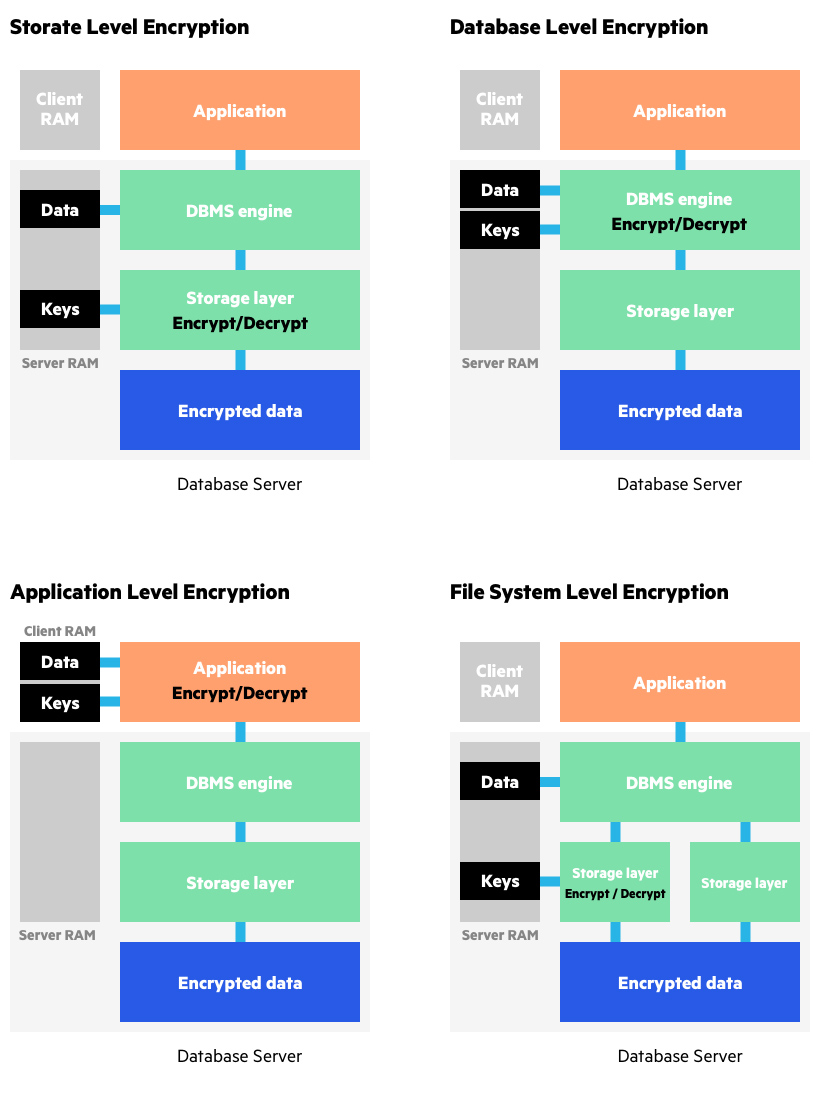
What is the highest encryption level
AES 256-bit encryption is the strongest and most robust encryption standard that is commercially available today. While it is theoretically true that AES 256-bit encryption is harder to crack than AES 128-bit encryption, AES 128-bit encryption has never been cracked.
What is level 3 encryption
Level 3: Adds requirements for physical tamper-resistance and identity-based authentication. There must also be physical or logical separation between the interfaces by which “critical security parameters” enter and leave the module. Private keys can only enter or leave in encrypted form.
What is the level of encryption
Modern AES encryption uses 128, 192 or 256-bit keys. As we might expect, the higher the number of bits in the key, the more possible key combinations there are and therefore the harder the code is to crack.
What are the 4 objectives of encryption
The Objectives of Cryptography
Cryptography has four major goals: confidentiality, integrity, authentication, and non-repudiation.
Has AES-256 been cracked
In the end, AES has never been cracked yet and is safe against any brute force attacks contrary to belief and arguments.
Who can crack 256-bit encryption
256-bit encryption is refers to the length of the encryption key used to encrypt a data stream or file. A hacker or cracker will require 2256 different combinations to break a 256-bit encrypted message, which is virtually impossible to be broken by even the fastest computers.
What is Type 5 encryption
Type 5. Type 5 use a Cisco proprietary encryption algorithm that makes use of the MD5 hashing algorithm. They are considered to be irreversible. The only way to crack type 5 passwords is by performing brute force attacks.
What is Type 7 encryption
Cisco type 7 password
This password type uses Vigenère cipher which is essentially a simple alphabetical substitution encryption. The algorithm is reversible and thus it can be deciphered instantly into a plain text without any need for cracking.
What are the four 4 most secure encryption techniques
11. What are the 4 basic types of encryption systemsAdvanced Encryption Standard (AES)Triple DES.Blowfish.Rivest-Shamir-Adleman (RSA)
What are the 5 stages of encryption
The encryption process step (step 4, above) is further broken down into five stages:Key transformation.Expansion permutation.S-Box permutation.P-Box permutation.XOR and swap.
Can FBI crack AES 256
AES Encryption is very strong and widely considered uncrackable by the government or anyone else with today's computational resources. Here are some key points about AES and government capabilities: AES is a symmetric encryption algorithm approved by the U.S. government to protect classified information.
Can hackers break AES 256
AES-256 is unbreakable by brute force
It is the strongest encryption and is almost impossible to break. A brute force attack is when a hacker checks different key combinations until he/she arrives at the correct combination. The larger the key size, the more difficult it becomes to break the encryption.
Can 1024 bit encryption be broken
Trapdoored primes allow an attacker to efficiently break certain 1024-bit keys to decrypt communications and cryptographically impersonate key owners to sign data, all unbeknownst to the victim.
What are the 4 basic types of encryption systems
11. What are the 4 basic types of encryption systemsAdvanced Encryption Standard (AES)Triple DES.Blowfish.Rivest-Shamir-Adleman (RSA)
What is Type 9 password
Type 9 is designed to make it difficult to crack the password since it requires a significant amount of hardware resources to do so, raising the cost for an adversary to brute force. The passwords are stored as hashes within the configuration file. Cisco and industry recommend Type 9 hashes.
What are the 3 types of encryption
3 Types of Encryption to Protect Your DataSymmetric. The symmetric encryption method uses a single key both to encrypt and decrypt the data.Asymmetric. The second major encryption method is asymmetric encryption, also sometimes known as public key encryption.Hashing.
What is 128 AES encryption
AES-128 uses a 128-bit key length to encrypt and decrypt a block of messages. AES-192 uses a 192-bit key length to encrypt and decrypt a block of messages. AES-256 uses a 256-bit key length to encrypt and decrypt a block of messages.
What are the three 3 types of modern encryption
The various encryption types. The three major encryption types are DES, AES, and RSA. While there are many kinds of encryption – more than can easily be explained here – we will take a look at these three significant types of encryption that consumers use every day.
Has AES 256 been hacked
The difference between cracking the AES-128 algorithm and AES-256 algorithm is considered minimal. Whatever breakthrough might crack 128-bit will probably also crack 256-bit. In the end, AES has never been cracked yet and is safe against any brute force attacks contrary to belief and arguments.
Will AES 256 ever be broken
However, while this seems significant, it doesn't break either algorithm. With the right quantum computer, AES-128 would take about 2.61*10^12 years to crack, while AES-256 would take 2.29*10^32 years.
Has AES-128 been hacked
A machine that can crack a DES key in a second would take 149 trillion years to crack a 128-bit AES key. Hence, it is safe to say that AES-128 encryption is safe against brute-force attacks. AES has never been cracked yet and it would take large amounts of computational power to crack this key.
Has AES 256 been cracked
In the end, AES has never been cracked yet and is safe against any brute force attacks contrary to belief and arguments.
What are the four 3 most secured encryption techniques
11. What are the 4 basic types of encryption systemsAdvanced Encryption Standard (AES)Triple DES.Blowfish.Rivest-Shamir-Adleman (RSA)
What are Type 7 passwords
Cisco type 7 password
This password type uses Vigenère cipher which is essentially a simple alphabetical substitution encryption. The algorithm is reversible and thus it can be deciphered instantly into a plain text without any need for cracking.
What is 3D password
The 3D password is simply the combination and the sequence of user interactions that occur in the 3D virtual environment. The 3D password can combine recognition, recall, token, and biometrics based systems into one authentication scheme.