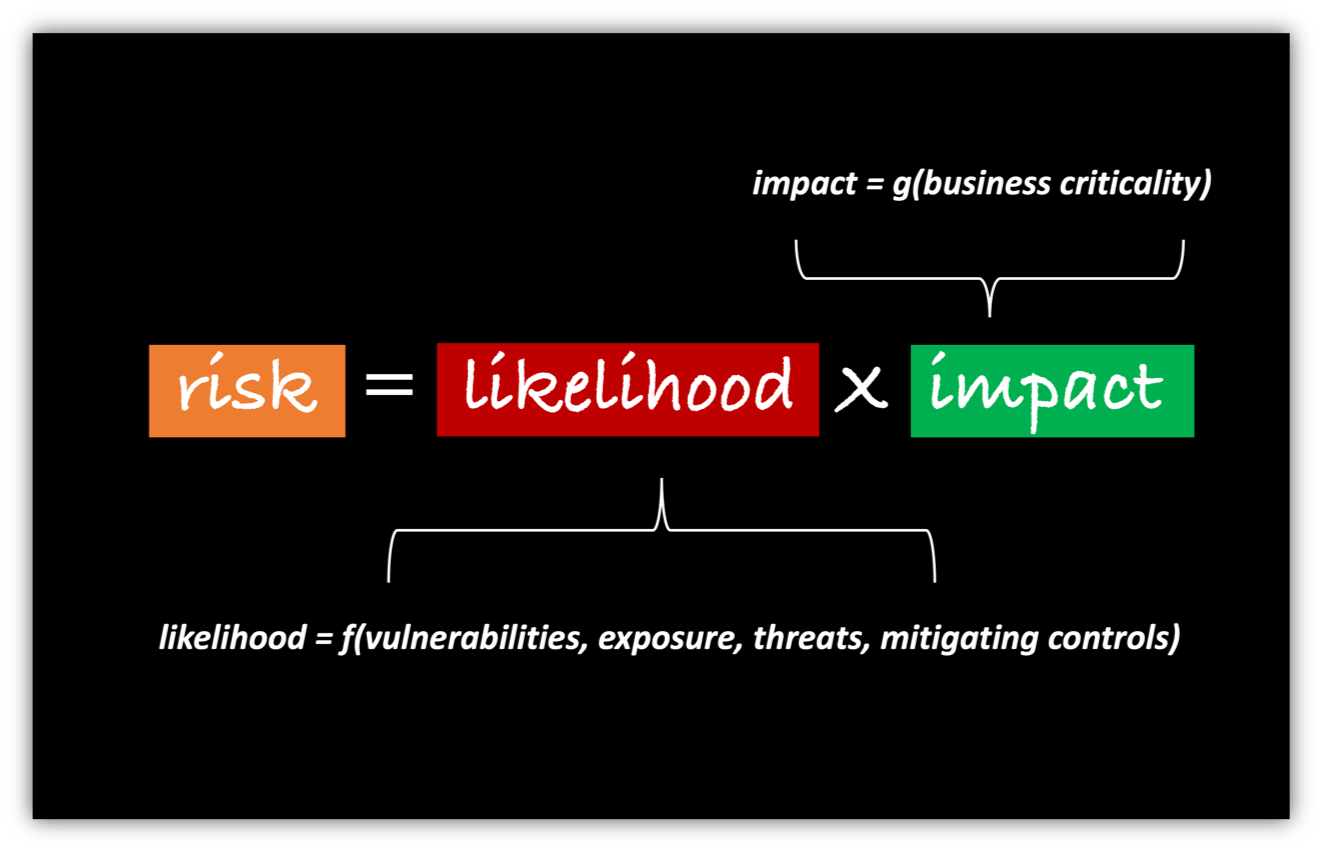
What is the formula for cybersecurity risk
Cyber risk is calculated by considering the identified security threat, its degree of vulnerability, and the likelihood of exploitation. At a high level, this can be quantified as follows: Cyber risk = Threat x Vulnerability x Information Value.
How is NIST risk calculated
Use the NIST matrix
For instance, if you have a medium threat likelihood and a high impact probability, you would multiply 100 x 0.5 for a score of 50. This score means that your company is classified as a medium risk under the scoring scale: High (>50 to 100); Medium (>10 to 50); Low (1 to 10).
What is cyber risk scoring
A cyber risk score is a numerical assessment of the level of security of an organization's networks and systems. It is a measure of the vulnerability of its cyber infrastructure to external threats such as malicious attacks, data theft, and unauthorized access.
What is factor of risk in cyber security
Cybersecurity risk is the probability of exposure or loss resulting from a cyber attack or data breach on your organization. A better, more encompassing definition is the potential loss or harm related to technical infrastructure, use of technology or reputation of an organization.
What is the formula of risk
Risk is the combination of the probability of an event and its consequence. In general, this can be explained as: Risk = Likelihood × Impact.
How is security risk measured
The five measures include the alpha, beta, R-squared, standard deviation, and Sharpe ratio. Risk measures can be used individually or together to perform a risk assessment. When comparing two potential investments, it is wise to compare like for like to determine which investment holds the most risk.
How to calculate risk in ISO 27001
Main steps in ISO 27001 risk assessmentRisk identification (listing assets, threats, and vulnerabilities)Assigning risk owners (persons responsible for risk)Risk analysis (assessing consequences and likelihood)Risk calculation (determining the level of risk)Risk evaluation (accepting the risks based on criteria)
What is the formula for risk threat vulnerability
Risk = threat x vulnerability
We can sum up this calculation with the concepts from above: that a single vulnerability multiplied by the potential threat (frequency, existing safeguards, and potential value loss) can give you an estimate of the risk involved.
How do you analyze cyber risk
Now let's look at what steps need to be taken to complete a thorough cyber risk assessment, providing you with a risk assessment template.Step 1: Determine Informational Value.Step 2: Identify and Prioritize Assets.Step 3: Identify Cyber Threats.Step 4: Identify Vulnerabilities.
What are the 4 main risk factors
In general, risk factors can be categorised into the following groups:Behavioural.Physiological.Demographic.Environmental.Genetic.
What are 5 risk factors
A poor diet, high blood pressure and cholesterol, stress, smoking and obesity are factors shaped by your lifestyle and can be improved through behavior modifications. Risk factors that cannot be controlled include family history, age and gender.
What is the formula for risk in Cissp
Risk = Threat x Vulnerability x Impact (How bad is it). Total Risk = Threat x Vulnerability x Asset Value.
What is the formula for total risk
Total risk = Systematic risk + Unsystematic risk
In a large portfolio: Some stocks will go up in value because of positive company-specific events, while. Others will go down in value because of negative company-specific events.
How is risk calculated
Calculate the risk of attack: Risk = consequences × likelihood.
What is the formula to define risk
Risk can be defined as the combination of the probability of an event occurring and the consequences if that event does occur. This gives us a simple formula to measure the level of risk in any situation. Risk = Likelihood x Severity.
What is the security risk analysis
Security and risk analysis is a field that explores the integrated processes conducted to provide decision-makers with the information needed to understand factors that can negatively influence operations and outcomes, and make informed judgments concerning the extent of actions needed to reduce vulnerabilities, …
What are the 5 components of risk
There are several ways to categorize an effective risk management process's constituent elements, but at the very least it should incorporate the following risk management components.Risk Identification.Risk Analysis.Response Planning.Risk Mitigation.Risk Monitoring.
What are the 5 types of risk factors
Risk factors in health and diseaseBehavioural.Physiological.Demographic.Environmental.Genetic.
What are the 8 key risk types
These risks are: Credit, Interest Rate, Liquidity, Price, Foreign Exchange, Transaction, Compliance, Strategic and Reputation.
What is the risk score formula
The risk score is the result of your analysis, calculated by multiplying the Risk Impact Rating by Risk Probability. It's the quantifiable number that allows key personnel to quickly and confidently make decisions regarding risks.
What is the formula for risk level
Risk = Likelihood x Severity
The more likely it is that harm will happen, and the more severe the harm, the higher the risk. And before you can control risk, you need to know what level of risk you are facing. To calculate risk, you simply need to multiply the likelihood by the severity.
What is the formula for total risk Cissp
Total Risk = Threat x Vulnerability x Asset Value. Residual Risk = Total Risk – Countermeasures.
What is the formula cost of risk
Premium cost + estimated cost of retained losses + risk management costs = total cost of insurable risk.
What is a security risk matrix
A cyber security risk assessment matrix is a crucial tool for helping organisations protect sensitive data and prevent data breaches. The matrix provides a consistent way to measure and compare threats and vulnerabilities. It's also an ideal resource for explaining the findings of your risk assessment to the board.
What are the types of risk analysis in cyber security
Types of Cyber Security Risk AnalysisQualitative Risk Analysis.Quantitative Risk Analysis.Reduction in Costs.Provides Assessment Framework.Increases Organizational Knowledge.Avoid data breaches and Loss.Avoid regulatory issues.Avoid Application Glitches.