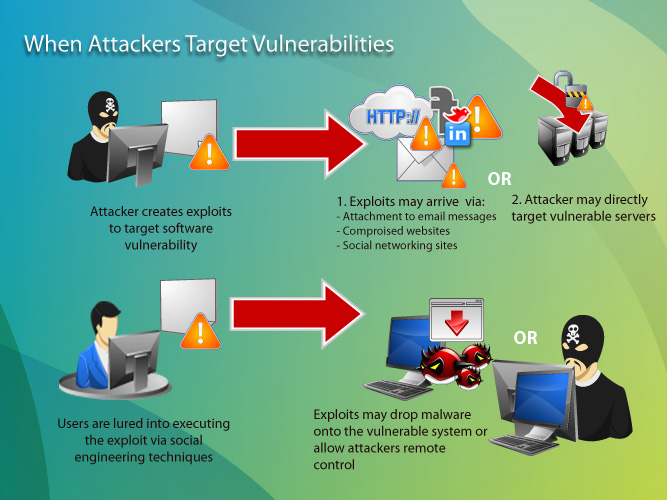
What is exploiting vulnerability
An exploit is a program, or piece of code, designed to find and take advantage of a security flaw or vulnerability in an application or computer system, typically for malicious purposes such as installing malware. An exploit is not malware itself, but rather it is a method used by cybercriminals to deliver malware.
What is a known vulnerability
Software that has been identified as unprotected and vulnerable to an attack. For example, bugs in Web server, Web browser and email client software are widely exploited for malicious purposes.
Which vulnerabilities were exploited
List of Top 10 Exploited VulnerabilitiesZeroLogon (CVE-2020-1472)Log4Shell (CVE-2021-44228)ICMAD (CVE-2022-22536)ProxyLogon (CVE-2021-26855)Spring4Shell (CVE-2022-22965)Atlassian Confluence RCE (CVE-2022-26134)VMware vSphere (CVE-2021-21972)Google Chrome Zero-Day (CVE-2022-0609)
What is a known exploit
Exploits are commonly classified as one of two types: known or unknown. Known exploits have already been discovered by cybersecurity researchers. Whether the known exploit is due to a vulnerability in the software, OS, or even hardware, developers can code patches to plug the hole.
Why exploit a vulnerability
An exploit is some malicious code used to take advantage of a vulnerability. Most exploits have a set of common goals: Steal private information from a system so that information can be sold. Slow down or completely stop a system from working, so a ransom can be demanded.
What does exploited mean in cyber security
Exploit Definition
An exploit (in its noun form) is a segment of code or a program that maliciously takes advantage of vulnerabilities or security flaws in software or hardware to infiltrate and initiate a denial-of-service (DoS) attack or install malware, such as spyware, ransomware, Trojan horses, worms, or viruses.
What is known and unknown vulnerability
The known knowns: Vulnerabilities that have been explicitly discovered through scanning and testing. The known unknowns: Newly created software that has yet to undergo any application security testing. The unknown unknowns: Systems that the defender does not know about.
What are the 4 main types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military. In relation to hazards and disasters, vulnerability is a concept that links the relationship that people have with their environment to social forces and institutions and the cultural values that sustain and contest them.
What is the CISA known exploited vulnerabilities catalog
Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog as a living list of known Common Vulnerabilities and Exposures (CVEs) that carry significant risk to the federal enterprise.
What is vulnerability vs exploitable vulnerability
A vulnerability is a gap in the armor or weakness that allows people to enter. The exploit is the mechanism that someone uses to get in. For example, a door with a fragile lock has a vulnerability. The exploit uses the keys, hammer, or lockpick to break the lock.
What are the 4 main types of security vulnerability
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
What is an example of exploited
Example Sentences
Top athletes are able to exploit their opponents' weaknesses. She said the tragedy had been exploited by the media.
How many vulnerabilities are actually exploited
In 2020, only 2.7% of security bugs appear to be exploitable and only roughly 0.4% of them have actually been exploited in attacks. According to Kenna, in terms of severity, 8.6% of the critical vulnerabilities disclosed this year are exploitable and 2.1% have been exploited in attacks.
What is an example of an exploit
Famous Examples of Exploits
A weak and out-of-date algorithm had caused a vulnerability, providing hackers with access to multiple email accounts. A recent infamous exploit named "EternalBlue" takes advantage of a flaw found in the Windows Server Message Block protocol.
How can cyber vulnerabilities be exploited
Internet Usage – The Internet is full of spyware and adware that can be installed automatically on computers. Software Bugs – Programmers can accidentally or deliberately leave an exploitable bug in software. Sometimes end users fail to update their software, leaving them unpatched and vulnerable to exploitation.
What are the 3 types of vulnerability
According to the different types of losses, the vulnerability can be defined as physical vulnerability, economic vulnerability, social vulnerability and environmental vulnerability.
What is zero-day vs known vulnerability
The threat of a Zero-Day Exploit
These attacks can take the form of polymorphic worms, viruses, Trojans, and other malware. When a vulnerability becomes public and researchers have discovered a solution or the vendor has deployed a patch, then it becomes a known or “n-day” vulnerability instead of a 'zero-day exploit.
What are the 5 categories of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What are 5 example of vulnerability
To illustrate the principles above, here are 11 specific examples of vulnerability: Telling someone when they've upset you, respectfully but honestly. Sharing something personal about yourself that you normally wouldn't. Admitting to mistakes you have made in the past.
Where to find cve exploits
For a full list of CVE databases, please visit our article Top 4 CVE databases.Exploit DB.Rapid7.CXSecurity.Vulnerability Lab.0day.SecurityFocus.Packet Storm Security.Google Hacking Database.
Is CVE a catalog of known security threats
Common Vulnerabilities and Exposures (CVE) is a catalog of known security threats. The catalog is sponsored by the United States Department of Homeland Security (DHS), and threats are divided into two categories: vulnerabilities and exposures.
What is an example of exploitable
able to be used unfairly, for someone's own advantage: The lack of jobs in this area means that the workforce is easily exploitable. He fixed a number of potentially exploitable security holes in the computer system. France's economically exploitable oil, gas, and coal reserves are small.
What is the difference between an exploit vulnerability and a payload
Exploits give you the ability to 'pop a shell/run your payload code'. Example payloads are things like Trojans/RATs, keyloggers, reverse shells etc. Payloads are only referred to when code execution is possible and not when using things like denial of service exploits.
Who exploits cyber vulnerabilities
Cybercriminals
Any flaw in an organization's internal controls, system procedures, or information systems is a vulnerability in cyber security. Cybercriminals and Hackers may target these vulnerabilities and exploit them through the points of vulnerability.
What is an example of exploit in information security
For example, an attacker could damage the confidentiality of a computer by installing malware on the computer, the integrity of a web page by injecting malicious code into the web browser, or availability by performing a distributed denial of service (DDoS) attack powered by a botnet of trojans.