Which Bash versions are vulnerable to Shellshock
In this tutorial, we'll talk about the shellshock bug. It's a vulnerability that affects GNU Bash from version 1.14 to those lower than 4.3. This bug affects Unix-based OSes, including Linux, BSD, and macOS systems.
What Bash versions are vulnerable to Shellshock CVE 2014 6271 )
The critical Bash Bug vulnerability, also dubbed Shellshock, affects versions GNU Bash versions ranging from 1.14 through 4.3. A threat actor could exploit it to execute shell commands remotely on a targeted machine using specifically crafted variables.
What feature of Bash is being exploited in the Shellshock attack
Shellshock is an arbitrary code execution vulnerability that offers a way for users of a system to execute commands that should be unavailable to them. This happens through Bash's "function export" feature, whereby one Bash process can share command scripts with other Bash processes that it executes.
What type of attack is CVE 2014 6271
The Shellshock Vulnerability (CVE-2014-6271) is a serious vulnerability in Bash on Linux. According to RedHat, “A flaw was found in the way Bash (aka bourne-again shell) evaluated certain specially crafted environment variables.
Which version of SSH is vulnerable
OpenSSH clients between versions 5.4 and 7.1 are vulnerable to information disclosure that may allow a malicious server to retrieve information including under some circumstances, user's private keys.
What is CVE 2014 6278
GNU Bash through 4.3 bash43-026 does not properly parse function definitions in the values of environment variables, which allows remote attackers to execute arbitrary commands via a crafted environment, as demonstrated by vectors involving the ForceCommand feature in OpenSSH sshd, the mod_cgi and mod_cgid modules in …
What is the most common method to exploit the bash bug or shellshock vulnerability
Explanation. The correct answer is CGI (Common Gateway Interface). "The most common being web servers using CGI environment.”
Which versions of Log4j CVE are vulnerable
Technical Details. The CVE-2021-44228 RCE vulnerability—affecting Apache's Log4j library, versions 2.0-beta9 to 2.14. 1—exists in the action the Java Naming and Directory Interface (JNDI) takes to resolve variables.
What is CVE version of discovered vulnerability
Common Vulnerabilities and Exposures
Common Vulnerabilities and Exposures (CVE) is a database of publicly disclosed information security issues. A CVE number uniquely identifies one vulnerability from the list.
Is SSH version 2 secure
SSH1 and SSH2 encrypt at different parts of the packets, and SSH1 uses server and host keys to authenticate systems where SSH2 only uses host keys. SSH2 is a complete rewrite of the protocol, and it does not use the same networking implementation that SSH1 does. Also, SSH2 is more secure.
Is OpenSSH 7.4 vulnerable
It is, therefore, affected by an information disclosure vulnerability : – An unspecified timing flaw exists in the CBC padding oracle countermeasures, within the ssh and sshd functions, that allows an unauthenticated, remote attacker to disclose potentially sensitive information.
What is CVE 2014 0224
The CCS Injection Vulnerability (CVE-2014-0224) is a serious vulnerability in the popular OpenSSL cryptographic software library. OpenSSL is an implementation of the SSL/TLS encryption protocol used to protect the privacy of Internet communication.
What is CVE 2014 6277
Description. The remote host is running a version of Bash that is vulnerable to command injection via environment variable manipulation. Depending on the configuration of the system, an attacker could remotely execute arbitrary code.
How does Bash shellshock work
It is a security bug in the Unix Bash shell that causes Bash to execute bash commands from environment variables unintentionally. If this vulnerability is successfully exploited, an attacker can remotely issue commands on the target host, i.e., remote code execution (RCE).
Is Windows vulnerable to shellshock
Explaining the “Shell Shock” bug
Bash is a commonly used “shell” environment used for command line operations in the Linux and Mac operating systems – Windows systems are not affected.
Is Log4j 2.16 still vulnerable
December 20, 2021
Log4j 2.17 has been released to address a Denial of Service (DoS) vulnerability found in v2. 16 and earlier. Log4j 2.16 and earlier does not always protect from infinite recursion in lookup evaluation, which can lead to DoS attacks. This is considered a High (7.5) vulnerability on the CVSS scale.
Is Log4j 2.17 0 vulnerable
3 or 2.17. 0: from these versions onwards, only the JAVA protocol is supported in JNDI connections. Note that only the log4j-core JAR file is impacted by this vulnerability. Applications using only the log4j-api JAR file without the log4j-core JAR file are not impacted by this vulnerability.
What is the CVE number of the vulnerability that was solved in version 2.4 51
CVE-2021-41773
On October 7, 2021, the Apache Software Foundation released Apache HTTP Server version 2.4. 51 to address Path Traversal and Remote Code Execution vulnerabilities (CVE-2021-41773, CVE-2021-42013) in Apache HTTP Server 2.4. 49 and 2.4. 50.
Why is SSH v2 better than v1
SSH1 and SSH2 encrypt at different parts of the packets, and SSH1 uses server and host keys to authenticate systems where SSH2 only uses host keys. SSH2 is a complete rewrite of the protocol, and it does not use the same networking implementation that SSH1 does. Also, SSH2 is more secure.
Is OpenSSH 7.2 p2 vulnerable
A vulnerability classified as problematic has been found in OpenSSH 7.2p2 (Connectivity Software). Affected is an unknown functionality of the component Authentication. The manipulation of the argument Password with an unknown input leads to a information disclosure vulnerability (Username).
What version of OpenSSH is vulnerable
OpenSSH clients between versions 5.4 and 7.1 are vulnerable to information disclosure that may allow a malicious server to retrieve information including under some circumstances, user's private keys.
What is CVE 2014 4078
IIS Security Feature Bypass Vulnerability – CVE-2014-4078
A security feature bypass vulnerability exists in Microsoft Information Services (IIS) that is caused when incoming web requests are not properly compared against the "IP and domain restriction" filtering list.
What is CVE 2013 2566
The RC4 algorithm, as used in the TLS protocol and SSL protocol, has many single-byte biases, which makes it easier for remote attackers to conduct plaintext-recovery attacks via statistical analysis of ciphertext in a large number of sessions that use the same plaintext.
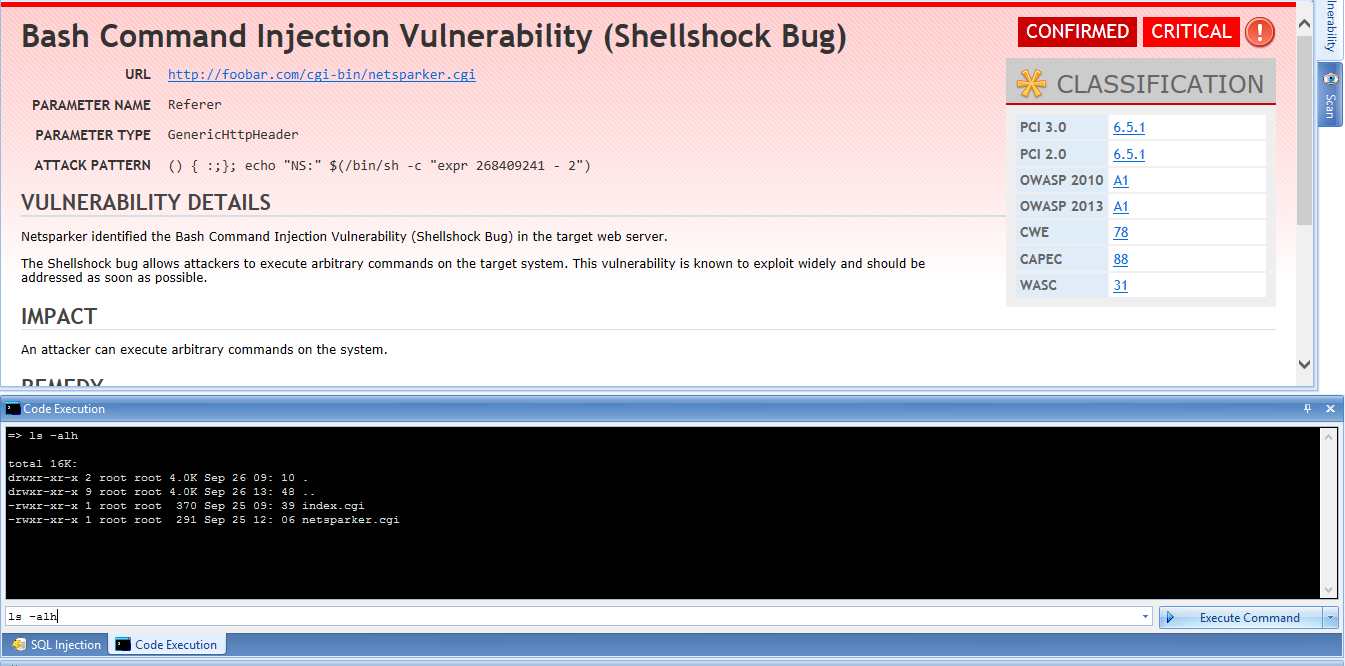
How do you detect vulnerability in shellshock
To detect this vulnerability the script executes a command that prints a random string and then attempts to find it inside the response body. Web apps that don't print back information won't be detected with this method. By default the script injects the payload in the HTTP headers User-Agent, Cookie, and Referer.
Does shellshock still work
Although the ShellShock vulnerability, CVE-2014-6271, was discovered in 2014, it is known to still exist on a large number of servers in the world. The vulnerability was updated (CVE-2014-7169) soon after and has been modified up until 2018. The main reason Shellshock is still in use is no shocker.