Which versions of Bash are vulnerable to shellshock
In this tutorial, we'll talk about the shellshock bug. It's a vulnerability that affects GNU Bash from version 1.14 to those lower than 4.3.
What is the CVE vulnerability of Shellshock
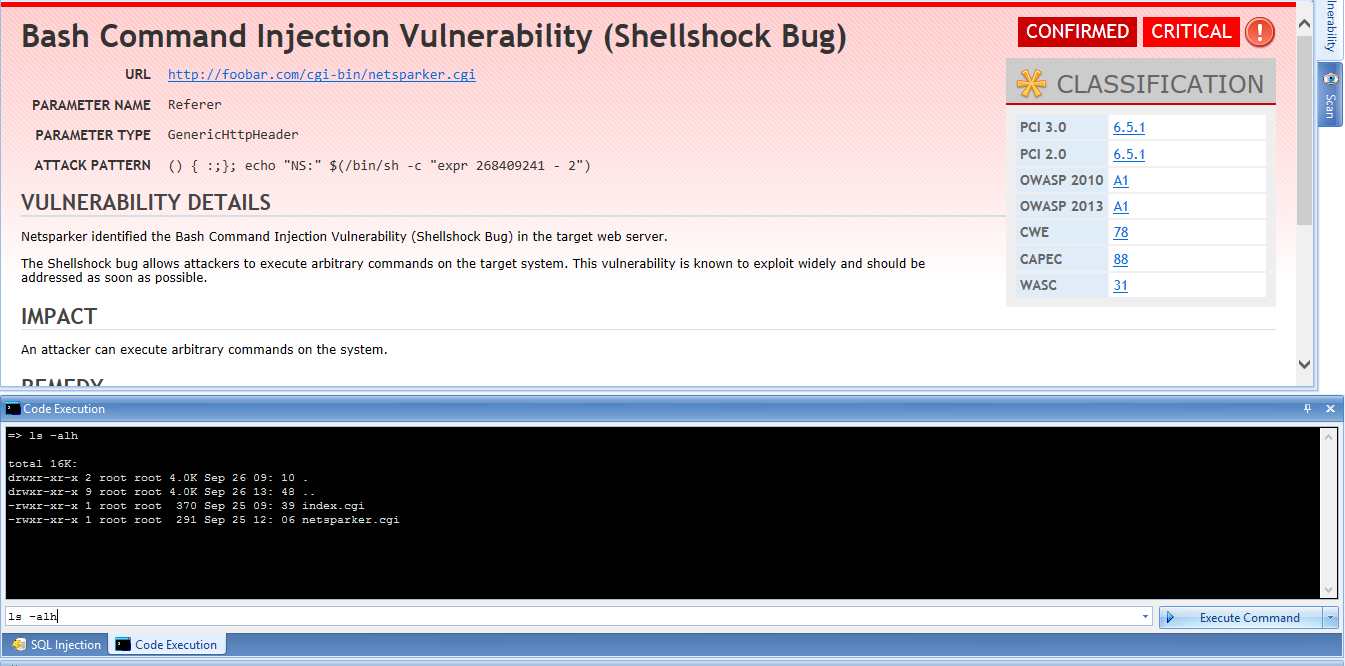
What is Shellshock The Shellshock Vulnerability (CVE-2014-6271) is a serious vulnerability in Bash on Linux. According to RedHat, “A flaw was found in the way Bash (aka bourne-again shell) evaluated certain specially crafted environment variables.
What is unique about Bash bug vulnerability
An attacker can simply execute system level commands, with the same privileges as the affected services. The flaw allows an attacker to remotely attach a malicious executable to a variable that is executed when Bash is invoked.
What software was affected by the shellshock bug
Bash
The Shellshock bug affects Bash, a program that various Unix-based systems use to execute command lines and command scripts. It is often installed as the system's default command-line interface.
Is Windows vulnerable to Shellshock
Explaining the “Shell Shock” bug
Bash is a commonly used “shell” environment used for command line operations in the Linux and Mac operating systems – Windows systems are not affected.
Who developed the exploit for CVE 2014 6271
Stéphane Chazelas
On 12 September 2014, Stéphane Chazelas informed Bash's maintainer Chet Ramey of his discovery of the original bug, which he called "Bashdoor". Working with security experts, Mr. Chazelas developed a patch (fix) for the issue, which by then had been assigned the vulnerability identifier CVE- 2014-6271.
What are the known vulnerabilities of ClamAV
On Feb 15, 2023, the following vulnerability in the ClamAV scanning library was disclosed: A vulnerability in the HFS+ partition file parser of ClamAV versions 1.0. 0 and earlier, 0.105. 1 and earlier, and 0.103. 7 and earlier could allow an unauthenticated, remote attacker to execute arbitrary code.
What software was affected by log 4 shell
Affected commercial services include Amazon Web Services, Cloudflare, iCloud, Minecraft: Java Edition, Steam, Tencent QQ and many others.
Is Windows 7 a vulnerability
Since the start of this year, there have been 47 vulnerabilities discovered in Windows 7, according to the U.S.'s National Institute of Standards and Technology Vulnerability Database. There are even more security issues with third-party software running on Windows 7.
What caused shellshock vulnerability
This deadly bug originates from the Bash (Bourne Again Shell) which is the default command-line interface on all Linux, Unix, and Mac-based operating systems. The Shellshock vulnerability was first detected some 30 years ago but was not classified as an official and public threat until September of 2014.
What significant vulnerability was discovered in OpenSSL in 2014
Heartbleed
Heartbleed is a security bug in some outdated versions of the OpenSSL cryptography library, which is a widely used implementation of the Transport Layer Security (TLS) protocol. It was introduced into the software in 2012 and publicly disclosed in April 2014.
What is the most common software vulnerability
The most common software security vulnerabilities include:Missing data encryption.OS command injection.SQL injection.Buffer overflow.Missing authentication for critical function.Missing authorization.Unrestricted upload of dangerous file types.Reliance on untrusted inputs in a security decision.
What piece of software has the most vulnerabilities
Top 50 Products By Total Number Of "Distinct" Vulnerabilities
| Product Name | Number of Vulnerabilities | |
|---|---|---|
| 1 | Debian Linux | 8190 |
| 2 | Android | 5238 |
| 3 | Fedora | 4517 |
| 4 | Ubuntu Linux | 3962 |
What products are affected by Log4Shell
F-Secure. On both Windows and Linux, Log4Shell affects several F-Secure products, including Policy Manager (only the Policy Manager Server component), Policy Manager Proxy, Endpoint Proxy, and Elements Connector.
What versions are affected by Log4Shell vulnerability
Technical Details. The CVE-2021-44228 RCE vulnerability—affecting Apache's Log4j library, versions 2.0-beta9 to 2.14. 1—exists in the action the Java Naming and Directory Interface (JNDI) takes to resolve variables.
Is Windows 7 vulnerable to ransomware
Leaving Windows 7 in Production Puts You at High Risk of Ransomware Attack. Microsoft end-of-support for Windows 7 means systems will remain unpatched, creating an opportunity for future ransomware attacks to wreak havoc.
Can I still use Windows 7 in 2023
Yes, Windows 7 can still be used after Jan. 10, 2023. However, since no security updates will be provided to the OS, it can easily be exploited by threat actors if vulnerabilities arise in it.
Who was affected by shell shock
By December 1914, as many as 10% of British officers and 4% of enlisted men were experiencing "nervous and mental shock". The term "shell shock" was coined during the Battle of Loos to reflect an assumed link between the symptoms and the effects of explosions from artillery shells.
Which software was vulnerable to the exploit CVE 2014 0160
OpenSSL
OpenSSL 'Heartbleed' vulnerability (CVE-2014-0160)
What are the vulnerabilities of Microsoft OpenSSL
Microsoft has chimed in on the highly visible OpenSSL security risks that emerged last week, and advises users start applying fixes based on OpenSSL's recent patches. The issue started on Oct. 25 when two vulnerabilities (CVE-2022-3602 and CVE-2022-3786) affecting OpenSSL version 3.0. 0 and later emerged.
What was the first software vulnerability
1965: First Reported Vulnerability
William D. Mathews from MIT, found a flaw in a Multics CTSS running on an IBM 7094, which disclosed the contents of the password file. That flaw is probably the first reported vulnerability in a computer system.
What systems are most vulnerable to cyber risks
Vulnerable systems are social media platforms, including their respective accounts and groups, mobile devices and remote servers.
What is software that is vulnerable
A software vulnerability is a weakness or gap in security checks within a software component that can allow an attacker to perform unauthorised actions. Software vulnerabilities in this context relate to how the software has been built as opposed to how it has been configured and implemented.
Which Windows OS is most vulnerable
Users can also be at risk because of security vulnerabilities in the applications they use or through attacks on connected devices. As a result, Windows 10 is considered the least secure operating system.
What software was affected by Log4Shell
Affected commercial services include Amazon Web Services, Cloudflare, iCloud, Minecraft: Java Edition, Steam, Tencent QQ and many others.