What is vulnerable in Log4Shell
What's the risk from the Log4Shell vulnerability in the Log4j 2 library Log4Shell is considered a zero-day vulnerability because malicious actors likely knew about and exploited it before experts did. What makes the log4j vulnerability so dangerous is how ubiquitous the Log4j 2 library is.
What is the vulnerability of Log4j shell
Log4Shell (CVE-2021-44228, CVE-2021-45046 and CVE-2021-45105) is a remote code execution (RCE) vulnerability that enables malicious actors to execute arbitrary Java code, taking control of a target server.
What is the impact of Log4Shell vulnerability
Log4Shell is a critical vulnerability, and can allow attackers to execute malicious code remotely to a target. If exploited, impact can range from theft of data, installation of malware, and full takeover of the system.
What is Log4Shell and why are we panicking about it
Log4Shell is one of the most serious Java vulnerabilities discovered to date. In addition to tapping sensitive data, the vulnerability can be exploited to open reverse shells on remote systems. If a reverse shell exists, attackers can insert further malicious code or take over the system completely.
Is Log4Shell a zero day vulnerability
“Log4Shell” or “LogJam” (CVE-2021-44228) is a critical zero-day vulnerability to the Apache Log4j Java-based, open-source logging library. The Log4j library is used in enterprise software and web applications, including products from Apple, Amazon, Cloudflare, Twitter, and Steam, among many others.
Are Log4Shell and Log4j the same
The original Apache Log4j vulnerability (CVE-2021-44228), also known as Log4Shell, is a cybersecurity vulnerability on the Apache Log4j 2 Java library. This security flaw is a Remote Code Execution vulnerability (RCE) – one of the most critical security exposures.
What damage can Log4j do
If left unfixed, attackers can break into systems, steal passwords and logins, extract data, and infect networks with malicious software. Log4j is used worldwide across software applications and online services, and the vulnerability requires very little expertise to exploit.
Why is Log4j so serious
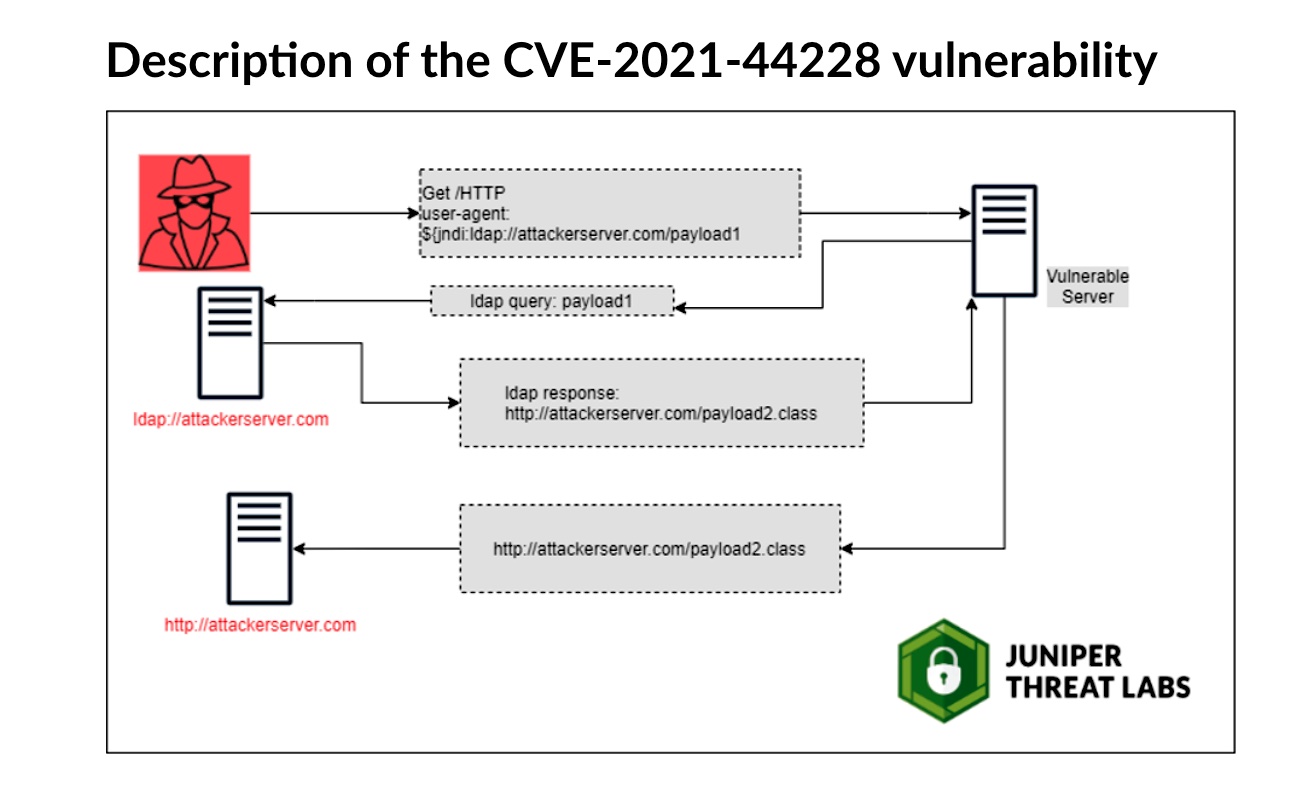
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
What products are affected by Log4Shell
F-Secure. On both Windows and Linux, Log4Shell affects several F-Secure products, including Policy Manager (only the Policy Manager Server component), Policy Manager Proxy, Endpoint Proxy, and Elements Connector.
What companies are hacked by Log4Shell
Log4Shell is different. By targeting the logging systems that countless developers have relied on, it has a much larger attack surface and compromised millions of vulnerable Java applications and services worldwide, including Cloudflare, iCloud, Minecraft servers, Steam, TencentQQ, and Twitter.
Who is affected by Log4Shell
Affected commercial services include Amazon Web Services, Cloudflare, iCloud, Minecraft: Java Edition, Steam, Tencent QQ and many others.
Is Log4Shell still a threat
According to a recent story we published, it's still one of the biggest vulnerabilities, 18 months after it initially appeared. How serious is the threat of Log4Shell in 2023 Log4Shell continues to haunt us. The exploitation of a vulnerability in logging software Log4j caused quite a stir in late 2021.
What is Log4j and why is it bad
Log4j is used to log messages within software and has the ability to communicate with other services on a system. This communication functionality is where the vulnerability exists, providing an opening for an attacker to inject malicious code into the logs so it can be executed on the system.
Who is at risk for Log4j
What Specific Devices are at Risk According to ZDNet, “Any device that's exposed to the internet is at risk if it's running Apache Log4J, versions 2.0 to 2.14. 1." This affects both IT and Operational Technology (OT) networks.
How does Log4j affect me
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
What is the root cause of Log4Shell
The root cause of this vulnerability is the way log4j processes log messages. Generally, software developers use a log mechanism to report on different flows within the software. During this process, a log message is passed as a string to be recorded in a log file.
What happens if I delete Log4j
Removing the Log4j related files does not affect further backup or recovery operations. BDRSuite has also developed a utility that identifies the log4j vulnerability in its installation location then removes the vulnerable file.
Is Log4j still a threat
Log4j remains a threat in 2023
The highest concentration of critical findings linked to Log4j were found within the first 48 hours of the vulnerability becoming known. At the time, findings often originated in the core of an application and later findings migrated to the dependences those applications rely on.
Who has been hacked by Log4j
Over a hundred vendors confirmed to be affected including: Microsoft, Amazon Web Services, Netflix and Oracle, and experts say that the flaw has gone unnoticed since 2013.
How bad is the Log4j vulnerability
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
Why is Log4j on my computer
Log4j is used by developers to keep track of what happens in their software applications or online services. It's basically a huge journal of the activity of a system or application. This activity is called 'logging' and it's used by developers to keep an eye out for problems for users.
Is Log4j safe to use now
The widespread vulnerability that first appeared in Apache Log4j in 2021 will continue to be exploited, potentially even in worse ways than we've seen to date. The more worrisome aspect of these threats is that there's a good chance they'll continue to be exploited months or years into the future.
Why was Log4j so bad
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
Is Log4j vulnerability bad
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
Is Windows 10 affected by Log4j
Natively, Windows is not vulnerable to the Log4j exploit, so don't look for evidence of the attack in your Windows event logs. Rather, look for this in applications that you have purchased or developed as that's typically where Log4j logging routines are located.