What is shellshock exploitation
In layman's terms, Shellshock is a vulnerability that allows systems containing a vulnerable version of Bash to be exploited to execute commands with higher privileges. This allows attackers to potentially take over that system.
What is the vulnerability of Shellshock
What is the Shellshock Remote Code Execution Vulnerability It is a security bug in the Unix Bash shell that causes Bash to execute bash commands from environment variables unintentionally.
What is the use of Shellshock
Shellshock is an arbitrary code execution vulnerability that offers a way for users of a system to execute commands that should be unavailable to them.
What is exploit the Bash bug or shellshock vulnerability
Shellshock is a security bug causing Bash to execute commands from environment variables unintentionally. In other words if exploited the vulnerability allows the attacker to remotely issue commands on the server, also known as remote code execution.
How do attackers exploit shellshock
Attackers can exploit the shellshock vulnerability in many ways. For instance, they can use ssh, web servers, DHCP, and web applications on vulnerable servers. Let's discuss these examples further. The ForceCommand feature in OpenSSH is a fixed command executed every time the user logs into the system.
What is Bash bug or shellshock vulnerability
Shellshock is a security bug causing Bash to execute commands from environment variables unintentionally. In other words if exploited the vulnerability allows the attacker to remotely issue commands on the server, also known as remote code execution.
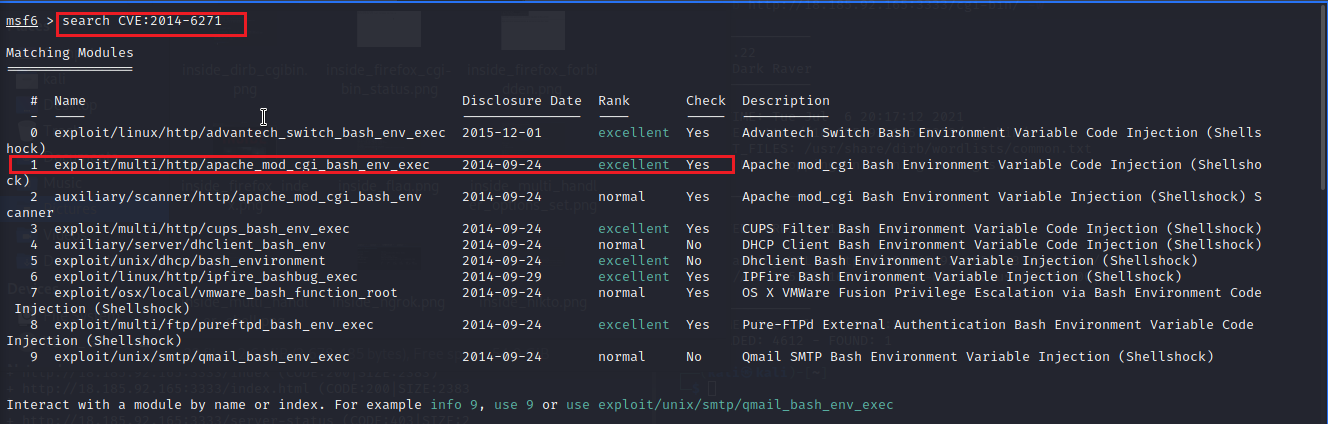
What is Linux exploit CVE 2014 6271
The Shellshock Vulnerability (CVE-2014-6271) is a serious vulnerability in Bash on Linux. According to RedHat, “A flaw was found in the way Bash (aka bourne-again shell) evaluated certain specially crafted environment variables.
Is a reverse shell an exploit
Reverse shell is a process attackers use to gain access to remote systems and exploit remote code execution (RCE) vulnerabilities present in these systems. Before we explore reverse shell, we need to establish what bind shell is.
What is vulnerability exploitation attacks
A vulnerability in security refers to a weakness or opportunity in an information system that cybercriminals can exploit and gain unauthorized access to a computer system. Vulnerabilities weaken systems and open the door to malicious attacks.
Is reverse shell a vulnerability
Reverse shell is a process attackers use to gain access to remote systems and exploit remote code execution (RCE) vulnerabilities present in these systems.
What does CVE mean in exploit
Common Vulnerabilities and Exposures (CVE) is a database of publicly disclosed information security issues. A CVE number uniquely identifies one vulnerability from the list.
What type of vulnerability is Log4Shell
Log4Shell is a software vulnerability in Apache Log4j 2, a popular Java library for logging error messages in applications. The vulnerability, published as CVE-2021-44228, enables a remote attacker to take control of a device on the internet if the device is running certain versions of Log4j 2.
Is a reverse shell a backdoor
Reverse shell attacks happen when an attacker creates a backdoor into a server through some means of remote access. The attacker uses that backdoor to gain access to the server and execute commands as if they were logged in on the server itself. Hackers execute reverse shell attacks using Python, Java, or Node.
What is a passive exploit
A passive attack attempts to access your data via hackers monitoring and scanning your systems for vulnerabilities that will give them this kind of access. This type of attack does not involve data alterations, which, generally, makes it very difficult to detect.
What are the 4 types of vulnerability
According to the different types of losses, the vulnerability can be defined as physical vulnerability, economic vulnerability, social vulnerability and environmental vulnerability.
Is reverse shell a backdoor
Reverse shell attacks happen when an attacker creates a backdoor into a server through some means of remote access. The attacker uses that backdoor to gain access to the server and execute commands as if they were logged in on the server itself. Hackers execute reverse shell attacks using Python, Java, or Node.
Is a reverse shell malware
Reverse shell connections are often malicious unless you set them up for the explicit purpose of remote administration. From a server perspective, it is difficult to block all reverse shell connections when using a networked system such as a server.
What type of vulnerability is CVE
CVE, short for Common Vulnerabilities and Exposures, is a list of publicly disclosed computer security flaws. When someone refers to a CVE, they mean a security flaw that's been assigned a CVE ID number. Security advisories issued by vendors and researchers almost always mention at least one CVE ID.
Is CVE a vulnerability
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
Is Log4j an exploit
Log4j Exploit Storyboard
The Apache Log4j vulnerability, CVE-2021-44228 (https://nvd.nist.gov/vuln/detail/CVE-2021-44228), affects a large number of systems, and attackers are currently exploiting this vulnerability for internet-connected systems across the world.
What is Log4j type vulnerabilities
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
What is a backdoor exploit
In the context of an attack, backdoors are hidden mechanisms attackers use to access a system without authentication. However, vendors sometimes create backdoors for legitimate purposes, such as restoring a user's lost password or providing government entities with access to encrypted data.
What is an active exploit
Active exploits will exploit a specific host, run until completion, and then exit. Brute-force modules will exit when a shell opens from the victim. Module execution stops if an error is encountered.
What are the active attacks
Active attacks:
Active attacks involve the attacker taking direct action against the target system or network, and can be more dangerous than passive attacks, which involve simply monitoring or eavesdropping on a system or network. Types of active attacks are as follows: Masquerade. Modification of messages. …
What are the 5 categories of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.