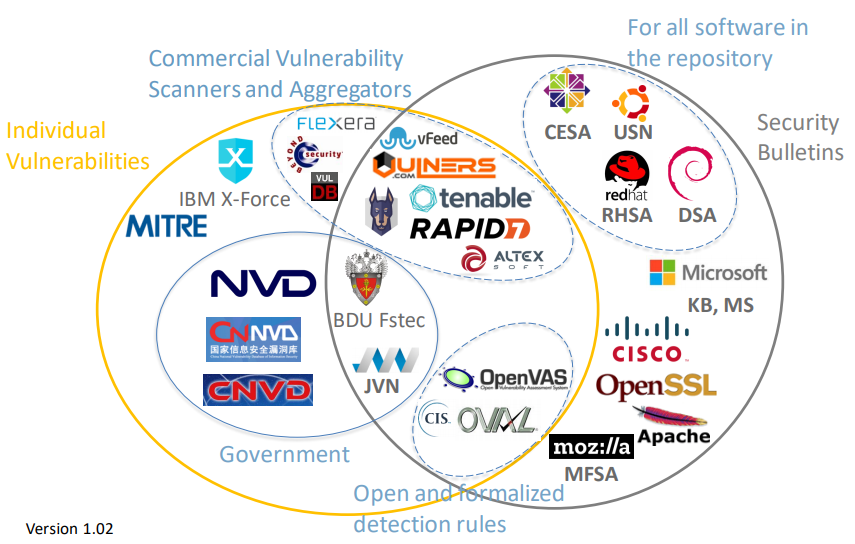
What is in the CVE database
CVE is the database of known vulnerabilities and exposures. Every entry in that database has a corresponding CVSS score. The CVSS score calculates the severity of the CVE.
Who maintains CVE database
the MITRE corporation
Founded in 1999, the CVE program is maintained by the MITRE corporation and sponsored by the U.S. Department of Homeland Security (DHS) and the Cybersecurity and Infrastructure Security Agency (CISA).
Is CVE a vulnerability database
CVE stands for Common Vulnerabilities and Exposures. CVE is a free service that identifies and catalogs known software or firmware vulnerabilities. CVE is not, in itself, an actionable vulnerability database. It is, in effect, a standardized dictionary of publicly known vulnerabilities and exposures.
What are the CVE and NVD databases
CVE – Common Vulnerabilities and Exposures (CVE) is a list of publicly disclosed vulnerabilities and exposures that is maintained by MITRE. NVD – The National Vulnerability Database (NVD) is a database, maintained by NIST, that is fully synchronized with the MITRE CVE list.
Where are CVE published
the U.S. National Vulnerability Database
A CVE Record can change from the RESERVED state to being published at any time based on a number of factors both internal and external to the CVE List. Once the CVE Record is published with details on the CVE List, it will become available in the U.S. National Vulnerability Database (NVD).
Where can I check my CVE
www.cvedetails.com provides an easy to use web interface to CVE vulnerability data.
Where to find CVE exploits
For a full list of CVE databases, please visit our article Top 4 CVE databases.Exploit DB.Rapid7.CXSecurity.Vulnerability Lab.0day.SecurityFocus.Packet Storm Security.Google Hacking Database.
What is database of vulnerable code
The vulnerable code database (Vulncode-DB) is a database for vulnerabilities and their corresponding source code if available. The database extends the NVD / CVE data sets with user-supplied information regarding patch links, vulnerable code offsets and descriptions.
What is the website for CVE
www.cve.org website
Attention: CVE Records now include product versions & more on the www.cve.org website.
What is CVE check tool
cve-check-tool, as its name suggests, is a tool for checking known (public) CVEs. The tool will identify potentially vunlnerable software packages within Linux distributions through version matching.
What is the exploit database
Exploit Database (ExploitDB) is an archive of exploits for the purpose of public security, and it explains what can be found on the database. The ExploitDB is a very useful resource for identifying possible weaknesses in your network and for staying up to date on current attacks occurring in other networks.
What is a vulnerability database
A vulnerability database (VDB) is a platform aimed at collecting, maintaining, and disseminating information about discovered computer security vulnerabilities.
Where can I download CVE
The most-current download file, which includes all CVE Records and updates, may be downloaded from the table below or directly from the repository on GitHub. Other download capabilities, including daily release versions and hourly updates, are available on GitHub.
Where can I find CVE exploits
www.cvedetails.com provides an easy to use web interface to CVE vulnerability data.
What is the largest exploit database
0day. Also known as Inj3ct0r, 0day. today claims to be the biggest exploit DB in the world, a full-service way to discover, buy and sell exploits anonymously to anyone by using digital currencies such as Bitcoin, Litecoin and Ethereum.
What are the common vulnerability databases
Following are the top sources to trace new vulnerabilities.National Vulnerability Database.Common Vulnerabilities And Exposures.VulnDB – Vulnerability Intelligence.DISA IAVA Database And STIGS.Open Vulnerability And Assessment Language.National Council of ISACs.SecurityTracker.
Where can I check CVE
For detailed information regarding CVE please refer to https://cve.mitre.org/ or the CNA CVE Counting rules at https://cve.mitre.org/cve/cna/CNA_Rules_v1.1.pdf.
Is there more than one vulnerability database
Types of vulnerability databases
Major vulnerability databases such as the ISS X-Force database, Symantec / SecurityFocus BID database, and the Open Source Vulnerability Database (OSVDB) aggregate a broad range of publicly disclosed vulnerabilities, including Common Vulnerabilities and Exposures (CVE).
What is the most common CVE
CVE-2022-22965: The most popular CVE reported in 2022 (also known as Spring4Shell) is an extremely high-impact Injection vulnerability in Spring Framework that allows attackers to make changes remotely to a target system.
What is CVE checker
The Common Vulnerabilities and Exposures (CVE) system identifies all vulnerabilities and threats related to the security of information systems. To do this, a unique identifier is assigned to each vulnerability. Test for free the CVE Scanner Request a demo. 14 days Free trial.
How many CVEs are there
Published CVE Records
| Year | 2023 | 2022 |
|---|---|---|
| Qtr3 | N/A | 6,448 |
| Qtr2 | N/A | 6,365 |
| Qtr1 | 7,015 | 6,015 |
| TOTAL | 7,015 | 25,059 |
What are examples of CVE
Examples of CVEs
A classic example of a CVE is the recent Log4j vulnerability report (CVE-2021-44228). It contains detailed information about a vulnerability of the popular Java logging framework, Apache Log4j. Many service providers, like AWS, Cloudflare and Twitter, were affected by this vulnerability.
How do I know if my CVE is installed
Manual check:
To check whether or not a currently installed package has been patched for a bug or security vulnerabiltiy, zypper can be used to query packages using –bug and –cve flags (this is the preferred method). The "rpm" command with flags "-q –changelog" will also show the patches including security patches.
How are CVEs found
CVE reports can come from anywhere. A vendor, a researcher, or just an astute user can discover a flaw and bring it to someone's attention. Many vendors offer bug bounties to encourage responsible disclosure of security issues. If you find a vulnerability in open source software you should submit it to the community.
What the CVE database is designed to provide to security researchers
One such indispensable tool for cybersecurity professionals is the Common Vulnerabilities and Exposures (CVE) system. As a comprehensive, standardized database of known security threats, CVE empowers organizations to identify, track, and address vulnerabilities effectively.