What is a CWE vulnerability
The Common Weakness Enumeration (CWE) is a category system for hardware and software weaknesses and vulnerabilities. It is sustained by a community project with the goals of understanding flaws in software and hardware and creating automated tools that can be used to identify, fix, and prevent those flaws.
What is the difference between CVSS and CWSS
The key difference between CWSS and CVSS is that while CVSS is reactive, CWSS is a proactive approach to cybersecurity. CVSS stands for Common Vulnerability Scoring System, numerically scoring vulnerabilities based on risk. Vulnerabilities are security flaws that attackers can exploit to gain access to a system.
What is the difference between CWE and CVE
While both standards play a critical role in secure software development, they have different purposes. In summary, CVE is a standard for identifying and naming specific vulnerabilities, while CWE is a standard for classifying and describing the types of weaknesses that can lead to vulnerabilities.
What is CVE and CVSS
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
What is CVE and CWE cyber security
Here's the simple distinction: CWE stands for Common Weakness Enumeration, and has to do with the vulnerability—not the instance within a product or system. CVE stands for Common Vulnerabilities and Exposures, and has to do with the specific instance within a product or system—not the underlying flaw.
What is CVSS in security
The Common Vulnerability Scoring System (aka CVSS Scores) provides a numerical (0-10) representation of the severity of an information security vulnerability.
What is CWE in cybersecurity
Common Weakness Enumeration (CWE) is a universal online dictionary of weaknesses that have been found in computer software. The dictionary is maintained by the MITRE Corporation and can be accessed free on a worldwide basis.
What is CVSS and CCSS
The Common Configuration Scoring System (CCSS) is a set of measures of the severity of software security configuration issues. CCSS is derived from CVSS, which was developed to measure the severity of vulnerabilities due to software flaws.
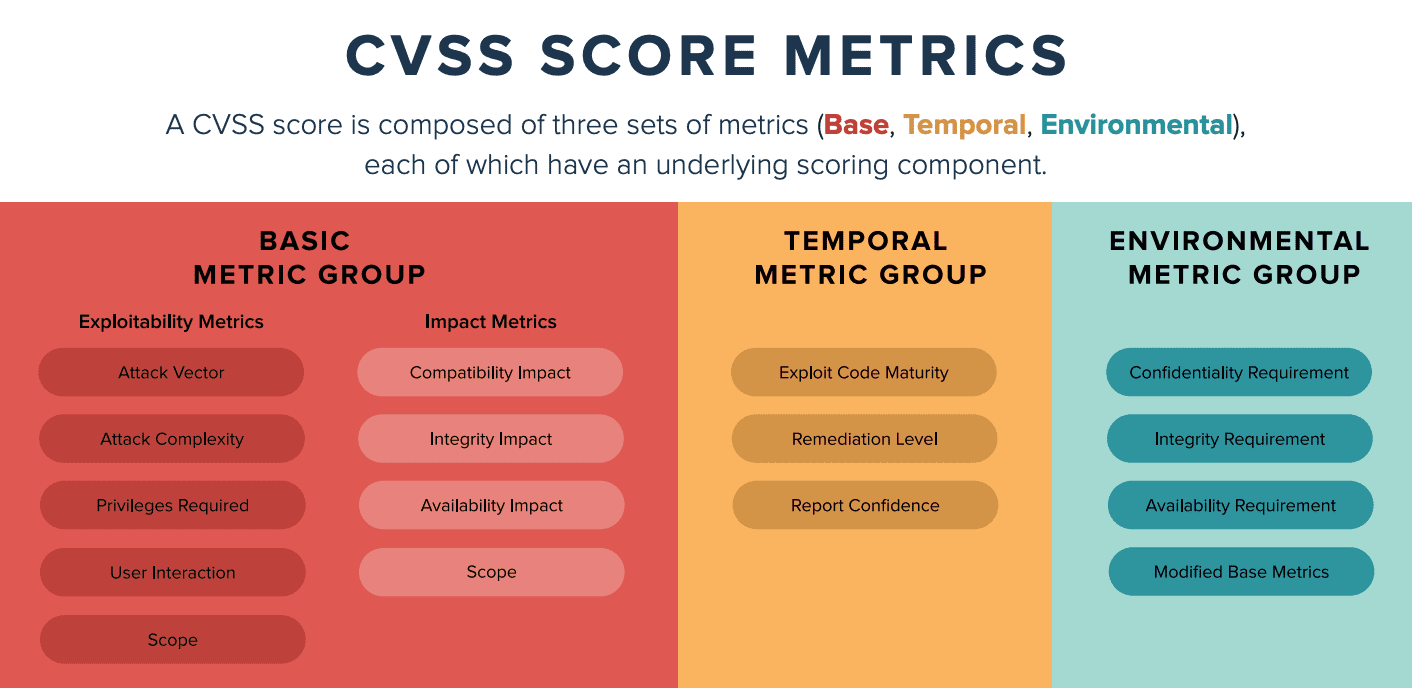
What does CVSS mean
The Common Vulnerability Scoring System (CVSS) provides a way to capture the principal characteristics of a vulnerability and produce a numerical score reflecting its severity.
What is CCE vs CVE
CVE provides this capability for information security vulnerabilities, CCE assigns a unique, common identifier to a particular security-related configuration issue. The name of the imported file. The type of the list, that is, if it is a CVE or CCE list.
What is CVSS score for vulnerability
NVD Vulnerability Severity Ratings
| CVSS v2.0 Ratings | CVSS v3.0 Ratings | |
|---|---|---|
| Severity | Base Score Range | Base Score Range |
| Low | 0.0-3.9 | 0.1-3.9 |
| Medium | 4.0-6.9 | 4.0-6.9 |
| High | 7.0-10.0 | 7.0-8.9 |
What is CVSS in cybersecurity
The Common Vulnerability Scoring System (CVSS) is a public framework for rating the severity of security vulnerabilities in software.
What is the difference between CWE and Owasp
OWASP: The Online Web Application Security Project curates the top 10 most dangerous vulnerabilities that affect web applications today. CWE: A list of the various weaknesses affecting software systems. It relies on the CVE and OWASP lists and focuses on building a unified language around security vulnerabilities.
What is CVSS a tool for
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard for assessing the severity of computer system security vulnerabilities. CVSS attempts to assign severity scores to vulnerabilities, allowing responders to prioritize responses and resources according to threat.
What is CVE and CWE in cyber security
In other words, CVE is a list of known instances of vulnerability for specific products or systems, while CWE acts as a dictionary (so to speak) of software vulnerability types. The National Vulnerability Database (NVD) actually uses CWEs to score CVEs.
What is CCE in cyber security
Common Configuration Enumeration (CCE) provides unique identifiers to system configuration issues in order to facilitate fast and accurate correlation of configuration data across multiple information sources and tools.
What is CVSS used for
The Common Vulnerability Scoring System (CVSS) is a free and open industry standard for assessing the severity of computer system security vulnerabilities.
Is CVSS a threat model
There are eight main methodologies you can use while threat modeling: STRIDE, PASTA, VAST, Trike, CVSS, Attack Trees, Security Cards, and hTMM. Each of these methodologies provides a different way to assess the threats facing your IT assets.
What is CWE used for
The Common Weakness Enumeration (CWE) is a list of weaknesses in software that can lead to security issues. While the CWE list is long, it is also prioritized by severity of risk, providing organizations and developers with a good idea about how to best secure applications.
What is CCE used for
CCE helps teachers to systematize their strategies for effective teaching. Continual evaluation allows the teacher to detect weaknesses and identify certain students' learning styles. By identifying a student's learning difficulties on a regular basis, it helps in improving student performance.
What are the 3 types of threat intelligence data
3 Types of Threat IntelligenceTactical intelligence.Operational intelligence.Strategic intelligence.
What is CCE process
Continuous and Comprehensive Evaluation (CCE) refers to a student evaluation system, which covers all aspects of activities related to student development. It emphasizes two-fold objectives such as continuity of evaluation and assessment of learning outcomes in a comprehensive manner.
What is the full meaning of CCE in computer
Common Configuration Enumeration (CCE) is a standard that provides unique identifiers to system configuration issues to facilitate fast and accurate correlation of configuration data across multiple information sources and tools.
What are the 4 types of threats to our data
Types of cyber threats your institution should be aware of include:Malware.Ransomware.Distributed denial of service (DDoS) attacks.Spam and Phishing.Corporate Account Takeover (CATO)Automated Teller Machine (ATM) Cash Out.
What are the three 3 categories of threats to security
The three most general categories are natural threats (such as earthquakes), physical security threats (such as power outages damaging equipment), and human threats (blackhat attackers who can be internal or external.)