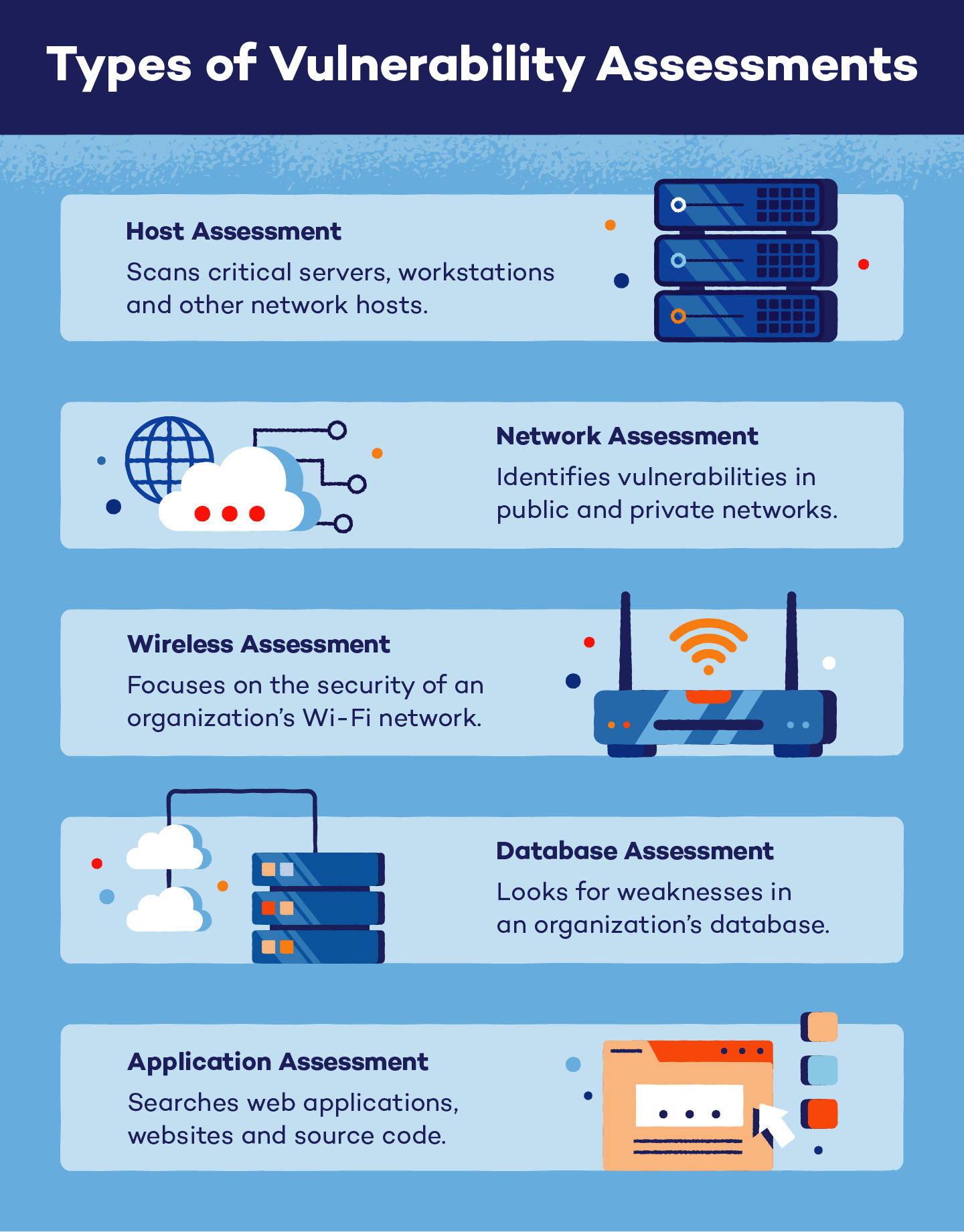
Who is generally involved in a vulnerability assessment
Vulnerability remediation involves fixing any security issues that were deemed unacceptable in the risk assessment process. This is typically a joint effort between development,operations, compliance, risk management, and security teams, who decide on a cost-effective path to remediate each vulnerability.
Who is accountable for vulnerability management
the security officer
The owner of the whole vulnerability management process is the security officer. The security officer is responsible for designing the whole process and making sure that it's getting implemented correctly.
What is the role of vulnerability assessment
A vulnerability assessment is the testing process used to identify and assign severity levels to as many security defects as possible in a given timeframe. This process may involve automated and manual techniques with varying degrees of rigor and an emphasis on comprehensive coverage.
Is vulnerability assessment part of vulnerability management
Vulnerability assessments are an important part of the vulnerability management cycle, and the VM cycle should be a key component of your NetOps team's security strategy. Organizations today simply can't afford to ignore the risks in their network infrastructure.
Who is responsible for cybersecurity risk management
Chief Information Officer (CIO)
A CIO must be aware of the cybersecurity regulations that govern their industry and communicate the risks throughout the organization. The CIO should also ensure controls are in place to mitigate cybersecurity risks.
Who is responsible for assessing managing and implementing security
Chief Information Security Officer (CISO). This person reports directly to the CIO (large enterprises may have more layers of management between this person and the CIO). This person is responsible for assessing, managing, and implementing security.
Who is responsible for cyber risk management
Chief Information Officer (CIO)
The CIO should also ensure controls are in place to mitigate cybersecurity risks. Additionally, this C-level executive must enforce and manage cybersecurity roles for third-party vendors, including thorough vetting of each outside entity.
Who is ultimately accountable for risks threats and vulnerabilities
Executive management is ultimately accountable for controlling risks. Executives must explain why major security breaches occurred. They must rebuild trust with the public.
What are the roles and responsibilities of vulnerability management analyst
Vulnerability Management/ Security AnalystVulnerability Management.Responsibilities: Daily assessment of vulnerabilities identified by infrastructure scan.Evaluate, rate and perform risk assessments on assets.Prioritizing vulnerabilities discovered along with remediation timeline(s)
What is needed for vulnerability assessment
Modern vulnerability assessments rely on automated scanning tools. Here are the main categories of tools used to scan an environment for vulnerabilities: Network-based scanning—used to identify potential network security attacks. This type of scan can also detect vulnerable systems on wired or wireless networks.
What are the 3 components of vulnerability assessment
There are three dimensions of vulnerability: exposure, sensitivity, and adaptive capacity.
Is vulnerability assessment an audit
A vulnerability assessment makes up one aspect of a security audit. While audits are comprehensive and cover all elements of a security system, assessments are often completed individually or only for one specific area. Audits also run tests and compare security measures to other federal compliance standards.
Who is most responsible for risk management
Senior Managers are essentially the 'risk owners' and are required to manage risks on a day-to-day basis. Senior managers are the first line defence in combating risk and are responsible for implementing effective internal controls.
Which department is responsible for cyber security
Ministry of Electronics and Information Technology
National Cyber Coordination Centre
| Emblem of India | |
| Agency overview | |
|---|---|
| Jurisdiction | Government of India |
| Agency executive | Lt. Gen. Rajesh Pant (Retd.), National Cyber Security Coordinator |
| Parent department | Ministry of Electronics and Information Technology (India) |
Who is responsible for security at the company
CISO: Security is the primary concern of the chief information security officer, the CISO. It is their responsibility to set the organization's security strategy, establish the policies that will uphold the strategy, and ensure that response plans are in place and tested.
Who prepares the security assessment report
At the completion of the assessment testing, the Independent Assessors or 3PAO produces the Security Assessment Report (SAR) that documents the verification of the CSPs implementation of security and provides the overall risk posture of a CSP in support of security authorization decision.
Which department is responsible for risk management
Typically, the risk manager is lodged in the finance department. In a few organizations, the risk manager is part of the legal or safety departments.
Which team is responsible for risk management
Risk management is the responsibility of the project team.
Who is responsible for security and compliance
A company's CISO is the leader and face of data security in an organization. The person in this role is responsible for creating the policies and strategies to secure data from threats and vulnerabilities, as well as devising the response plan if the worst happens.
Who owns vulnerability management
What is IT vulnerability ownership SANS states that a security officer is the ultimate vulnerability owner.
What are the responsibilities of data management analyst
A data management analyst is responsible for maintaining databases. In this position, your responsibilities are to keep an eye on how secure the data is and look for ways to increase user efficiency when accessing it. For example, you might move the database to an online cloud-based server to free up system resources.
What are the 4 steps in vulnerability assessment
With the right tools in hand, you can perform a vulnerability assessment by working through the following steps:Asset discovery. First, you need to decide what you want to scan, which isn't always as simple as it sounds.Prioritization.Vulnerability scanning.Result analysis & remediation.Continuous cyber security.
Which are the 4 key drivers of vulnerability
4 key drivers of customer vulnerabilityHealth. Conditions or illnesses that affect one's ability to complete day-to-day tasks, both mentally and physically.Life Events. Such as bereavement, job loss or relationship breakdown.Resilience. Low ability to withstand and manage financial or emotional shocks.Capability.
What are the 4 pillars of vulnerability
In there, we argue that there is a connection between vulnerability, empathy, integrity and adaptability (the 4 Pillars) and authentic leadership for trustful working environments.
Do auditors do risk assessments
Risk assessment is a key requirement of the planning phase of an audit. and assess the risks of material misstatement, whether due to error or fraud, at the financial statement and relevant assertion levels, which aids us in designing further audit procedures.