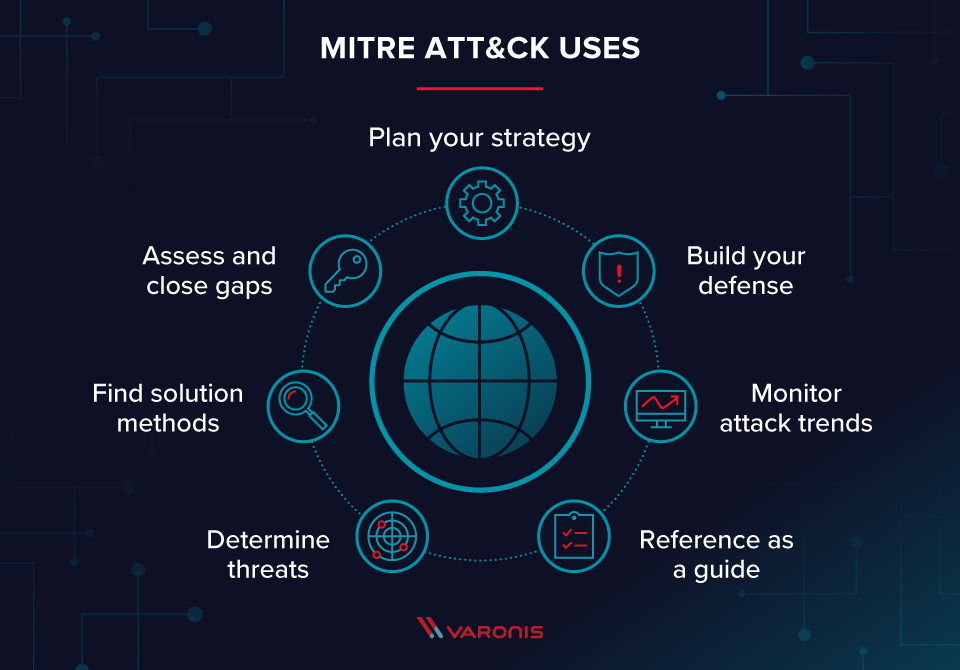
What is MITRE used for
The MITRE ATT&CK® framework is a knowledge base of tactics and techniques designed for threat hunters, defenders and red teams to help classify attacks, identify attack attribution and objectives, and assess an organization's risk.
What is MITRE technology
ATT&CK Technologies
The MITRE ATT&CK Framework is not a technology or software application, but rather a knowledge base and framework that describes these tactics, techniques, and procedures (TTPs)used by threat actors to carry out attacks.
Why was MITRE created
MITRE began in 1958, sponsored by the U.S. Air Force to bridge across the academic research community and industry to architect the Semi-Automatic Ground Environment , or SAGE, a key component of Cold War-era air defense.
What is MITRE in cyber security
MITRE draws from a wealth of deep technical expertise to create innovative solutions that address the ever-evolving challenges in cybersecurity. We advocate a multi-faceted, interactive approach—which, in turn, broadens our impact through the power of collaboration.
How does mitre framework work
The MITRE ATT&CK Framework catalogs information that correlates adversary groups to campaigns, so security teams can better understand the adversaries they are dealing with, evaluate their defenses, and strengthen security where it matters most.
Why is it called mitre
Etymology. From Middle English mytre, from Old French mitre, from Ancient Greek μίτρα (mítra, “headband, turban”). Its use in reference to a counterfeit coin derived from the bishop's mitre stamped upon it.
Why do we use MITRE Att&ck
Security platform developers and engineers use MITRE ATT&CK as a tool to evaluate the effectiveness of their products, uncover previously unknown weaknesses, and model how their products will behave during the lifecycle of a cyberattack.
Why is IT called MITRE
Etymology. From Middle English mytre, from Old French mitre, from Ancient Greek μίτρα (mítra, “headband, turban”). Its use in reference to a counterfeit coin derived from the bishop's mitre stamped upon it.
Why is it called MITRE
Etymology. From Middle English mytre, from Old French mitre, from Ancient Greek μίτρα (mítra, “headband, turban”). Its use in reference to a counterfeit coin derived from the bishop's mitre stamped upon it.
What is called MITRE
mitre, also spelled miter, liturgical headdress worn by Roman Catholic bishops and abbots and some Anglican and Lutheran bishops. It has two shield-shaped stiffened halves that face the front and back. Two fringed streamers, known as lappets, hang from the back.
What is MITRE vulnerability
Common Vulnerabilities and Exposures (CVE) is a list of publicly disclosed information security vulnerabilities and exposures. CVE was launched in 1999 by the MITRE corporation to identify and categorize vulnerabilities in software and firmware.
Is MITRE a threat model
The MITRE ATTACK framework is a “globally-accessible knowledge base of adversary tactics and techniques based on real-world observations” (MITRE) used for threat modeling language.
How many techniques are there in MITRE
There are currently 185 techniques and 367 sub-techniques in the Enterprise ATT&CK matrix, and Mitre continuously adds more. Each technique has a four-digit code—for example, Abuse Elevation Control Mechanism is T1548.
What is mitre in architecture
A mitre joint is an angle joint. An example is a joint that is formed when two pieces meet on a 90-degree angle and each piece has been cut at an angle of 45 degrees to be joined.
What is a mitre in building
A mitre joint (often miter in American English) is a joint made by cutting each of two parts to be joined, across the main surface, usually at a 45° angle, to form a corner, usually to form a 90° angle, though it can comprise any angle greater than 0 degrees.
Why is it called a mitre
Etymology. From Middle English mytre, from Old French mitre, from Ancient Greek μίτρα (mítra, “headband, turban”). Its use in reference to a counterfeit coin derived from the bishop's mitre stamped upon it.
How does MITRE framework work
The MITRE ATT&CK Framework catalogs information that correlates adversary groups to campaigns, so security teams can better understand the adversaries they are dealing with, evaluate their defenses, and strengthen security where it matters most.
What is MITRE Cyber operations and effects
The Cyber Operations and Effects Innovation Center provides solutions and expertise performing defensive cyber operations, enabling offensive objectives, and conducting adversary emulation.
What are the top 10 techniques MITRE
The MITRE ATT&CK framework categorizes attacker behavior into 12 tactics in its Windows Matrix for Enterprise, including Initial Access, Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, Discovery, Lateral Movement, Collection, Command and Control, Exfiltration, and Impact.
Why is it called a miter
And they made this nice neat little Union somehow. It got equated to joining similar pieces of wood together. And that joint voila became the miter joint. And today we have miter saw and now you know.
What is the difference between miter and mitre
Miter and mitre are both English terms. Miter is predominantly used in 🇺🇸 American (US) English ( en-US ) while mitre is predominantly used in 🇬🇧 British English (used in UK/AU/NZ) ( en-GB ). In the United States, there is a preference for "miter" over "mitre" (78 to 22).
How does Mitre framework work
The MITRE ATT&CK Framework catalogs information that correlates adversary groups to campaigns, so security teams can better understand the adversaries they are dealing with, evaluate their defenses, and strengthen security where it matters most.
How many techniques are there in Mitre
There are currently 185 techniques and 367 sub-techniques in the Enterprise ATT&CK matrix, and Mitre continuously adds more. Each technique has a four-digit code—for example, Abuse Elevation Control Mechanism is T1548.
What is miter in design
Article Talk. A mitre joint (often miter in American English) is a joint made by cutting each of two parts to be joined, across the main surface, usually at a 45° angle, to form a corner, usually to form a 90° angle, though it can comprise any angle greater than 0 degrees.
What are the top 10 techniques Mitre
The MITRE ATT&CK framework categorizes attacker behavior into 12 tactics in its Windows Matrix for Enterprise, including Initial Access, Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, Discovery, Lateral Movement, Collection, Command and Control, Exfiltration, and Impact.