What is vulnerability in disaster management
What is Vulnerability. Vulnerability describes the characteristics and circumstances of a community, system or asset that make it susceptible to the damaging effects of a hazard. There are many aspects of vulnerability, arising from various physical, social, economic, and environmental factors.
What are the 4 types of vulnerability in disaster management
In the table below four different types of vulnerability have been identified, Human-social, Physical, Economic and Environmental and their associated direct and indirect losses.
What is vulnerability in disaster and example
Vulnerability is the inability to resist a hazard or to respond when a disaster has occurred. For instance, people who live on plains are more vulnerable to floods than people who live higher up.
What is risk identification in disaster
A qualitative or quantitative approach to determine the nature and extent of disaster risk by analysing potential hazards and evaluating existing conditions of exposure and vulnerability that together could harm people, property, services, livelihoods and the environment on which they depend.
Why is vulnerability important in disaster management
Vulnerable groups find it hardest to reconstruct their livelihoods following a disaster, and this in turn makes them more vulnerable to the effects of subsequent hazard events. Consequently, we have to reduce vulnerability in order to reduce disaster risk.
Why is vulnerability important in disasters
Vulnerability represents the susceptibility of a given population to harmful effects from exposure to hazardous events. It directly affects disaster preparation, response, and recovery [4]. Hazardous event can directly or indirectly affect the health status of an individual or a population.
What are the 4 stages of identifying vulnerabilities
A 4-Step Vulnerability Management ProcessIdentification. A vulnerability management system continuously scans an environment against one or more databases of known vulnerabilities, with the objective of identifying vulnerable assets.Prioritization.Remediation.Verification and Reporting.
What are the 4 stages of vulnerability
4 Steps of the Vulnerability Management ProcessPerform Vulnerability Scan.Assess Vulnerability Risk.Prioritize & Address Vulnerabilities.Continuous Vulnerability Management.
What are 5 example of vulnerability
To illustrate the principles above, here are 11 specific examples of vulnerability: Telling someone when they've upset you, respectfully but honestly. Sharing something personal about yourself that you normally wouldn't. Admitting to mistakes you have made in the past.
What are 3 examples of vulnerability
Different types of Security Vulnerabilities:Unpatched Software.Misconfiguration.Weak Credentials.Easy-to-phish-users.Trust Relationship.Compromised Credentials.Malicious Insider.Missing/Poor Encryption.
What is risk identification and why is it important
Risk identification is the process of documenting any risks that could keep an organization or program from reaching its objective. It's the first step in the risk management process, which is designed to help companies understand and plan for potential risks.
What are the 5 components of risk identification
There are several ways to categorize an effective risk management process's constituent elements, but at the very least it should incorporate the following risk management components.Risk Identification.Risk Analysis.Response Planning.Risk Mitigation.Risk Monitoring.
What is the importance of vulnerability identification
Vulnerability assessments can identify vulnerabilities in applications, systems, and network devices that attackers could exploit to gain unauthorized access to sensitive data. Organizations can reduce the risk of data breaches by identifying these vulnerabilities and protecting sensitive information.
Why is it important to identify vulnerability
A vulnerability assessment provides an organization with details on any security weaknesses in its environment. It also provides direction on how to assess the risks associated with those weaknesses.
What is vulnerability and why is it important
Vulnerability is an opportunity to grow as a person and a way to find deep satisfaction in your relationships. Opening up and relinquishing your fears of rejection helps builds trust and honesty with others, fosters empathy, and builds stronger bonds.
Why is vulnerability important in pre disaster management
Answer: Vulnerability and risk assessment is essential to take up pre-disaster management steps. Prevention, Mitigation and Preparedness can only be developed properly if we know the underlying disaster risks. … Mapping of the more disaster prone areas.
What are the methods of identifying vulnerabilities
Network-based vulnerability assessments typically involve specialized software tools and techniques that scan the network for vulnerabilities. These tools may use various methods to identify vulnerabilities, such as port scanning, vulnerability scanning, password cracking, and network mapping.
What are the four vulnerability identification and assessment
A vulnerability assessment is an examination of vulnerabilities in IT systems at a certain point in time with the goal of detecting system flaws before hackers may exploit them. Security assessments come in four types: application scans, network or wireless assessment, database assessment, and host assessment.
What are the 5 steps of vulnerability management
There are five main stages in the vulnerability management cycle include:Assess.Prioritize.Act.Reassess.Improve.
What are the 3 components of vulnerability assessment
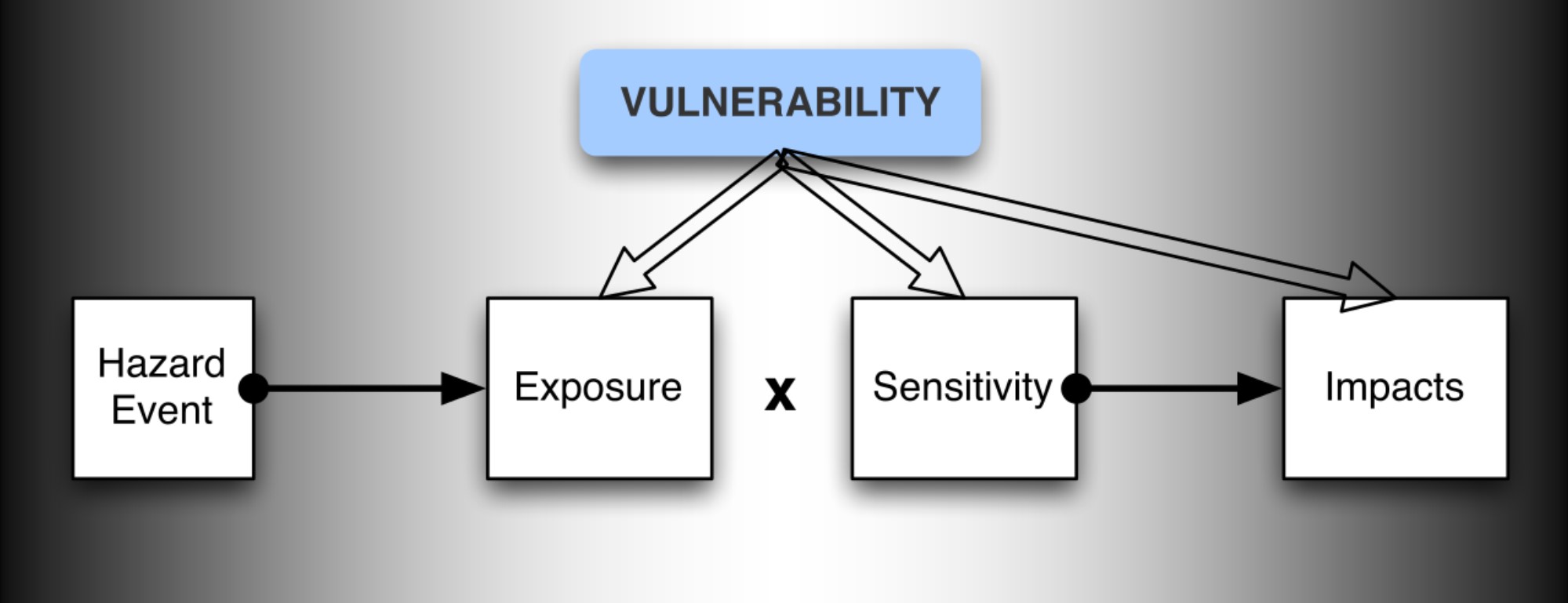
There are three dimensions of vulnerability: exposure, sensitivity, and adaptive capacity.
What are 3 example of vulnerabilities
Vulnerability Examples
Any susceptibility to humidity, dust, soiling, natural disaster, poor encryption, or firmware vulnerability.
What are the 3 types of vulnerability explain each type
The different types of vulnerability
According to the different types of losses, the vulnerability can be defined as physical vulnerability, economic vulnerability, social vulnerability and environmental vulnerability.
What are the 5 types of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What is the importance of risk identification in disaster management
Risk identification deals with the factors that cause disasters, namely: natural hazards; the exposure of people, infrastructure and eco- nomic activities to these hazards; and the vulnerabilities that the exposed elements may possess that cause them to be damaged or lost when a hazard strikes.
What is the importance of risk identification and vulnerabilities to assets in risk management
3. Why is identification of risks, through a listing of assets and their vulnerabilities, so important to the risk management process Answer: It is important because management needs to know the value of each company asset and what losses will be incurred if an asset is compromised.