When should you check for vulnerabilities in the software you maintain
All an attacker needs is just one vulnerability to get a foothold in your network. That's why at a minimum, you should scan your network at least once a month and patch or remediate identified vulnerabilities. Although some compliance requirements require you to scan your network quarterly, that's not often enough.
What is the ideal time for performing vulnerability scans for Windows environment
Most IT professionals agree that vulnerability scans should be conducted quarterly, and some say that to be even better-protected vulnerability scans should be run monthly.
In which mode should vulnerability scanning be performed
Vulnerability scanning can be performed manually or via automated efforts with automated scanner tools, which analyze various areas of a computer system to look for vulnerabilities such as misconfigurations, unsecured/open ports, potential vulnerability to malware infections, and so on.
When would you want to use the Nessus vulnerability scanner
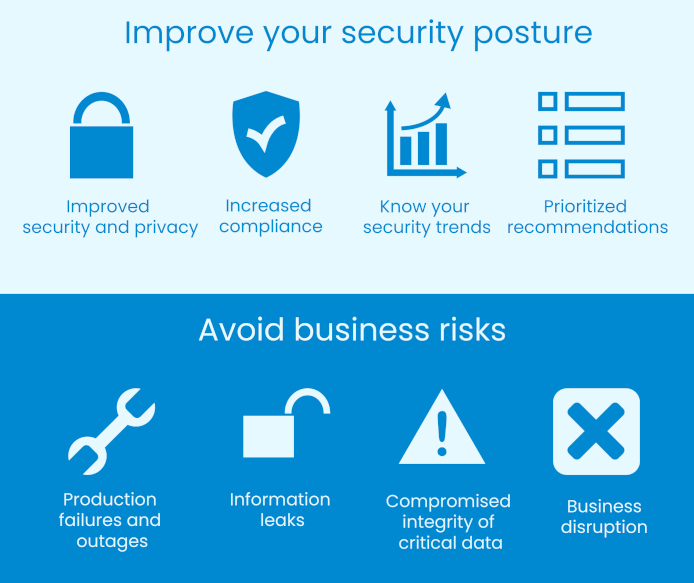
Benefits of Nessus vulnerability scanner
Organizations need to be aware of these vulnerabilities and act proactively to prevent them from harming their assets. Nessus provides a fast, user-friendly way to find and fix vulnerabilities in many kinds of IT assets, including cloud-based and virtualized resources.
At what stage of software development is security checked
Phase Three
Phase Three: Test
Testing is an essential part of any software development lifecycle. In addition to security testing, performance tests, unit tests, and non-functional testing such as interface testing all take place in this phase.
What are the 4 stages of identifying vulnerabilities
A 4-Step Vulnerability Management ProcessIdentification. A vulnerability management system continuously scans an environment against one or more databases of known vulnerabilities, with the objective of identifying vulnerable assets.Prioritization.Remediation.Verification and Reporting.
Why would you run vulnerability scans
Vulnerability scanning lets you take a proactive approach to close any gaps and maintain strong security for your systems, data, employees, and customers. Data breaches are often the result of unpatched vulnerabilities, so identifying and eliminating these security gaps, removes that attack vector.
How often should you run a Nessus scan
Daily
Daily scans and passive monitoring can ensure that all data is within 24 hours. If a network is so large that it takes a few days or even a week to complete a scan, the data is less useful, but better than no data at all.
Why should you do vulnerability scanning
Vulnerability scanning is important because of the many cybersecurity risks within a company. Vulnerabilities within a company's IT infrastructure can be breached by cybercriminals if those weaknesses go unnoticed. Despite the protective measures they have in place, enterprises experience data breaches.
In which stage of SDLC we should start testing
When to Start Testing An early start to testing reduces the cost and time to rework and produce error-free software that is delivered to the client. However in Software Development Life Cycle (SDLC), testing can be started from the Requirements Gathering phase and continued till the deployment of the software.
In which phase of SDLC should security be integrated
A better practice is to integrate security activities across the SDLC–from the planning phase to release. This helps discover (and fix!) defects close to the time they're introduced.
What are the 5 phases of vulnerability assessment
The Five Phases of Penetration Testing. There are five penetration testing phases: reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. Let's take a closer look at the 5 Penetration Testing phases.
What are the 3 criteria for assessing vulnerability
The assessment framework involves three dimensions: engagement, intent and capability, which are considered separately.
What is vulnerability testing and why is IT done
Definition. A vulnerability assessment is the testing process used to identify and assign severity levels to as many security defects as possible in a given timeframe. This process may involve automated and manual techniques with varying degrees of rigor and an emphasis on comprehensive coverage.
Why do we need vulnerability
Vulnerability fosters good emotional and mental health. Vulnerability also is a sign of courage. We become more resilient and brave when we embrace who we truly are and what we are feeling. Lastly, being vulnerable can help us foster better connections and relationships with others.
How often do you think you would want to run a vulnerability scan on corporate servers
Our recommendation for good cyber hygiene for most businesses, is to use a vulnerability scanner on your external facing infrastructure on at least a monthly basis, to allow you to keep one step ahead of these nasty surprises.
How long should a Nessus scan take
Most devices between 20min – 40min, however there are a few which take over 240 minutes. Nessus will slow down its scan if the target device is busy, or the network is getting congested, so its not really a figure that you can always state this is how long it will take.
Why is vulnerability necessary
Vulnerability may help you express your feelings, whether they're positive or negative. New research on vulnerability and coping with stress found that vulnerability was associated with higher levels of emotional expression and social support.
How do you use vulnerability scanning
7 TIPS TO MANAGE VULNERABILITIES.CONFIRM YOUR SCOPE.RUN EXTERNAL VULNERABILITY SCANS.RUN INTERNAL VULNERABILITY SCANS.INDEPENDENT AND QUALIFIED TESTING.REGULARLY RUN VULNERABILITY SCANS.RUN SCANS AFTER SIGNIFICANT NETWORK CHANGES.ESTABLISH A TOP-DOWN APPROACH.
Which phase in SDLC is most important
Requirements gathering and analysis
Requirements gathering and analysis is the most crucial phase of the SDLC. Without understanding the requirements, no project team can create a solution that is appreciated by customers.
In which phase of SDLC risk analysis is done
requirements stage
The first step to risk analysis at the requirements stage is to break down requirements into three simple categories: must haves, important to haves, and nice but unnecessary.
When should security testing be done in SDLC
Security applies at every phase of the software development life cycle (SDLC) and needs to be at the forefront of your developers' minds as they implement your software's requirements.
In which phase of secure SDLC is the code review and vulnerability analysis done
In the SDLC (Software Development Life Cycle) process [Figure-1], the secure code review process comes under the Development Phase, which means that when the application is being coded by the developers, they can do self-code review or a security analyst can perform the code review, or both.
What are the 4 stages of vulnerability
4 Steps of the Vulnerability Management ProcessPerform Vulnerability Scan.Assess Vulnerability Risk.Prioritize & Address Vulnerabilities.Continuous Vulnerability Management.
What is vulnerability assessment and why do we need IT
Definition. A vulnerability assessment is the testing process used to identify and assign severity levels to as many security defects as possible in a given timeframe. This process may involve automated and manual techniques with varying degrees of rigor and an emphasis on comprehensive coverage.