What is MITRE in cyber
The MITRE ATT&CK framework is a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary's attack lifecycle and the platforms they are known to target.
What is MITRE What is it used for
Organizations can use MITRE ATT&CK to develop threat models, evaluate security tool efficacy, develop detection strategies and prioritize security investments. Additionally, it can be used to share threat and defense information between organizations.
What is the Mitre attack
The MITRE ATTACK Framework is a curated knowledge base that tracks cyber adversary tactics and techniques used by threat actors across the entire attack lifecycle.
What is the difference between NIST and MITRE
One key difference between MITRE ATT&CK and NIST is their level of granularity. MITRE ATT&CK is highly detailed and provides a comprehensive taxonomy of adversary tactics and techniques, while NIST takes a more high-level approach, providing guidelines for managing cybersecurity risks across the entire organization.
What is MITRE CVE
Common Vulnerabilities and Exposures (CVE) is a list of publicly disclosed information security vulnerabilities and exposures. CVE was launched in 1999 by the MITRE corporation to identify and categorize vulnerabilities in software and firmware.
Why is it called MITRE
Etymology. From Middle English mytre, from Old French mitre, from Ancient Greek μίτρα (mítra, “headband, turban”). Its use in reference to a counterfeit coin derived from the bishop's mitre stamped upon it.
Is mitre a threat model
The MITRE ATTACK framework is a “globally-accessible knowledge base of adversary tactics and techniques based on real-world observations” (MITRE) used for threat modeling language.
Why is it called mitre
Etymology. From Middle English mytre, from Old French mitre, from Ancient Greek μίτρα (mítra, “headband, turban”). Its use in reference to a counterfeit coin derived from the bishop's mitre stamped upon it.
What is MITRE vulnerability
Common Vulnerabilities and Exposures (CVE) is a list of publicly disclosed information security vulnerabilities and exposures. CVE was launched in 1999 by the MITRE corporation to identify and categorize vulnerabilities in software and firmware.
Why is IT called MITRE
Etymology. From Middle English mytre, from Old French mitre, from Ancient Greek μίτρα (mítra, “headband, turban”). Its use in reference to a counterfeit coin derived from the bishop's mitre stamped upon it.
Is MITRE a threat model
The MITRE ATTACK framework is a “globally-accessible knowledge base of adversary tactics and techniques based on real-world observations” (MITRE) used for threat modeling language.
What is MITRE vs CIS
CIS (Center for Internet Security) controls are a set of best practices for securing IT systems and data, while MITRE ATT&CK is a framework for understanding and identifying cyber threats. While both are important tools for improving cyber security, they serve different purposes and are not directly comparable.
Does MITRE own CVE
The CVE program is overseen by the MITRE corporation with funding from the Cybersecurity and Infrastructure Security Agency (CISA), part of the U.S. Department of Homeland Security.
Did MITRE create CVE
The CVE List was launched by the MITRE Corporation as a community effort in 1999. The U.S. National Vulnerability Database (NVD) was launched by the National Institute of Standards and Technology (NIST) in 2005.
What is called mitre
mitre, also spelled miter, liturgical headdress worn by Roman Catholic bishops and abbots and some Anglican and Lutheran bishops. It has two shield-shaped stiffened halves that face the front and back. Two fringed streamers, known as lappets, hang from the back.
What is the mitre technique called
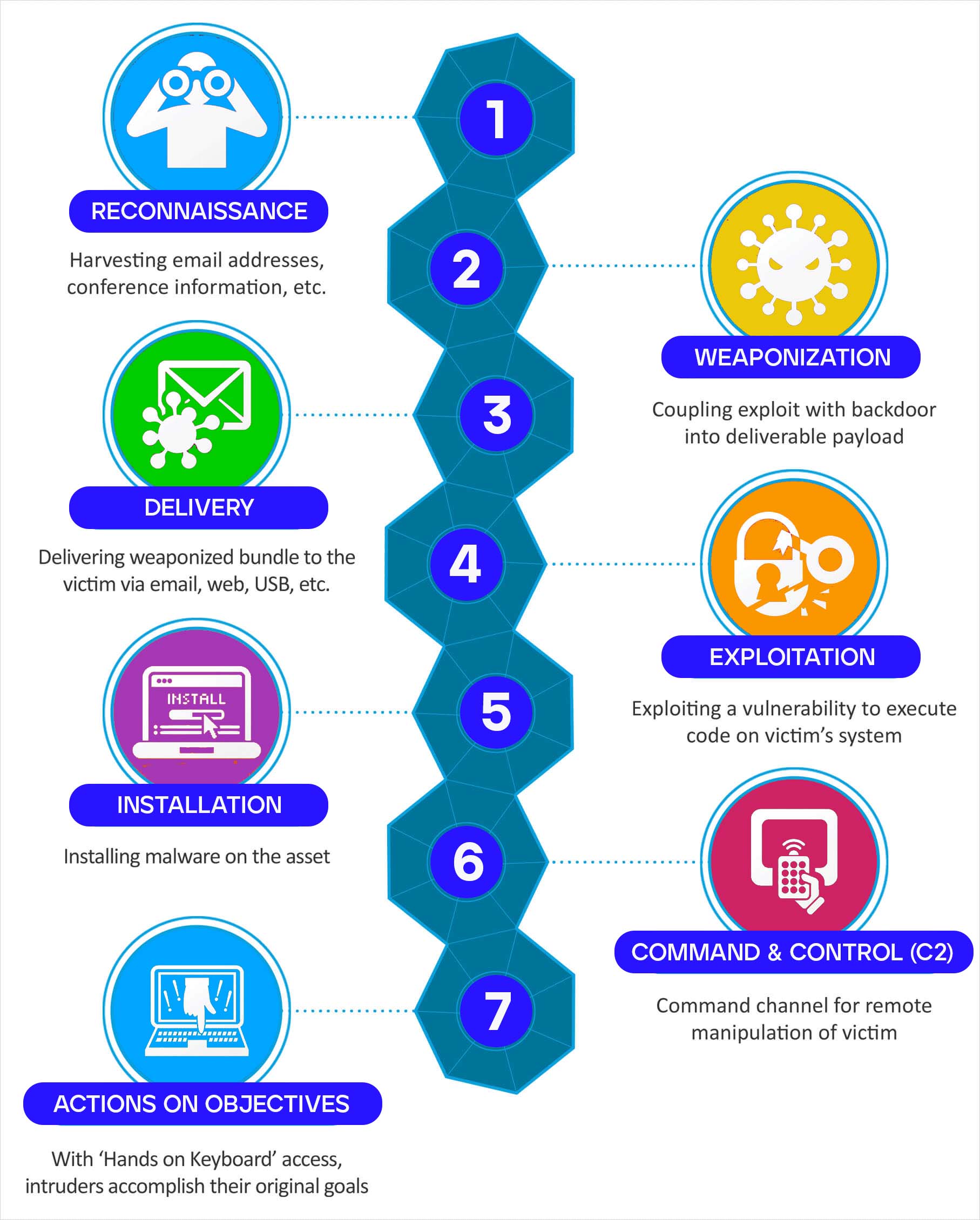
The MITRE ATT&CK Matrix for Enterprise [1] consists of 14 tactics: Reconnaissance, Resource Development, Initial Access, Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, Discovery, Lateral Movement, Collection, Command and Control, Exfiltration, and Impact.
What is MITRE Cyber operations and effects
The Cyber Operations and Effects Innovation Center provides solutions and expertise performing defensive cyber operations, enabling offensive objectives, and conducting adversary emulation.
Is MITRE related to MIT
First: MITRE is NOT associated with MIT (Massachusetts Institute of Technology), although it is a spin-off of MIT, or more accurately, of Lincoln Labs which is part of MIT.
What is MITRE CVE database
The mission of the CVE® Program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities.
Why is it called a miter
And they made this nice neat little Union somehow. It got equated to joining similar pieces of wood together. And that joint voila became the miter joint. And today we have miter saw and now you know.
Why is it called Mitre
Etymology. From Middle English mytre, from Old French mitre, from Ancient Greek μίτρα (mítra, “headband, turban”). Its use in reference to a counterfeit coin derived from the bishop's mitre stamped upon it.
Is Mitre Att&ck a threat model
Security teams use threat modeling, a key method to proactively remediating vulnerabilities and detecting active threats, to understand their adversaries' potential techniques, tactics, and processes (TTPs). The most popular threat modeling framework today is called the MITRE ATT&CK framework.
What are MITRE technology domains
To date MITRE has defined three technology domains – Enterprise (representing traditional enterprise networks and cloud technologies), Mobile (for mobile communication devices), and ICS (for industrial control systems).
Is MIT part of Harvard
Eventually, the MIT Corporation approved a formal agreement to merge with Harvard, over the vehement objections of MIT faculty, students, and alumni. However, a 1917 decision by the Massachusetts Supreme Judicial Court effectively put an end to the merger scheme.
What is MITRE security
The MITRE ATT&CK® framework is a knowledge base of tactics and techniques designed for threat hunters, defenders and red teams to help classify attacks, identify attack attribution and objectives, and assess an organization's risk.