What is CVE and CWE cyber security
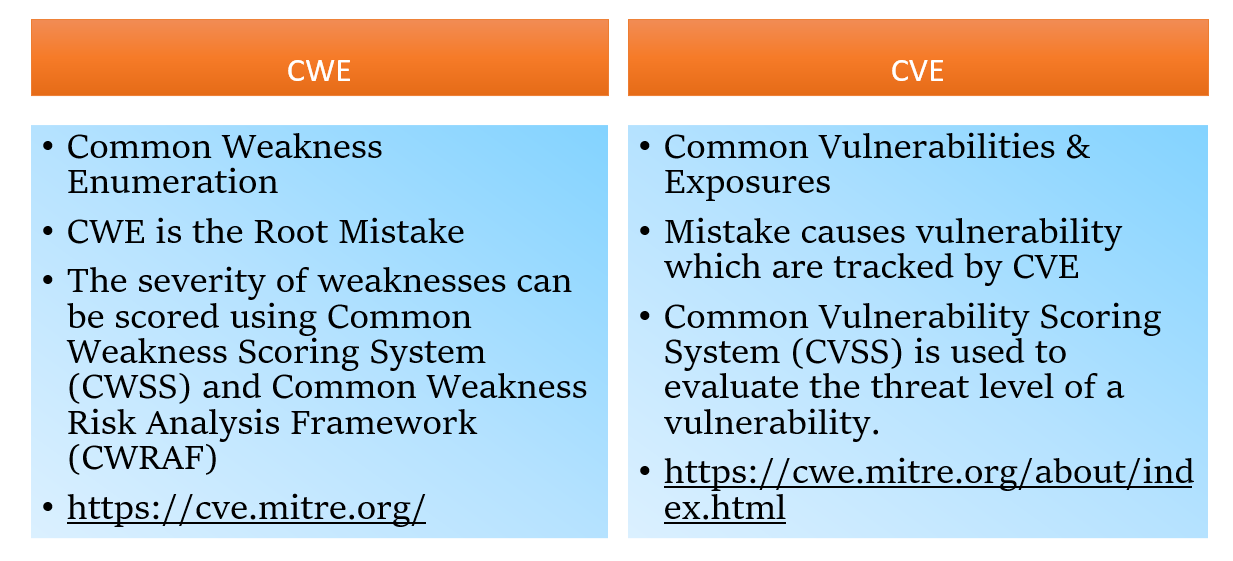
Here's the simple distinction: CWE stands for Common Weakness Enumeration, and has to do with the vulnerability—not the instance within a product or system. CVE stands for Common Vulnerabilities and Exposures, and has to do with the specific instance within a product or system—not the underlying flaw.
What is the difference between CWE and CVSS
Common Weakness Scoring System (CWSS) is a framework that documents software weaknesses so developers can minimize the number of bugs and vulnerabilities they introduce in a live system. The biggest difference between scoring systems is that the CWSS is proactive, whereas the CVSS is reactive.
What is the difference between vulnerability and CVE
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
What is the difference between CVSS and CVE
The CVE represents a summarized vulnerability, while the Common Vulnerability Scoring System (CVSS) assesses the vulnerability in detail and scores it, based on several factors.
What is the difference between CVE and CWE *
While both standards play a critical role in secure software development, they have different purposes. In summary, CVE is a standard for identifying and naming specific vulnerabilities, while CWE is a standard for classifying and describing the types of weaknesses that can lead to vulnerabilities.
What is CVE in cyber security
CVE, short for Common Vulnerabilities and Exposures, is a list of publicly disclosed computer security flaws. When someone refers to a CVE, they mean a security flaw that's been assigned a CVE ID number. Security advisories issued by vendors and researchers almost always mention at least one CVE ID.
What is Capec vs CVE
CVE lists common identifiers for known vulnerability information. CAPEC is a dictionary of common identifiers for attack patterns employed by adversaries to exploit weaknesses.
What is CVE vs CWE example
CVE stands for Common Vulnerabilities and Exposures. When you see CVE, it refers to a specific instance of a vulnerability within a product or system. For example, Microsoft Outlook Elevation of Privilege Vulnerability is CVE-2023-23397. CWE stands for Common Weakness Enumeration.
What is CCE vs CVE
CVE provides this capability for information security vulnerabilities, CCE assigns a unique, common identifier to a particular security-related configuration issue. The name of the imported file. The type of the list, that is, if it is a CVE or CCE list.
What is a CVE in cyber security
CVE, short for Common Vulnerabilities and Exposures, is a list of publicly disclosed computer security flaws. When someone refers to a CVE, they mean a security flaw that's been assigned a CVE ID number. Security advisories issued by vendors and researchers almost always mention at least one CVE ID.
What is a CVE example
Examples of CVEs
A classic example of a CVE is the recent Log4j vulnerability report (CVE-2021-44228). It contains detailed information about a vulnerability of the popular Java logging framework, Apache Log4j. Many service providers, like AWS, Cloudflare and Twitter, were affected by this vulnerability.
What is the purpose of CVE
CVE is designed to allow vulnerability databases and other tools to be linked together. It also facilitates comparisons between security tools and services. Check out the US National Vulnerability Database (NVD) that uses the CVE list identifiers and includes fix information, scoring and other information.
What is the difference between CWE and Capec
What is the relationship between CWE and CAPEC While CWE is a list of software and hardware weakness types, Common Attack Pattern Enumeration and Classification (CAPEC™) is a list of the most common methods attackers use to exploit these weaknesses.
What is CCE cybersecurity
Common Configuration Enumeration (CCE) provides unique identifiers to system configuration issues in order to facilitate fast and accurate correlation of configuration data across multiple information sources and tools.
Do hackers use CVE
Can Hackers Use CVE to Attack My Organization The short answer is yes but many cybersecurity professionals believe the benefits of CVE outweigh the risks: CVE is restricted to publicly known vulnerabilities and exposures.
Why are CWE and CVE important
Whereas the CVE logs real-world instances of vulnerabilities and exposures in specific products, the CWE lists and defines weaknesses commonly seen in digital products. The CWE does not refer to one particular example but provides definitions for widely seen defects.
What is the relationship between CVE and CWE
In other words, CVE is a list of known instances of vulnerability for specific products or systems, while CWE acts as a dictionary (so to speak) of software vulnerability types. The National Vulnerability Database (NVD) actually uses CWEs to score CVEs.
What is CAPEC vs CVE
CVE lists common identifiers for known vulnerability information. CAPEC is a dictionary of common identifiers for attack patterns employed by adversaries to exploit weaknesses.
What is CCE used for
CCE helps teachers to systematize their strategies for effective teaching. Continual evaluation allows the teacher to detect weaknesses and identify certain students' learning styles. By identifying a student's learning difficulties on a regular basis, it helps in improving student performance.
Do all vulnerabilities have a CVE
CVE stands for Common Vulnerabilities and Exposures. It is the database of publicly disclosed information on security issues. All organizations use CVEs to identify and track the number of vulnerabilities. But not all the vulnerabilities discovered have a CVE number.
Who creates a CVE for vulnerability
The Mitre Corporation
CVEs are assigned by a CVE Numbering Authority (CNA). While some vendors acted as a CNA before, the name and designation was not created until February 1, 2005. there are three primary types of CVE number assignments: The Mitre Corporation functions as Editor and Primary CNA.
What does CVE mean
common vulnerabilities and exposures
common vulnerabilities and exposures (CVE)
What is the full meaning of CCE in computer
Common Configuration Enumeration (CCE) is a standard that provides unique identifiers to system configuration issues to facilitate fast and accurate correlation of configuration data across multiple information sources and tools.
What is the full form of CCE
Continuous And Comprehensive Evaluation
CCE Stands for Continuous And Comprehensive Evaluation.
The Central Board of Secondary Education (CBSE) and the state governments of India together developed the Continuous and Complete Evaluation (CCE) system to continuously assess a student's development throughout the academic year.
What is a CVE in cybersecurity
Common Vulnerabilities and Exposures (CVE) is a catalog of known security threats. The catalog is sponsored by the United States Department of Homeland Security (DHS), and threats are divided into two categories: vulnerabilities and exposures.