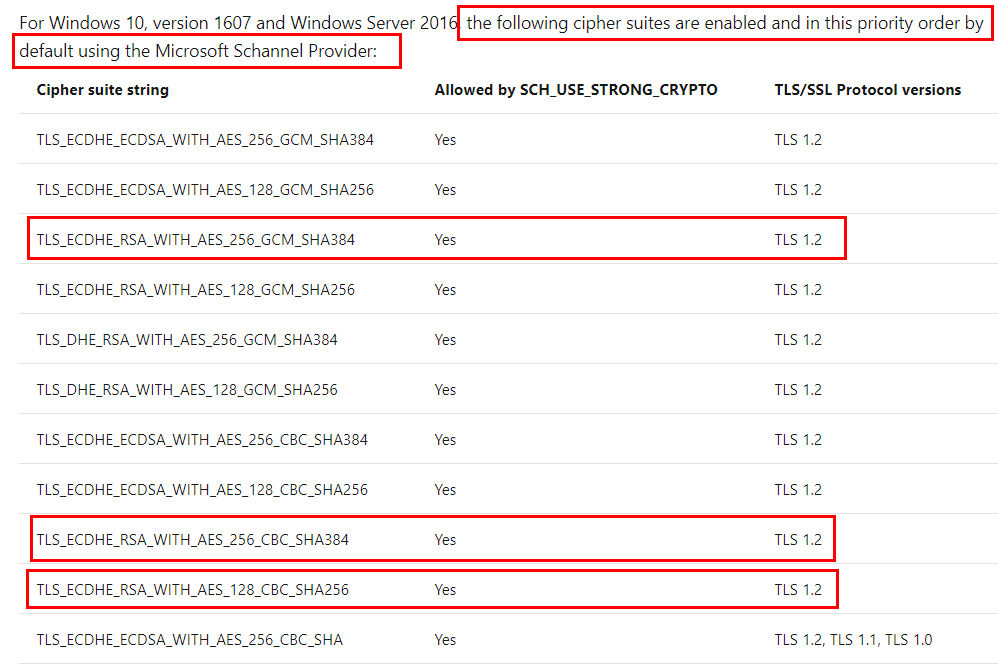
What TLS ciphers are weak
Your organization should avoid TLS versions 1.1 and below and RC4 encryption, as there have been multiple vulnerabilities discovered that render it insecure. The best way to ensure strong transport layer security is to support TLS 1.3, which is the most secure and up-to-date version of TLS.
Does TLS 1.2 have weak ciphers
Especially weak encryption algorithms in TLS 1.2 are designated as NULL, RC2, RC4, DES, IDEA, and TDES/3DES; cipher suites using these algorithms should not be used9. TLS 1.3 removes these cipher suites, but implementations that support both TLS 1.3 and TLS 1.2 should be checked for obsolete cipher suites.
Is TLS 1.2 strong
TLS 1.2 supports Advanced Encryption Standard (AES) cipher suites, which are more secure than the Triple Data Encryption Standard (3DES) cipher suites used in TLS 1.1. AES is a block cipher that uses a 128-bit key, which makes it more secure than 3DES, which uses a 168-bit key.
Which TLS encryption is most secure
One of the key reasons why TLS 1.3 is considered more secure than any of its predecessors is because of how it approaches forward secrecy, an encryption implementation method. Although forward secrecy was possible in older TLS versions, it was only optional. But with TLS 1.3, forward secrecy is mandatory.
Is TLS 1.1 weak
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Which TLS versions are insecure
SSL version 1 and 2, SSLv2 and SSLv3 are now insecure. It is also recommended to phase out TLS 1.0 and TLS 1.1. We recommend that you disable SSLv2, SSLv3, TLS 1.0 and TLS 1.1 in your server configuration so that only the newer TLS protocols can be used. It is recommended to only enable TLS 1.3 for maximum security.
Why is TLS 1.0 and 1.1 bad
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Is TLS 1.2 vulnerable to SWEET32
The SWEET32 (Birthday Attack) is a Medium level vulnerability which is prevalent in TLS 1.0 and TLS 1.1 which support 3DES Encryption. To resolve this issue you should deploy TLS 1.2 as a minimum (the 3DES cypher is dropped by default) and disable vulnerable ciphers.
Does TLS 1.2 have vulnerabilities
Any software is going to have vulnerabilities – flaws that an attacker can exploit. In the case of TLS, parts of the protocol carried over from its early days in the 1990s resulted in several high-profile vulnerabilities persisting in TLS 1.2.
Is TLS 1.2 the most secure
The most widely used versions of TLS nowadays are TLS 1.0, TLS 1.1, and TLS 1.2. While TLS 1.0 & TLS 1.1 are known to be very vulnerable, the TLS 1.2 protocol is considered to be much more secure and is thus recommended for use.
Which TLS is vulnerable
While TLS 1.0 & TLS 1.1 are known to be very vulnerable, the TLS 1.2 protocol is considered to be much more secure and is thus recommended for use.
Why is TLS 1.0 weak
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Is TLS 1.1 still in use
We have already disabled TLS 1.0 and 1.1 for most Microsoft 365 services in the world wide environment. For Microsoft 365 operated by 21 Vianet, TLS 1.0/1.1 will be disabled on June 30, 2023. As of October 31, 2018, the Transport Layer Security (TLS) 1.0 and 1.1 protocols are deprecated for the Microsoft 365 service.
Is TLS 1.3 vulnerable
Many of the major vulnerabilities in TLS 1.2 had to do with older cryptographic algorithms that were still supported. TLS 1.3 drops support for these vulnerable cryptographic algorithms, and as a result it is less vulnerable to cyber attacks.
Why is TLS 1.2 not secure
In TLS 1.2 and earlier versions, the use of ciphers with cryptographic weaknesses had posed potential security vulnerabilities. TLS 1.3 includes support only for algorithms that currently have no known vulnerabilities, including any that do not support Perfect Forward Secrecy (PFS).
Is TLS 1.0 outdated
As of October 31, 2018, the Transport Layer Security (TLS) 1.0 and 1.1 protocols are deprecated for the Microsoft 365 service. The effect for end-users is minimal. This change has been publicized for over two years, with the first public announcement made in December 2017.
Is TLS 1.2 vulnerable to LUCKY13
LUCKY13 is a timing attack that can be used against implementations of the TLS protocol. Timming attack can be used by the cipher block chaining mode of operation. Because the vulnerability affects the TLS 1.1 and 1.2 specification as well as certain forms of earlier versions.
Which version of TLS is unsafe
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Is TLS 1.2 not secure
TLS 1.2 is more secure than the previous cryptographic protocols such as SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1. Essentially, TLS 1.2 keeps data being transferred across the network more secure.
Why is TLS 1.1 bad
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Why TLS 1.3 is not used
TLS 1.3 mandates the use of specific ciphers, which can take a toll on the server side. SSL offload on application delivery controllers (ADCs) and decryption on servers would require costly hardware upgrades and administrative overhead. TLS 1.2 is still relevant and has not yet been compromised.
Is TLS 1.1 a security risk
Risk of outdated TLS protocols
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Why is TLS 1.1 insecure
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Is TLS 1.2 end of life
It appears the maximum number of years is 22years and the average is approximately 15 years. TLS 1.2 being published in 2008 would then have an expected life of 22years to 2023 however we expect it to be longer than this. One reason to change version is vulnerabilities and TLS1.
Is TLS 1.1 vulnerable
TLS 1.1 is the forgotten “middle child.” It doesn't have any known protocol vulnerabilities, though does share support for bad cryptography like its younger sibling. In most software it was leapfrogged by TLS 1.2 and it's rare to see TLS 1.1 used.