Where to find cve exploits
For a full list of CVE databases, please visit our article Top 4 CVE databases.Exploit DB.Rapid7.CXSecurity.Vulnerability Lab.0day.SecurityFocus.Packet Storm Security.Google Hacking Database.
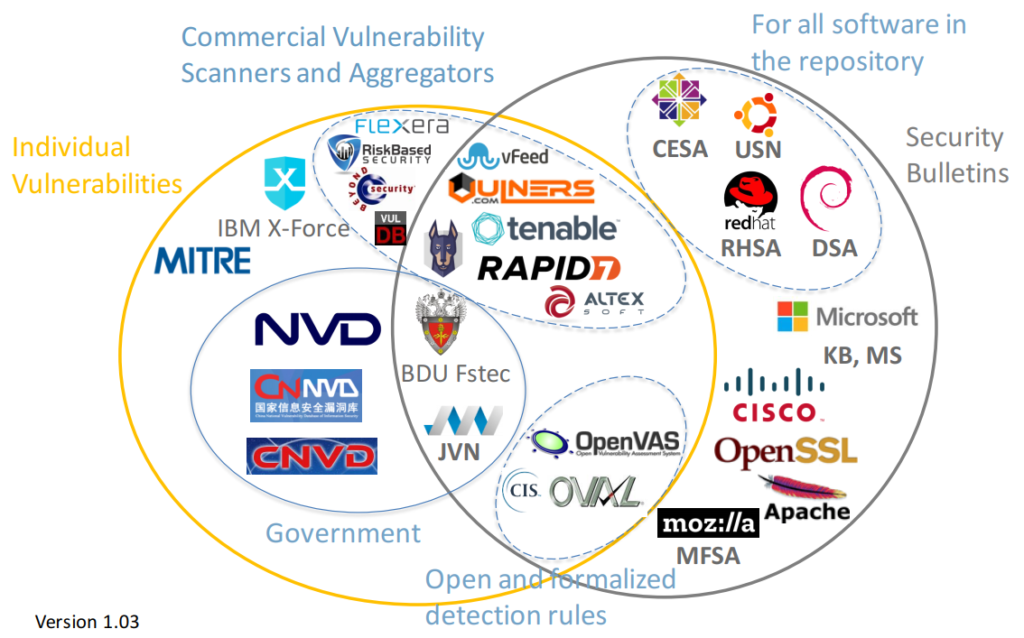
Who controls CVE
The Mitre Corporation
The Mitre Corporation functions as Editor and Primary CNA. Various CNAs assign CVE numbers for their own products (e.g. Microsoft, Oracle, HP, Red Hat, etc.) A third-party coordinator such as CERT Coordination Center may assign CVE numbers for products not covered by other CNAs.
Who created exploit DB
str0ke, one of the leaders of the ex-hacking group milw0rm, that split up in 1998, started a public exploit archive in early 2004. He chose to do so when 'FrSIRT' (another exploit source) changed into a private, paid source (which in 2008 became VUPEN).
Who can publish a CVE
The publication can be done by the vendor if the response is present within a timeframe you have chosen and if not, you can do a publication on your own.
Is CVE a vulnerability database
CVE stands for Common Vulnerabilities and Exposures. CVE is a free service that identifies and catalogs known software or firmware vulnerabilities. CVE is not, in itself, an actionable vulnerability database. It is, in effect, a standardized dictionary of publicly known vulnerabilities and exposures.
Who owns exploit db
The Exploit Database is maintained by OffSec, an information security training company that provides various Information Security Certifications as well as high end penetration testing services. The Exploit Database is a non-profit project that is provided as a public service by OffSec.
How does exploit DB work
Exploit Database (ExploitDB) is an archive of exploits for the purpose of public security, and it explains what can be found on the database. The ExploitDB is a very useful resource for identifying possible weaknesses in your network and for staying up to date on current attacks occurring in other networks.
Who is CVE managed by
the MITRE Corporation
First launched in 1999, CVE is managed and maintained by the National Cybersecurity FFRDC (Federally Funded Research and Development Center), operated by the MITRE Corporation.
What is the process of CVE publishing
The reporter requests a CVE ID, which is then reserved for the reported vulnerability. Once the reported vulnerability is confirmed by the identification of the minimum required data elements for a CVE Record, the record is published to the CVE List.
Who creates a CVE for vulnerability
The Mitre Corporation
CVEs are assigned by a CVE Numbering Authority (CNA). While some vendors acted as a CNA before, the name and designation was not created until February 1, 2005. there are three primary types of CVE number assignments: The Mitre Corporation functions as Editor and Primary CNA.
What does a CVE database do
CVE stands for Common Vulnerabilities and Exposures. CVE is a free service that identifies and catalogs known software or firmware vulnerabilities. CVE is not, in itself, an actionable vulnerability database. It is, in effect, a standardized dictionary of publicly known vulnerabilities and exposures.
Who manages Metasploit
The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development. It is owned by Boston, Massachusetts-based security company Rapid7.
Who owns exploit-db
The Exploit Database is maintained by OffSec, an information security training company that provides various Information Security Certifications as well as high end penetration testing services. The Exploit Database is a non-profit project that is provided as a public service by OffSec.
How do hackers get access to databases
This can be done through a variety of means, but the most common is by guessing or brute forcing passwords. Once in, the hacker can then do anything they want with the data, including deleting it, modifying it, or using it to their own ends. The most common way that databases are hacked is by guessing passwords.
Where are CVE published
the U.S. National Vulnerability Database
A CVE Record can change from the RESERVED state to being published at any time based on a number of factors both internal and external to the CVE List. Once the CVE Record is published with details on the CVE List, it will become available in the U.S. National Vulnerability Database (NVD).
What are the CVE and CWE databases
In other words, CVE is a list of known instances of vulnerability for specific products or systems, while CWE acts as a dictionary (so to speak) of software vulnerability types. The National Vulnerability Database (NVD) actually uses CWEs to score CVEs.
What database does Metasploit use
PostgreSQL database system
Databases in Metasploit
Metasploit has built-in support for the PostgreSQL database system. The system allows quick and easy access to scan information and gives us the ability to import and export scan results from various third party tools. We can also use this information to configure module options rather quickly.
Which database service is required for Metasploit
PostgreSQL
The Metasploit Framework provides back end database support for PostgreSQL. The database stores information, such as host data, loot, and exploit results.
How do hackers most commonly gain access to firm networks and databases
Emails. Emails are a common source of entry, from phishing to malware. Email phishing is one of the oldest and most successful hacking techniques. Attackers send out mass emails disguised as an authentic communication from a bank, subscription service or online payment site.
How do hackers gain data
One of the most common and well known ways is through a data breach. A data breach occurs when an individual or organization accesses your data without your permission. Hackers will breach the databases of corporations in order to obtain your personal info.
What organization maintains the national vulnerability database
The National Vulnerability Database (NVD) is the most comprehensive publicly accessible repository of vulnerability intelligence. It is maintained by the National Institute of Standards and Technology (NIST) and draws on the work of MITRE and others.
What is in the CVE database
CVE is the database of known vulnerabilities and exposures. Every entry in that database has a corresponding CVSS score. The CVSS score calculates the severity of the CVE.
Do real hackers use Metasploit
Information gathering is one of the main use cases of Metasploit. Both actual and ethical hackers can use this tool to obtain access and information about their targets by using a variety of IT recon techniques, such as service identification, SNMP sweeping, port scanning, or Microsoft SQL hunting.
Which type of database does Metasploit 5 use
The Metasploit Framework provides back end database support for PostgreSQL. The database stores information, such as host data, loot, and exploit results.
How do hackers get databases
Attackers are capable of exploiting buffer overflows, SQL Injection, etc. in order to own the database server. The attack could be via a web application by exploiting SQL injection, so no authentication is needed. In this way, databases can be hacked from the Internet and firewalls are completely bypassed.