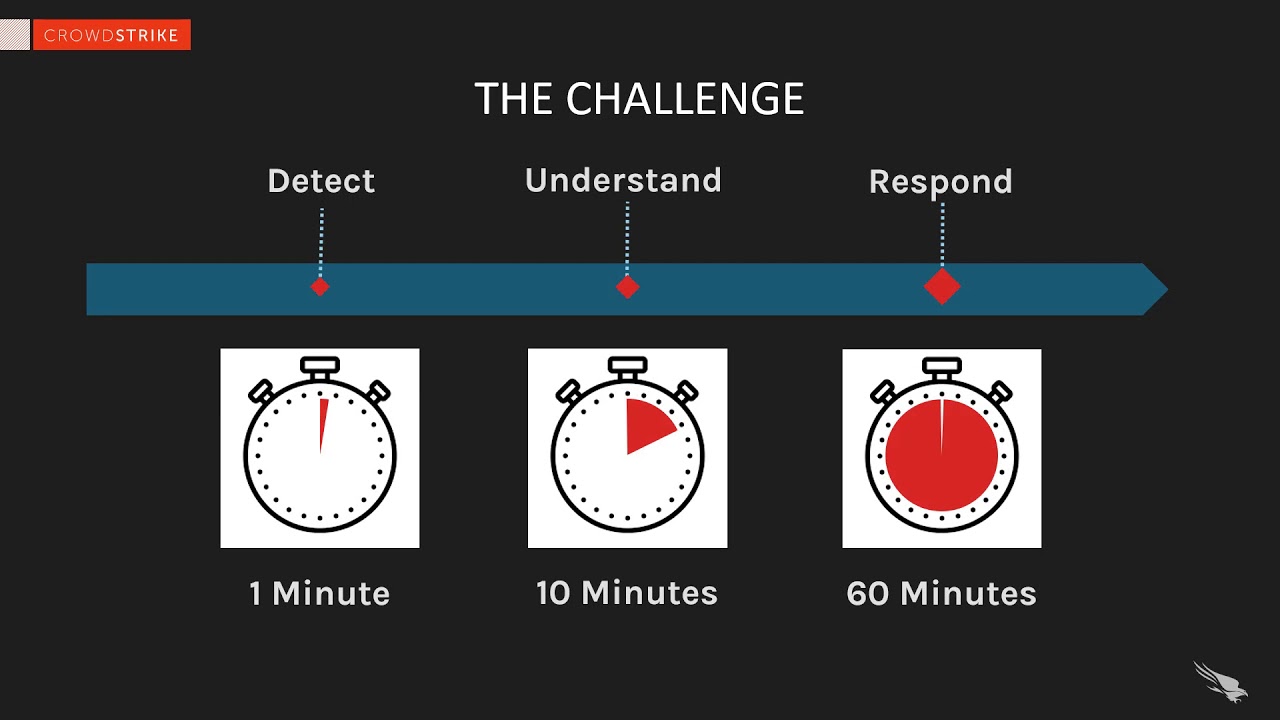
What is the 1 10 60 rule
Josh ThomsonReady For Anything: Do You Meet The 1-10-60 Rule When you are the victim of a cyberattack, the time it takes you to identify and resolve a breach is critical. Experts recommend aiming to meet the 1-10-60 rule: 1 minute to detect, 10 minutes to investigate and 60 minutes to remediate.
What are the 5 rules of cyber security
Content Quick Links:Introduction.Law 1: if there is a vulnerability, it will be exploited.Law 2: Everything is vulnerable in some way.Law 3: Humans can trust even when they shouldn't.Law 4: with innovation comes an opportunity for exploitation.Law 5: when in doubt, see law 1.
What is the number one rule of cybersecurity
Treat Everything Like It's Vulnerable
The first rule of cybersecurity is to treat everything as if it's vulnerable because, of course, everything is vulnerable. Every risk management course, security certification exam, and audit mindset always emphasizes that there is no such thing as a 100% secure system.
What are the three rules of cyber security
Find out about the five golden rules of cybersecurity.Think before clicking. – Whether in your e-mail or Internet browser, never click on links or open attachments of dubious origin.Use strong passwords.Lock the device when you are away.Do not connect unkown devices.Carry out regular backups.
What is 90 10 cybersecurity rule
The 90/10 rule on security states that 90% of cybersecurity is about implementing the right policies and procedures, while the other 10% is about implementing the right technology. People represent your human risk, which is the least managed and mitigated risk in cybersecurity.
What is 5 nines cyber security
Five-nines availability — or 99.999% — is the percentage of time a network component or service is accessible to a user in a given period, usually defined as a year. The migration from private networks to cloud services has led companies to demand that service providers offer five-nines availability.
What are 10 cyber safety rules
Get the latest anti-virus and firewall software.Update your internet browser.Create a strong and easy-to-remember password.Use a different password to the one you use for other services.Change your password on a regular basis.Never share your password.Don't let your browser remember your log on details.
What is 321 rule in cyber security
The 3-2-1 rule states that in order to be fully protected, organizations must have three copies of their data on two different types of media, with one copy off site. The rule was created when tape was the backup media of choice and predates cloud backups, which explains why it might be due for an upgrade.
What are the four 4 cybersecurity protocols
Four security protocols to protect the new normal, a hybridAccess Control.Authentication.Information Protection.Automated Monitoring.
What is the 80 20 rule security
So logically, if we can eliminate or significantly reduce the risk from that 80% of attacks—and we do it by implementing just a handful of targeted, focused and related controls—then we'd be able to mitigate 80% of an organization's information security risk with 20% of the effort.
What is 42 in cyber security
The Unit 42 Threat Intelligence team provides threat research that enables security teams to understand adversary intent and attribution, while enhancing protections offered by our products and services to stop advanced attacks.
What is cyber safety class 10
Cyber safety and security can be defined as the practice of defending our computers, servers, mobile devices, electronic systems, and any kind of network, from malicious attacks initiated by antisocial groups and organisations.
What is the 4 3 2 rule security
A 4-3-2 strategy means backups are duplicated and geographically distant to offer protection from events like natural disasters. Backups are also stored on two separate networks, isolating them from production networks in the event they're compromised.
What are the 7 layers of cyber security
The 7 layers of cyber security are:Physical security.Network security.Perimeter security.Endpoint security.Application Security.Data security.User education.
What are the 6 phases of cybersecurity
cyber incident response plan has 6 phases, namely, Preparation, Identification, Containment, Eradication, Recovery and Lessons Learned. Any organisation that is serious about its cybersecurity requires a solid cyber incident response plan.
What is security 90 10 rule
The 90/10 rule on security states that 90% of cybersecurity is about implementing the right policies and procedures, while the other 10% is about implementing the right technology. People represent your human risk, which is the least managed and mitigated risk in cybersecurity.
What is the 90 10 rule for good security
10% of security safeguards are technical. 90% of security safeguards rely on the computer user to adhere to good computing practices. Example: The lock on your car is the 10%. You remembering to close the door, lock the lock, put up the windows, and keep control of your keys is the 90%
What is cyber 9
The “Cyber 9-Line” is a template of questions that participating National Guard units use to quickly communicate a cyber incident to USCYBERCOM.
What is cyber 9 12
The Cyber 9/12 Strategy Challenge is a cyber policy and strategy competition where students compete in developing policy recommendations tackling a fictional cyber catastrophe.
What is cyber safety class 12
Let's know it! Cyber safety and security can be defined as the practice of defending our computers, servers, mobile devices, electronic systems, and any kind of network, from malicious attacks initiated by antisocial groups and organisations.
What is cyber class 11
Ans: Cyber safety refers to the safe and responsible use of internet to ensure safety and security of personal information. It also includes not creating threat for anyone else's information.
What are the 6 steps of cyber security
6 phases of the cyber incident response lifecyclePreparation.Identification.Containment.Eradication.Recovery.Lessons learned.
What are the 7 types of cyber security
It can be divided into seven main pillars:Network Security. Most attacks occur over the network, and network security solutions are designed to identify and block these attacks.Cloud Security.Endpoint Security.Mobile Security.IoT Security.Application Security.Zero Trust.
What is the 90 10 formula
The 90/10 investing strategy for retirement savings involves allocating 90% of one's investment capital in low-cost S&P 500 index funds and the remaining 10% in short-term government bonds. The 90/10 investing rule is a suggested benchmark that investors can easily modify to reflect their tolerance to investment risk.
What is 80 20 rule in cyber security
How security teams can achieve 80% of the benefit for 20% of the work. Information risk has multiple components. With too many threats to assess individually, too many vulnerabilities to patch all at once, and many choices among controls, where should security leaders start