What are the different types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military.
What is an example of vulnerability
Vulnerability Examples
Any susceptibility to humidity, dust, soiling, natural disaster, poor encryption, or firmware vulnerability.
What is the introduction of vulnerability
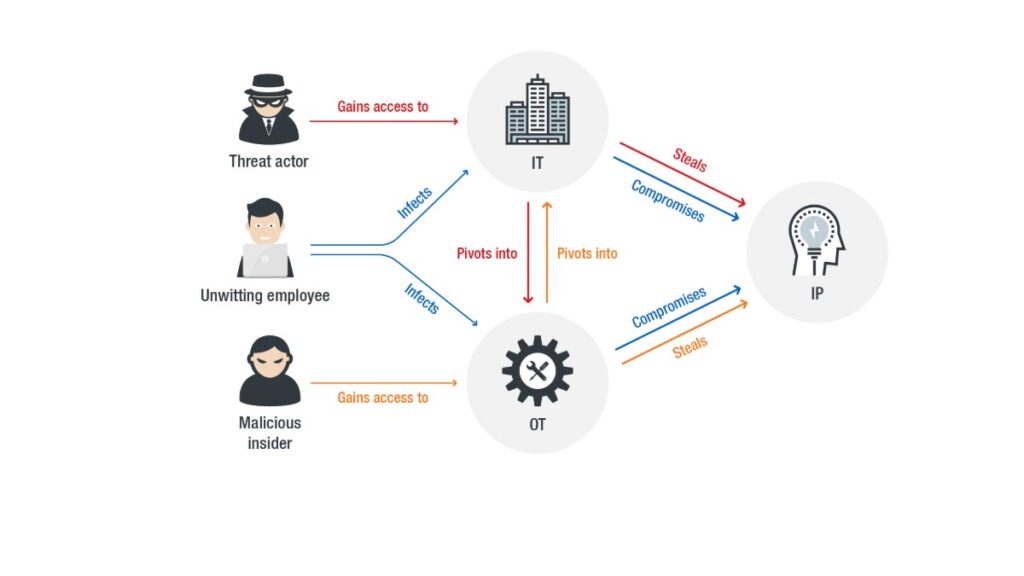
A vulnerability in security refers to a weakness or opportunity in an information system that cybercriminals can exploit and gain unauthorized access to a computer system.
What are the 4 characteristics of vulnerability
Vulnerability is more widespread than many of us realise. There are four characteristics to be aware of: poor health, experiencing a negative life event, having low financial resilience and having low capability. It's potentially a huge disadvantage as it can lead you to make poor financial decisions.
What are the 4 types of vulnerability in disaster management
Vulnerability relates to a number of factors, including:Physical factors. e.g. poor design and construction of buildings, unregulated land use planning, etc.Social factors.Economic factors.Environmental factors.
What are 5 examples of social vulnerability
Disruption of communication, power supply, water supply, public services… Vulnerable residential settings (i.e. weak structure, poor protection, poor maintenance, etc.) Lack of or Limited access to critical services such as communication, transportation, power supply, water supply, sanitation, etc.
What is the best definition of vulnerability
1. : capable of being physically or emotionally wounded. 2. : open to attack or damage : assailable. vulnerable to criticism.
Which are the 4 key drivers of vulnerability
4 key drivers of customer vulnerabilityHealth. Conditions or illnesses that affect one's ability to complete day-to-day tasks, both mentally and physically.Life Events. Such as bereavement, job loss or relationship breakdown.Resilience. Low ability to withstand and manage financial or emotional shocks.Capability.
What are the four stages of vulnerability management
The four continuous stages of identification, prioritization, remediation, and reporting are essential for an effective vulnerability management process. A vulnerability is a flaw or weakness in a system that, if exploited, would allow a user to gain unauthorized access to conduct an attack.
What are the 4 factors of disaster management
Preparedness, Response, Recovery & Prevention/MitigationPreparedness – First, prepare to protect yourself, others and items of great importance in the event an emergency/disaster occurs.Response – When there is an actual occurrence, administer first aid or get medical attention for victims if necessary.
What are 4 disaster risk factors
PW Disaster riskEnviromental degradation.Globalized economic development.Poverty and inequality.Poorly planned urban development.Weak governance.
What are 3 examples of vulnerability
Examples may include:poor design and construction of buildings,inadequate protection of assets,lack of public information and awareness,limited official recognition of risks and preparedness measures, and.disregard for wise environmental management.
What are the causes of vulnerability
Vulnerability is most often associated with poverty, but it can also arise when people are isolated, insecure and defenseless in the face of risk, shock or stress. People differ in their contact to risk as a result of their social group, gender, ethnic or other individuality, age and other factor.
What is human vulnerability
Human Vulnerability is a specific code or metaprogram hard wired in human mind that can be exploited to cause harm. Exploitation may occur via a known or unknown attacker. The human vulnerability profiling is the testing process used to identify possible mindset exploits that can be used for penetrating the system.
What are the 4 requirements of every vulnerability management program
Let us examine briefly each stage and see how Tripwire can help you.The First Stage: The Scanning Process. The first step is to identify the criticality of your organization's assets.Stage Two: Asset Discovery and Inventory.Stage Three: Vulnerability Detection.Stage Four: Reporting and Remediation.How Tripwire Helps.
What is log 4 js vulnerability
Log4Shell is a software vulnerability in Apache Log4j 2, a popular Java library for logging error messages in applications. The vulnerability, published as CVE-2021-44228, enables a remote attacker to take control of a device on the internet if the device is running certain versions of Log4j 2.
What are the 5 steps of vulnerability management
There are five main stages in the vulnerability management cycle include:Assess.Prioritize.Act.Reassess.Improve.
What are the 4 C’s of disaster recovery
Aligned with the founding principles of the National Voluntary Organizations Active in Disaster (National VOAD), VALs are committed to fostering the four Cs: communication, coordination, collaboration, and cooperation.
What are the 4 phases of emergency management
However, preparedness is only one phase of emergency management. Current thinking defines four phases of emergency management: mitigation, preparedness, response, and recovery.
What are the 4 key disaster characteristics
Many of those who choose not to define a disaster by its origin/cause define it according to its characteristics. These may include: (1) length of forewarning, (2) magnitude of impact, (3) scope of impact, and (4) duration of impact.
What are the 5 types of vulnerable
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What are the 3 points of vulnerability
Vulnerability is a weakness which allows an attacker to reduce a system's information assurance. Vulnerability is the intersection of three elements : a system susceptibility or defect, attacker access to the defect, and attacker capability to exploit the defect.
What is Log4Shell exploit
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
What is log4 in cyber security
Log4j is used by developers to keep track of what happens in their software applications or online services. It's basically a huge journal of the activity of a system or application. This activity is called 'logging' and it's used by developers to keep an eye out for problems for users.
What are the 4 pillars of disaster risk
The 4 Phases of Disaster ManagementMitigation.Preparedness.Response.Recovery.