What is the CVE code for Log4j vulnerability
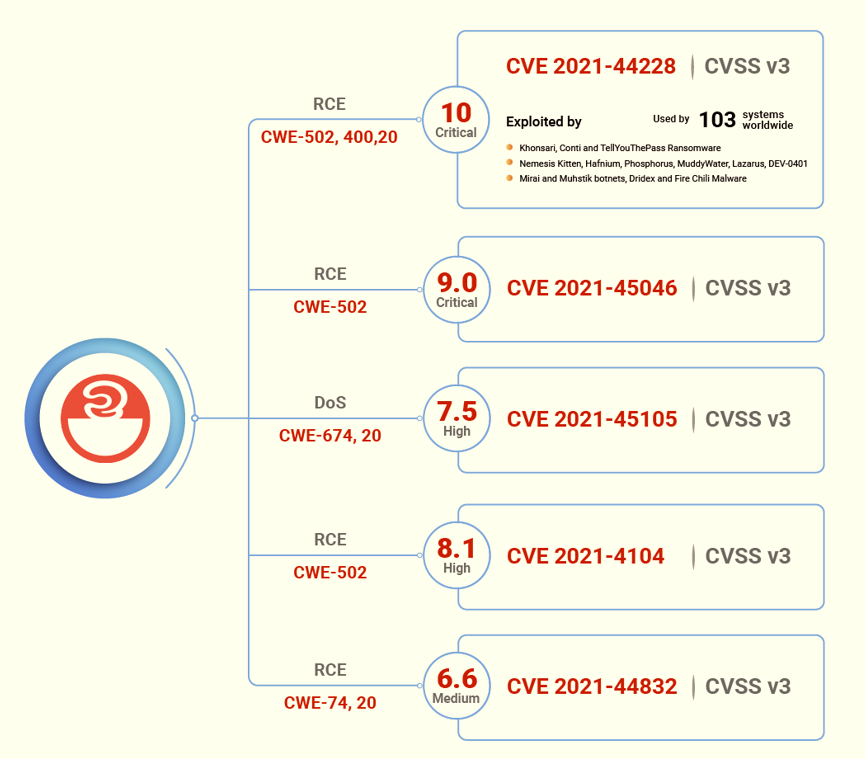
CVE-2021-44228
CVE-2021-44228: Apache Log4j2 JNDI features do not protect against attacker controlled LDAP and other JNDI related endpoints. Log4j2 allows Lookup expressions in the data being logged exposing the JNDI vulnerability, as well as other problems, to be exploited by end users whose input is being logged.
What is the name of the vulnerability in Log4j
Log4Shell (CVE-2021-44228, CVE-2021-45046 and CVE-2021-45105) is a remote code execution (RCE) vulnerability that enables malicious actors to execute arbitrary Java code, taking control of a target server.
What is the vulnerability of Log4j 1.2 13
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data.
What is the vulnerability of Log4j 1.2 15
Affected versions of this package are vulnerable to Man-in-the-Middle (MitM). Improper validation of certificate with host mismatch in Apache Log4j SMTP appender. This could allow an SMTPS connection to be intercepted by a man-in-the-middle attack which could leak any log messages sent through that appender.
Does Log4j 1.2 17 have vulnerability
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data.
What is the CVE ID for this specific vulnerability
A CVE ID is a unique, alphanumeric identifier assigned by the CVE Program. Each identifier references a specific vulnerability. The “Year” portion is the year that the CVE ID was reserved or the year the vulnerability was made public. The year portion is not used to indicate when the vulnerability was discovered.
What is the CVSS for the Log4j vulnerability
It's described as a zero-day (0 day) vulnerability and rated the highest severity under the Common Vulnerability Scoring System (CVSS; CVE-2021-44228). It was rated a 10 out of 10 on the CVSS, due to the potential impact that it can have if leveraged by attackers.
Does Log4j 1.2 14 have vulnerability
Affected versions of this package are vulnerable to Deserialization of Untrusted Data. JMSSink in all versions of Log4j 1. x is vulnerable to deserialization of untrusted data when the attacker has write access to the Log4j configuration or if the configuration references an LDAP service the attacker has access to.
What is the replacement for Log4j 1.2 17
Initiated by Ceki Gülcü, the original author of Apache log4j 1. x, the reload4j project is a fork of Apache log4j version 1.2. 17 with the goal of fixing pressing security issues. Reload4j is a binary compatible, drop-in replacement for log4j version 1.2.
What is CVE numbering
CVE, short for Common Vulnerabilities and Exposures, is a list of publicly disclosed computer security flaws. When someone refers to a CVE, they mean a security flaw that's been assigned a CVE ID number. Security advisories issued by vendors and researchers almost always mention at least one CVE ID.
What is 7 zip vulnerability CVE
CVE-2022-29072
7-Zip vulnerability or CVE-2022-29072 is an active zero-day vulnerability and is characterized as allowing privilege escalation and command execution for Windows when a file with the .
Is CVSS the same as CVE
Differences between CVSS and CVE
CVSS is the overall score assigned to a vulnerability. CVE is simply a list of all publicly disclosed vulnerabilities that includes the CVE ID, a description, dates, and comments. The CVSS score is not reported in the CVE listing – you must use the NVD to find assigned CVSS scores.
What is CVE vs CVSS score
The CVE represents a summarized vulnerability, while the Common Vulnerability Scoring System (CVSS) assesses the vulnerability in detail and scores it, based on several factors.
Is Log4j 1.2 17 vulnerable or not
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data.
Is Log4j 1.2 7 vulnerable
JMSAppender, in log4j 1.2 version, is vulnerable to deserialization of untrusted data if the attacker has the 'write' permissions to the log4j configuration.
What is CVE 2013 4786
The IPMI 2.0 specification supports RMCP+ Authenticated Key-Exchange Protocol (RAKP) authentication, which allows remote attackers to obtain password hashes and conduct offline password guessing attacks by obtaining the HMAC from a RAKP message 2 response from a BMC.
What is CVE 2007 4559
Directory traversal vulnerability in the (1) extract and (2) extractall functions in the tarfile module in Python allows user-assisted remote attackers to overwrite arbitrary files via a .. (dot dot) sequence in filenames in a TAR archive, a related issue to CVE-2001-1267.
What is 7-Zip 21.07 vulnerability
Privilege escalation vulnerability was found in 7-Zip. Malicious users can exploit this vulnerability to gain privileges and execute arbitrary code by dragging and dropping file with the . 7z extension to the Help>Contents area. The vulnerability announced in version 21.07 and disputed by vendor.
What is 7-Zip CVE 2016 7804 untrusted search path vulnerability
Untrusted search path vulnerability in 7 Zip for Windows 16.02 and earlier allows remote attackers to gain privileges via a Trojan horse DLL in an unspecified directory. Note: References are provided for the convenience of the reader to help distinguish between vulnerabilities.
What is the CVE of the log4j vulnerability with the highest CVSS score
CVE-2021-44228
It's described as a zero-day (0 day) vulnerability and rated the highest severity under the Common Vulnerability Scoring System (CVSS; CVE-2021-44228). It was rated a 10 out of 10 on the CVSS, due to the potential impact that it can have if leveraged by attackers.
What is CVE ID and CVSS
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
Why did Log4j vulnerability receive the highest CVSS score
The Apache Software Foundation, which publishes the Log4j 2 library, gave the vulnerability a CVSS score of 10 out of 10, the highest-level severity score, because of its potential for widespread exploitation and the ease with which malicious attackers can exploit it.
What is the CVE of the vulnerability
CVE, short for Common Vulnerabilities and Exposures, is a list of publicly disclosed computer security flaws. When someone refers to a CVE, they mean a security flaw that's been assigned a CVE ID number.
Is Log4j 2.16 0 vulnerable
Vulnerability Details
DESCRIPTION: Apache Log4j is vulnerable to a denial of service, caused by the failure to protect from uncontrolled recursion from self-referential lookups.
What is CVE 2010 2568
The CVE-2010-2568 vulnerability was most notable for being the flaw used by the stealth threat Stuxnet to gain access to target systems, though it has also since been leveraged by other malware families. Exploit:W32/WormLink was first seen in 2010 spreading via infected removable drives.