What is Nessus vulnerability
Nessus is a platform developed by Tenable that scans for security vulnerabilities in devices, applications, operating systems, cloud services and other network resources. Originally launched as an open source tool in 1998, its enterprise edition became a commercial product in 2005.
What vulnerabilities does Nessus scan for
Nessus can scan these vulnerabilities and exposures:Vulnerabilities that could allow unauthorized control or access to sensitive data on a system.Misconfiguration (e.g. open mail relay)Denials of service (Dos) vulnerabilities.Default passwords, a few common passwords, and blank/absent passwords on some system accounts.
Can Nessus exploit vulnerabilities
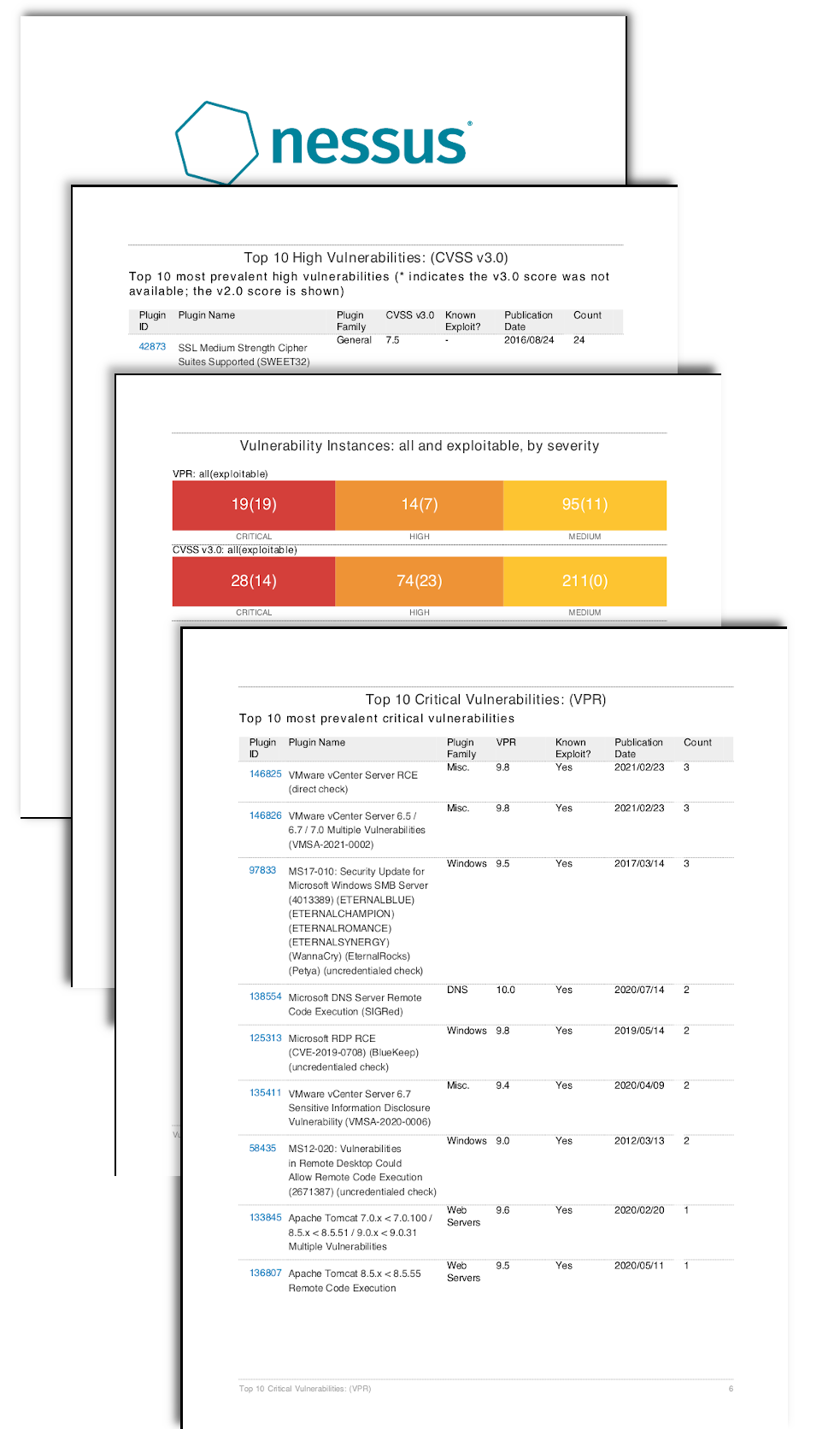
Nessus identifies exploitable vulnerabilities present in your scan results. The report contains two tables which bring focus to the exploitable vulnerabilities.
Is Nessus a good vulnerability scanner
Nessus is the most widely-used vulnerability scanner in the world. It looks for more than 57,000 possible security weaknesses from an external viewpoint. These weaknesses are known as “exploits” and they can give hackers a way into a system.
Is Nessus a web vulnerability scanner
Is Nessus a web vulnerability scanner Nessus was created as a network security scanner. With time, some web vulnerability tests were added to Nessus. However, web vulnerability scanning in Nessus does not offer as many features as Acunetix.
Why is Nessus not secure
The certificate may not be considered secure because "Nessus Certification Authority" is not a trusted valid certificate authority. Because of this, when Nessus is accessed through port 8834, the browser will produce a warning regarding an unsafe connection.
What is vulnerability scan
Vulnerability scanning is the process of discovering, analyzing, and reporting on security flaws and vulnerabilities. Vulnerability scans are conducted via automated vulnerability scanning tools to identify potential risk exposures and attack vectors across an organization's networks, hardware, software, and systems.
How do you find vulnerability in Nessus
To perform a vulnerability scan, you would need to navigate your browser to the link https://localhost:8834. See below: Hit the “New Scan” button above, then select the type of scan to perform from the numerous templates available. The templates shown above will be limited within the free version of Nessus.
What is vulnerability exploit
An exploit is a program, or piece of code, designed to find and take advantage of a security flaw or vulnerability in an application or computer system, typically for malicious purposes such as installing malware. An exploit is not malware itself, but rather it is a method used by cybercriminals to deliver malware.
How are vulnerabilities exploited
Exploitation is the next step in an attacker's playbook after finding a vulnerability. Exploits are the means through which a vulnerability can be leveraged for malicious activity by hackers; these include pieces of software, sequences of commands, or even open-source exploit kits.
Does Nessus scan for CVE
All Nessus and Passive Vulnerability Scanner plugins receive mappings to CVE, Bugtraq and other identifiers.
Which is a vulnerability scanner
A vulnerability scanner enables organizations to monitor their networks, systems, and applications for security vulnerabilities. Most security teams utilize vulnerability scanners to bring to light security vulnerabilities in their computer systems, networks, applications and procedures.
What is a vulnerability scanner
Vulnerability scanning is the process of identifying security weaknesses and flaws in systems and software running on them. This is an integral component of a vulnerability management program, which has one overarching goal – to protect the organization from breaches and the exposure of sensitive data.
What is CVE vulnerability scan
The Common Vulnerabilities and Exposures (CVE) system identifies all vulnerabilities and threats related to the security of information systems. To do this, a unique identifier is assigned to each vulnerability. Test for free the CVE Scanner Request a demo.
What is a process vulnerability
Unpatched and outdated software also creates OS vulnerabilities, because the system running the application is exposed, sometimes endangering the entire network. Process vulnerabilities are created when procedures that are supposed to act as security measures are insufficient.
What is vulnerability finding
A vulnerability assessment is a systematic review of security weaknesses in an information system. It evaluates if the system is susceptible to any known vulnerabilities, assigns severity levels to those vulnerabilities, and recommends remediation or mitigation, if and whenever needed.
How do I show vulnerability
Being vulnerable involves the following actions:Ask for what you need. When we're hurting, it's easy to dismiss our pain or try to protect ourselves and the people around us by closing off.Be willing to expose your feelings.Say what you want.Express what you really think.Slow down and be present.
What are the 4 main types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military. In relation to hazards and disasters, vulnerability is a concept that links the relationship that people have with their environment to social forces and institutions and the cultural values that sustain and contest them.
What is vulnerability and its types
Vulnerability describes the characteristics and circumstances of a community, system or asset that make it susceptible to the damaging effects of a hazard. There are many aspects of vulnerability, arising from various physical, social, economic, and environmental factors.
What is this vulnerability
A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorized access to a computer system. After exploiting a vulnerability, a cyberattack can run malicious code, install malware, and even steal sensitive data.
How are vulnerabilities detected
The vulnerability scanner uses a database to compare details about the target attack surface. The database references known flaws, coding bugs, packet construction anomalies, default configurations, and potential paths to sensitive data that can be exploited by attackers.
What is the difference between CVE and vulnerability database
CVE – Common Vulnerabilities and Exposures (CVE) is a list of publicly disclosed vulnerabilities and exposures that is maintained by MITRE. NVD – The National Vulnerability Database (NVD) is a database, maintained by NIST, that is fully synchronized with the MITRE CVE list.
What are the 4 types of vulnerability
According to the different types of losses, the vulnerability can be defined as physical vulnerability, economic vulnerability, social vulnerability and environmental vulnerability.
What are the 4 main types of vulnerabilities
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
What does in vulnerability mean
Vulnerability is the quality of being easily hurt or attacked. Some seniors think it's funny to pick on the ninth graders because of their vulnerability. Vulnerability comes from the Latin word for "wound," vulnus. Vulnerability is the state of being open to injury, or appearing as if you are.