What vulnerabilities does Nessus scan for
Nessus can scan these vulnerabilities and exposures:Vulnerabilities that could allow unauthorized control or access to sensitive data on a system.Misconfiguration (e.g. open mail relay)Denials of service (Dos) vulnerabilities.Default passwords, a few common passwords, and blank/absent passwords on some system accounts.
What can be identified by Nessus
Nessus identifies software flaws, missing patches, malware, denial-of-service vulnerabilities, default passwords and misconfiguration errors, among other potential flaws.
Can Nessus detect log4j vulnerability
When scanning with Credentials and Thorough enabled, Nessus will show the file that are vulnerable. Nessus is not checking all your application code for the use of the log4j function. If you are sure you are not using log4j, then remove it from your environment and reduce your attack surface.
Can Nessus exploit vulnerabilities
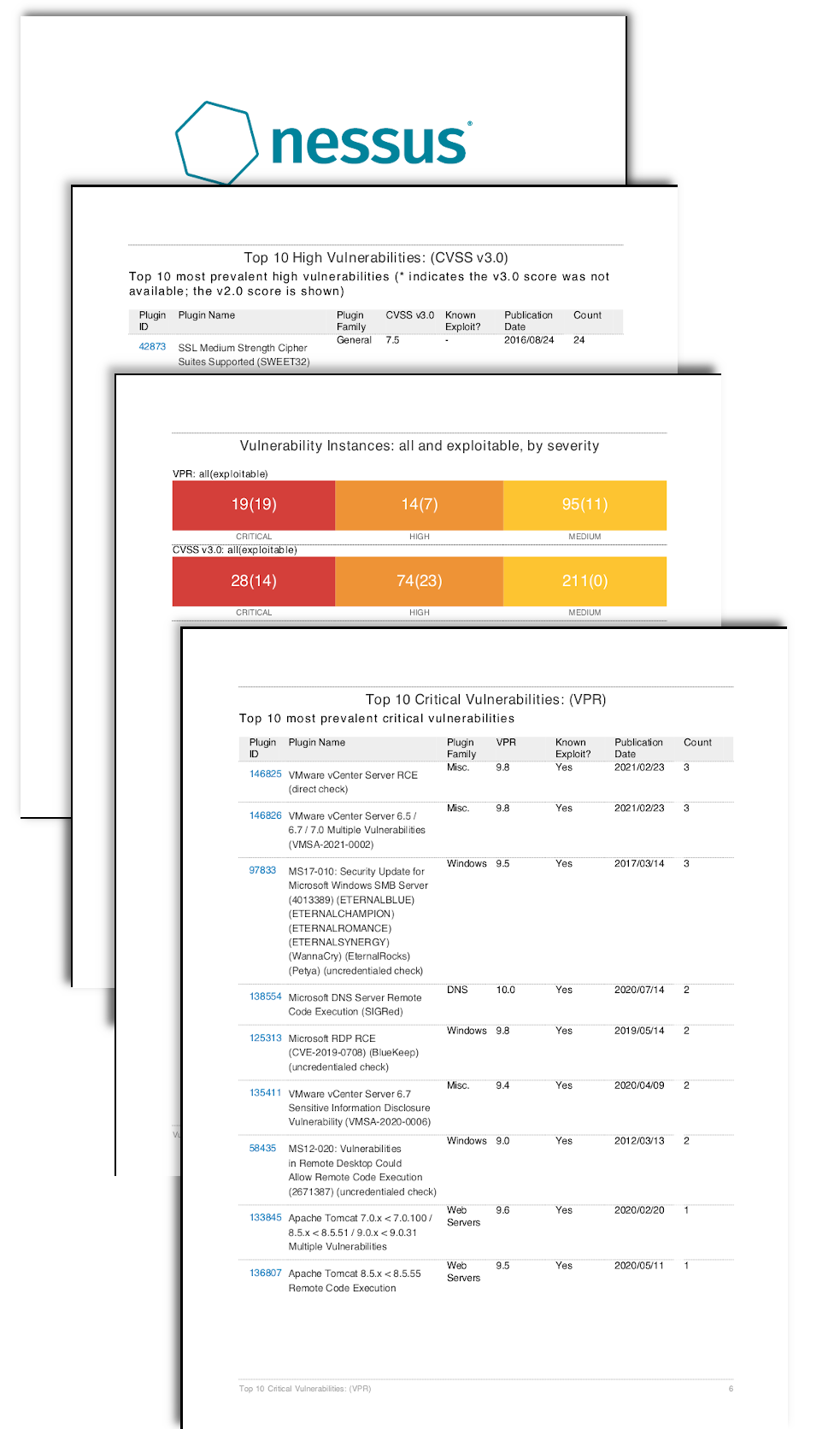
Nessus identifies exploitable vulnerabilities present in your scan results. The report contains two tables which bring focus to the exploitable vulnerabilities.
Does Nessus scan for CVE
All Nessus and Passive Vulnerability Scanner plugins receive mappings to CVE, Bugtraq and other identifiers.
Can Nessus detect malware
Nessus allows the ability to utilize a text file with custom hashes to identify known bad files so they can be flagged as malicious during scans. Custom files are supported by: Plugin 88962: Malicious File Detection: User Defined Malware.
What Cannot be identified by Nessus
Nessus cannot identify incorrect IP addresses.
Does Nessus scan for viruses
Its also provides a plug-in interface, and many free plug-ins are available from the Nessus plug-in site. These plugs are often specific to detecting a common virus or vulnerability. – Up to date information about new vulnerabilities and attacks.
Is Nessus a good vulnerability scanner
Nessus is the most widely-used vulnerability scanner in the world. It looks for more than 57,000 possible security weaknesses from an external viewpoint. These weaknesses are known as “exploits” and they can give hackers a way into a system.
Can Nessus be used by hackers
Nessus has become the de facto standard in vulnerability scanners, and every white hat hacker should be familiar with it. It is capable of finding known vulnerabilities, but its limitation, like all vulnerability scanners, are false positives.
What type of vulnerability will not be found by a vulnerability scanner
Vulnerability scanners cannot detect vulnerabilities for which they do not have a test, plug-in, or signature. Signatures often include version numbers, service fingerprints, or configuration data.
Which vulnerability cannot be discovered
Business logic vulnerabilities:
These vulnerabilities cannot be found through automated scanning.
What are common vulnerabilities that scanners will report
Vulnerability scanners are automated tools that scan web applications to look for security vulnerabilities. They test web applications for common security problems such as cross-site scripting (XSS), SQL injection, and cross-site request forgery (CSRF).
What types of vulnerabilities are not identified by non-credentialed scans
Credential-based vs.
Unfortunately, non-credentialed scans do not provide deeper insight into application and operating system vulnerabilities not exposed to the network, or those vulnerabilities behind a firewall. It provides a false hope that the system is safe.
What are the 4 main types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military. In relation to hazards and disasters, vulnerability is a concept that links the relationship that people have with their environment to social forces and institutions and the cultural values that sustain and contest them.
What are the 4 main types of vulnerabilities
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
What are 3 example of vulnerabilities
Vulnerability Examples
Any susceptibility to humidity, dust, soiling, natural disaster, poor encryption, or firmware vulnerability.
What are the 5 categories of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What are 5 example of vulnerability
To illustrate the principles above, here are 11 specific examples of vulnerability: Telling someone when they've upset you, respectfully but honestly. Sharing something personal about yourself that you normally wouldn't. Admitting to mistakes you have made in the past.
What are the 5 types of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What are the 4 main types of security vulnerability
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
What are the 4 stages of identifying vulnerabilities
A 4-Step Vulnerability Management ProcessIdentification. A vulnerability management system continuously scans an environment against one or more databases of known vulnerabilities, with the objective of identifying vulnerable assets.Prioritization.Remediation.Verification and Reporting.