What is the 3-2-1 backup strategy
The 3-2-1 backup strategy simply states that you should have 3 copies of your data (your production data and 2 backup copies) on two different media (disk and tape) with one copy off-site for disaster recovery.
What is the 3-2-1 golden backup rule
3: Keep 3 copies at least (one primary backup and two copies) to ensure that you can recover the data from any accidents. 2: Save backups to two different storage devices or locations. 1: Keep at least one backup copy in a different location.
What are the three strategies of backups
There are mainly three types of backup: full, differential, and incremental.
What’s the 321 rule
Here's what the 3-2-1 backup rule involves: 3: Create one primary backup and two copies of your data. 2: Save your backups to two different types of media. 1: Keep at least one backup file offsite.
What is 321 backup rule wiki
3-2-1 Rule (or 3-2-1 Backup Strategy) The idea that a minimal backup solution should include three copies of the data, including two local copies and one remote copy.
What is the 3-2-1 backup rule Wiki
The 3-2-1 rule can aid in the backup process. It states that there should be at least 3 copies of the data, stored on 2 different types of storage media, and one copy should be kept offsite, in a remote location (this can include cloud storage).
What is a 3-2-1 backup for ransomware
Complete Ransomware Protection Starts With 3-2-1-1
It says to keep three copies of your data—one primary and two backups—with two copies stored locally on two formats (network-attached storage, tape, or local drive) and one copy stored offsite in the cloud or secure storage.
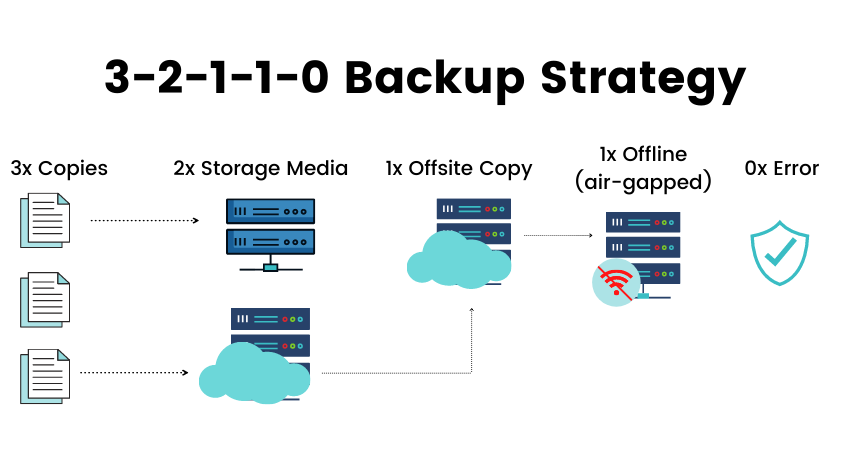
What is 3-2-1 1 0 backup rule
You should have at least 3 copies of your data, including the production copy. At least 2 different storage media should be used; for instance, a tape and a cloud storage. At least 1 of the copies should be kept off-site, in case your machines are physically damaged.
What is the 3-2-1 backup rule Wikipedia
The 3-2-1 rule can aid in the backup process. It states that there should be at least 3 copies of the data, stored on 2 different types of storage media, and one copy should be kept offsite, in a remote location (this can include cloud storage).
What is the benefit of the 3-2-1 backup rule
One additional benefit of using the 3-2-1 rule is the ability to perform certain data analytics functions on the data copies (the data stored in backup or disaster recovery infrastructure) rather than on the original data. Along with its seeming simplicity, another benefit to this rule is its allowance for fine-tuning.
Who invented the 3-2-1 backup rule
photographer Peter Krogh’s
(3-2-1 Backup Strategy Guide)
The rule was first coined in photographer Peter Krogh's 2005 book on digital asset management. Over time, people have adapted it to suit a changing business and technical landscape, but the core concepts remain the same.
What is the 3-2-1 backup rule reddit
3: Have at least 3 copies of your data, no problem. 1: Have at least 1 offsite copy, which makes total sense, but it might be tough for people paying for a cloud service (times are tough). The cheapest option would be an external drive kept at a friend's house with the most important data.
What does the 3-2-1 1 rule define backup principles to follow
Principles of the 3-2-1 backup rule: 3: Keep 3 copies of your data. 2: Store the data copies on 2 different devices or media types. 1: Store 1 copy of data offsite.
Which backup strategy is guaranteed protection against ransomware
Keep at least one backup offsite or offline
Aside from actually implementing backups, the most important aspect of protecting backups from ransomware is making sure they can't be breached. Keeping a backup offline or physically offsite is one of the best ways to ensure there's no way ransomware can touch them.
What are the three types of ransomware
The most common types include:Crypto Ransomware or Encryptors. Encyrptors are one of the most well-known and damaging variants.Lockers. Lockers completely lock you out of your system, so your files and applications are inaccessible.Scareware.Doxware or Leakware.RaaS (Ransomware as a Service)
What is the 321 backup rule reddit
3: Have at least 3 copies of your data, no problem. 1: Have at least 1 offsite copy, which makes total sense, but it might be tough for people paying for a cloud service (times are tough). The cheapest option would be an external drive kept at a friend's house with the most important data.
What is 3-2-1 backup Veritas
A dependable recovery process for guaranteeing that data is appropriately safeguarded and backup copies of the data are available when needed is the 3-2-1 backup strategy. The three copies of the data to be safeguarded are saved on two distinct types of storage media, and one copy of the data is transported offsite.
What is 3-2-1 backup ransomware
Complete Ransomware Protection Starts With 3-2-1-1
It says to keep three copies of your data—one primary and two backups—with two copies stored locally on two formats (network-attached storage, tape, or local drive) and one copy stored offsite in the cloud or secure storage.
What is the 3-2-1 backup rule ransomware
The 3-2-1 rule states that in order to be fully protected, organizations must have three copies of their data on two different types of media, with one copy off site. The rule was created when tape was the backup media of choice and predates cloud backups, which explains why it might be due for an upgrade.
What is 3 2 1 backup ransomware
Complete Ransomware Protection Starts With 3-2-1-1
It says to keep three copies of your data—one primary and two backups—with two copies stored locally on two formats (network-attached storage, tape, or local drive) and one copy stored offsite in the cloud or secure storage.
What are the 2 main types of ransomware
In particular, two types of ransomware are very popular:Locker ransomware. This type of malware blocks basic computer functions.Crypto ransomware. The aim of crypto ransomware is to encrypt your important data, such as documents, pictures and videos, but not to interfere with basic computer functions.
What do 91% of ransomware attacks start with
phishing email
According to reports, 91% of all attacks begin with a phishing email to an unsuspecting victim. On top of that, 32% of all successful breaches involve the use of phishing techniques.
What are the three main types of ransomware
The most common types include:Crypto Ransomware or Encryptors. Encyrptors are one of the most well-known and damaging variants.Lockers. Lockers completely lock you out of your system, so your files and applications are inaccessible.Scareware.Doxware or Leakware.RaaS (Ransomware as a Service)
What are the top 3 causes of successful ransomware attacks
Ransomware attack vectors and mitigations
The top three ways ransomware gets onto victims' systems are phishing, Remote Desktop Protocol (RDP) and credential abuse, and vulnerabilities.
What are the two 2 main types of ransomware
In particular, two types of ransomware are very popular:Locker ransomware. This type of malware blocks basic computer functions.Crypto ransomware. The aim of crypto ransomware is to encrypt your important data, such as documents, pictures and videos, but not to interfere with basic computer functions.