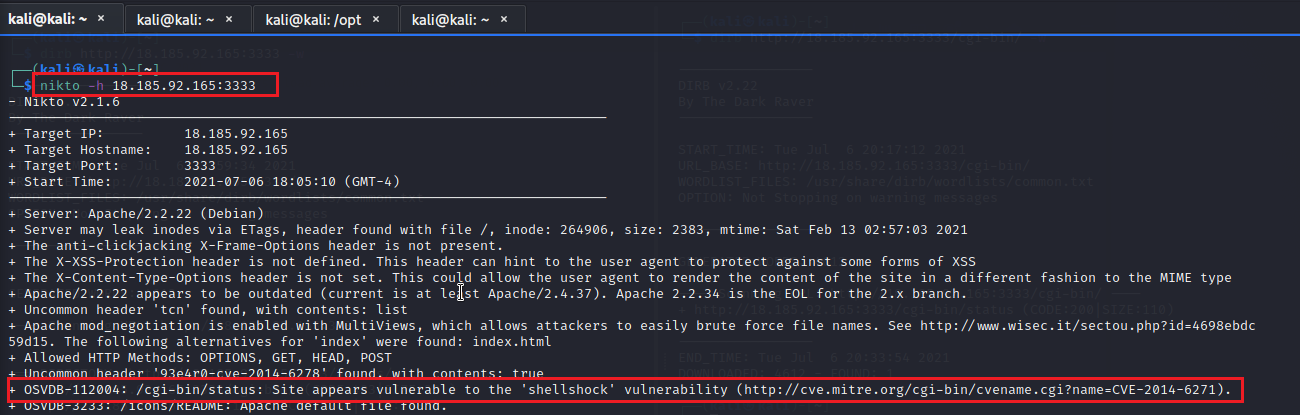
What is the vulnerability of Shellshock
What is the Shellshock Remote Code Execution Vulnerability It is a security bug in the Unix Bash shell that causes Bash to execute bash commands from environment variables unintentionally.
What version of Bash is shellshock vulnerability
It's a vulnerability that affects GNU Bash from version 1.14 to those lower than 4.3. This bug affects Unix-based OSes, including Linux, BSD, and macOS systems. Additionally, since Linux powers many internet servers and IoT devices, these might also be vulnerable to this exploit.
How is Shellshock exploited
Shellshock is an arbitrary code execution vulnerability that offers a way for users of a system to execute commands that should be unavailable to them. This happens through Bash's "function export" feature, whereby one Bash process can share command scripts with other Bash processes that it executes.
What was unique about the bash bug vulnerability
The current command Bash interpreter lets users execute commands on a computer. The vulnerability allows attackers to run malicious scripts in systems and servers, which compromises everything in it.
What is CVE 2014 6278
GNU Bash through 4.3 bash43-026 does not properly parse function definitions in the values of environment variables, which allows remote attackers to execute arbitrary commands via a crafted environment, as demonstrated by vectors involving the ForceCommand feature in OpenSSH sshd, the mod_cgi and mod_cgid modules in …
What is vulnerability cve 2014 6271
The Shellshock Vulnerability (CVE-2014-6271) is a serious vulnerability in Bash on Linux. According to RedHat, “A flaw was found in the way Bash (aka bourne-again shell) evaluated certain specially crafted environment variables.
What does CVE 2014 6271 belong to
The Shellshock Vulnerability (CVE-2014-6271) is a serious vulnerability in Bash on Linux. According to RedHat, “A flaw was found in the way Bash (aka bourne-again shell) evaluated certain specially crafted environment variables.
How do you detect vulnerability in shellshock
To detect this vulnerability the script executes a command that prints a random string and then attempts to find it inside the response body. Web apps that don't print back information won't be detected with this method. By default the script injects the payload in the HTTP headers User-Agent, Cookie, and Referer.
What Bash versions are vulnerable to Shellshock CVE 2014 6271 )
The critical Bash Bug vulnerability, also dubbed Shellshock, affects versions GNU Bash versions ranging from 1.14 through 4.3. A threat actor could exploit it to execute shell commands remotely on a targeted machine using specifically crafted variables.
Does Shellshock still work
Although the ShellShock vulnerability, CVE-2014-6271, was discovered in 2014, it is known to still exist on a large number of servers in the world. The vulnerability was updated (CVE-2014-7169) soon after and has been modified up until 2018. The main reason Shellshock is still in use is no shocker.
What is CVE 2014 6271
The Shellshock Vulnerability (CVE-2014-6271) is a serious vulnerability in Bash on Linux. According to RedHat, “A flaw was found in the way Bash (aka bourne-again shell) evaluated certain specially crafted environment variables.
What is CVE 2013 2566
The RC4 algorithm, as used in the TLS protocol and SSL protocol, has many single-byte biases, which makes it easier for remote attackers to conduct plaintext-recovery attacks via statistical analysis of ciphertext in a large number of sessions that use the same plaintext.
What is CVE 2014 0224
The CCS Injection Vulnerability (CVE-2014-0224) is a serious vulnerability in the popular OpenSSL cryptographic software library. OpenSSL is an implementation of the SSL/TLS encryption protocol used to protect the privacy of Internet communication.
What is CVE 2014 4078
IIS Security Feature Bypass Vulnerability – CVE-2014-4078
A security feature bypass vulnerability exists in Microsoft Information Services (IIS) that is caused when incoming web requests are not properly compared against the "IP and domain restriction" filtering list.
What is CVE 2014 3704
Exploits CVE-2014-3704 also known as 'Drupageddon' in Drupal. Versions < 7.32 of Drupal core are known to be affected. Vulnerability allows remote attackers to conduct SQL injection attacks via an array containing crafted keys.
Is ShellShock 2 a horror game
ShellShock 2: Blood Trails is a violent, first-person, survival horror game set against the backdrop of the Vietnam War.
What is CVE 2010 2568
The CVE-2010-2568 vulnerability was most notable for being the flaw used by the stealth threat Stuxnet to gain access to target systems, though it has also since been leveraged by other malware families. Exploit:W32/WormLink was first seen in 2010 spreading via infected removable drives.
What is CVE 2013 4786
The IPMI 2.0 specification supports RMCP+ Authenticated Key-Exchange Protocol (RAKP) authentication, which allows remote attackers to obtain password hashes and conduct offline password guessing attacks by obtaining the HMAC from a RAKP message 2 response from a BMC.
What horror game deletes itself
Killswitch
Killswitch, by design, deletes itself upon player completion of the game.
What is the scariest jumpscare in games
10 Best Jump Scares In Gaming10 Krypt Monster.9 Fatal Frame Broken Neck Lady.8 Batman Arkham Knight Man-Bat.7 Alien Isolation Alien.6 P.T. Lisa.5 F.E.A.R. Alma.4 Condemned Locker Man.3 Resident Evil Interrogation Room.
What is CVE 2015 9251
Description. The MITRE CVE dictionary describes this issue as: jQuery before 3.0. 0 is vulnerable to Cross-site Scripting (XSS) attacks when a cross-domain Ajax request is performed without the dataType option, causing text/javascript responses to be executed.
What is the oldest horror game
Haunted House
The earliest rudimentary attempt at a horror video game dates back to as early as 1972, when a Haunted House overlay was included with the first video game console, the Magnavox Odyssey, inspired by haunted house fiction.
Why do scary games exist
The most obvious answer is that we get to experience danger. The thrill of danger gets the blood pumping and we can feel the adrenaline. There's a rush of excitement going through one's body when adrenaline is released. So, naturally, we will feel a sense of pleasure – even if it is a scary sensation.
What is the oldest jumpscare
Cat People (1942)
Cat People (1942), which featured the Lewton Bus technique, considered the first jump scare.
Are jump scares bad
Cardiologists are of the opinion that while movies with jump scare scenes may not pose a heart attack risk to everyone, if someone suffers from paranoia or PTSD, is elderly or has a pre-existing heart condition, it is recommended that they avoid watching such movies and that they should not partake in fear-evoking …