What is NIST risk management framework
The Risk Management Framework (RMF), presented in NIST SP 800-37, provides a disciplined and structured process that integrates information security and risk management activities into the system development life cycle.
What is the NIST definition of cybersecurity risk
Cybersecurity risks relate to the loss of confidentiality, integrity, or availability of information, data, or information (or control) systems and reflect the potential adverse impacts to organizational operations (i.e., mission, functions, image, or reputation) and assets, individuals, other organizations, and the …
What does the NIST stand for
National Institute of Standards and Technology
National Institute of Standards and Technology (NIST)
What are the 3 tiers of the NIST Risk Management Framework
The NIST SP 800-39 lists three tiers at which risk management should be addressed:organizational tier,business process tier;information systems tier.
What are the 5 components of NIST framework
Here, we'll dive into the Framework Core and the five core functions: Identify, Protect, Detect, Respond, and Recover. NIST defines the framework core on its official website as a set of cybersecurity activities, desired outcomes, and applicable informative references common across critical infrastructure sectors.
Why is NIST the best framework
Superior and Unbiased Cybersecurity
As discussed earlier, the NIST CSF is a voluntary approach that represents the collective experience of thousands of information security professionals. It is widely recognized as an industry best practice and the most comprehensive, in-depth set of framework controls.
What are the 5 areas of the NIST cybersecurity framework
Here, we'll dive into the Framework Core and the five core functions: Identify, Protect, Detect, Respond, and Recover. NIST defines the framework core on its official website as a set of cybersecurity activities, desired outcomes, and applicable informative references common across critical infrastructure sectors.
What are the 5 pillars of NIST
The cybersecurity framework's five pillars follow.Identify. This pillar involves identifying an organization's so-called critical functions and what cybersecurity risks could impede those functions.Protect. This function focuses on containing a cybersecurity breach's potential impact.Detect.Respond.Recover.
What are examples of NIST
According to NIST, examples of outcome Categories within this Function include Identity Management and Access Control, Awareness and Training, Data Security, Information Security Protection Processes and Procedures, Maintenance, and Protective Technology.
What are the 4 elements of NIST Framework Core
Framework core
The core is “a set of activities to achieve specific cybersecurity outcomes, and references examples of guidance to achieve those outcomes.” It is further broken down into four elements: Functions, categories, subcategories and informative references.
What are the 5 domains of NIST
NIST framework is divided into 5 main functions. These functions are as follows: identity, protect, detect, respond, and recover. They support an organization in expressing its management of cybersecurity risk by addressing threats and developing by learning from past activities.
What are the 4 stages of NIST
The NIST incident response lifecyclePhase 1: Preparation.Phase 2: Detection and Analysis.Phase 3: Containment, Eradication, and Recovery.Phase 4: Post-Event Activity.
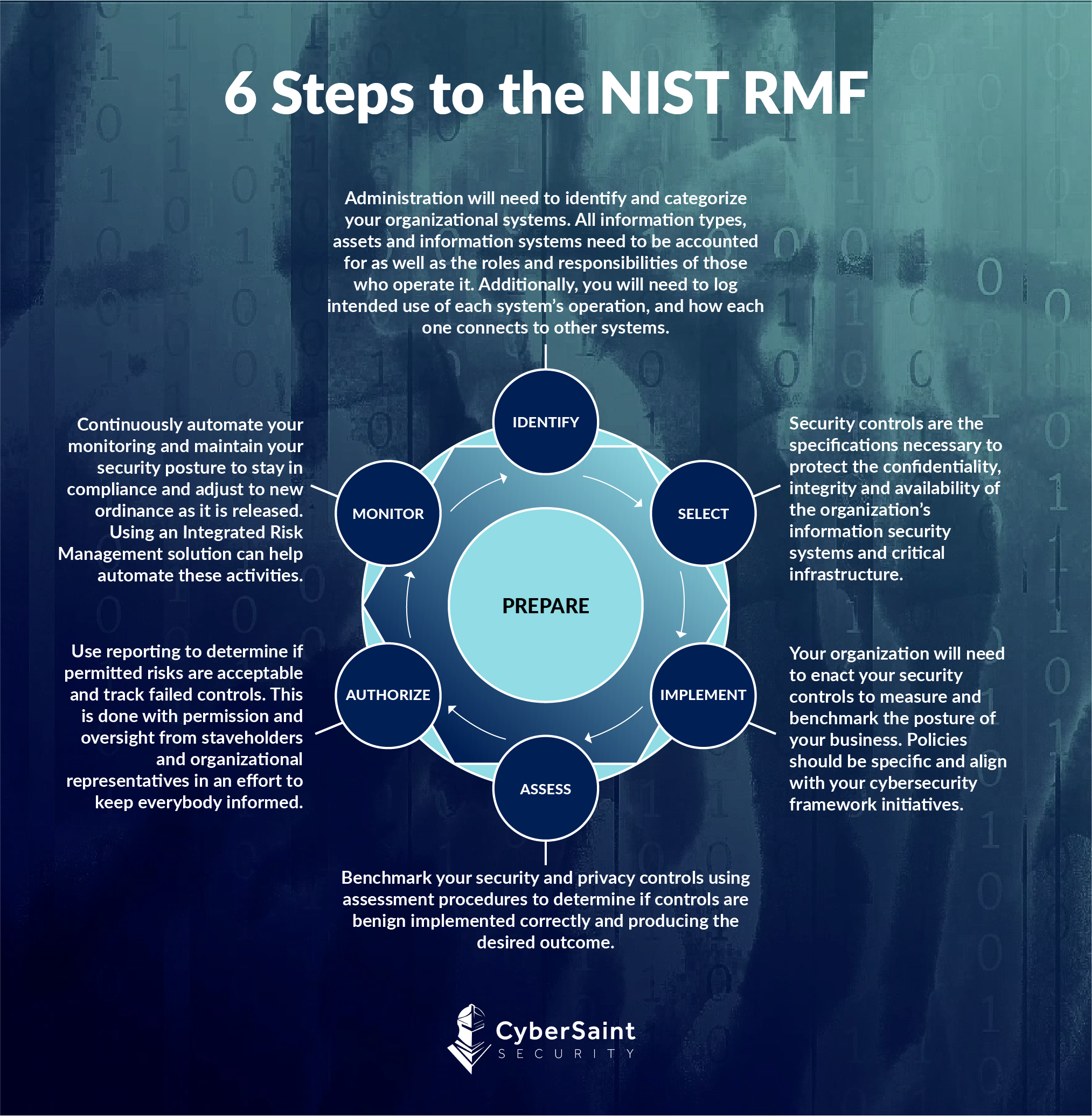
What are the 6 phases of NIST
The NIST management framework is a culmination of multiple special publications (SP) produced by the National Institute for Standards and Technology (NIST) – as we'll see below, the 6 NIST RMF Steps; Step 1: Categorize/ Identify, Step 2: Select, Step 3: Implement, Step 4: Assess, Step 5: Authorize and Step 6: Monitor, …
Is NIST better than ISO
Operational stage and technical level: ISO 27001 is less technical, with more emphasis on risk-based management and organizations that have reached operational maturity. NIST CSF is more technical and best suited for the initial stages of a cybersecurity risk program or when attempting to mitigate a breach.
Why do we need NIST framework
The Framework helps guide key decision points about risk management activities through the various levels of an organization from senior executives, to business and process level, and implementation and operations as well.
What are the NIST risk domains
The five domains in the NIST framework are the pillars support the creation of a holistic and successful cybersecurity plan. They include identify, protect, detect, respond, and recover.
What are the 5 standards of NIST
You can put the NIST Cybersecurity Framework to work in your business in these five areas: Identify, Protect, Detect, Respond, and Recover.
What are the 5 components of NIST
Although The 5 NIST functions, namely Protect, Identify, Detect, Respond, and Recover are similar to other top security frameworks, they contain a number of critical procedures that help minimize the effect of cybersecurity incidents on organizations of any size.
Is NIST equivalent to ISO 17025
The NIST Quality System for Measurement Services is based on the ISO/IEC 17025 (General requirements for the competence of testing and calibration laboratories) and includes the requirements of ISO 17034 (General requirements for the competence of reference material producers), ISO/IEC 17043 (General requirements for …
Is ISO 27001 based on NIST
ISO 27001 is a set of security standards and protocols, much like NIST. But ISO 27001 was developed by the International Organization of Standardization. This ISO database security framework is commonly used worldwide as the gold standard for security best practices.
Why is ISO better than NIST
Operational stage and technical level: ISO 27001 is less technical, with more emphasis on risk-based management and organizations that have reached operational maturity. NIST CSF is more technical and best suited for the initial stages of a cybersecurity risk program or when attempting to mitigate a breach.
Who needs NIST
NIST Special Publication 800-171 Rev.
All organizations that work with a federal agency must follow the NIST SP 800-171 requirements in order to be considered for government contracts.
What are the 5 NIST categories
NIST framework is divided into 5 main functions. These functions are as follows: identity, protect, detect, respond, and recover. They support an organization in expressing its management of cybersecurity risk by addressing threats and developing by learning from past activities.
What are the 4 elements of NIST framework Core
Framework core
The core is “a set of activities to achieve specific cybersecurity outcomes, and references examples of guidance to achieve those outcomes.” It is further broken down into four elements: Functions, categories, subcategories and informative references.
How is NIST different from ISO
Operational stage and technical level: ISO 27001 is less technical, with more emphasis on risk-based management and organizations that have reached operational maturity. NIST CSF is more technical and best suited for the initial stages of a cybersecurity risk program or when attempting to mitigate a breach.