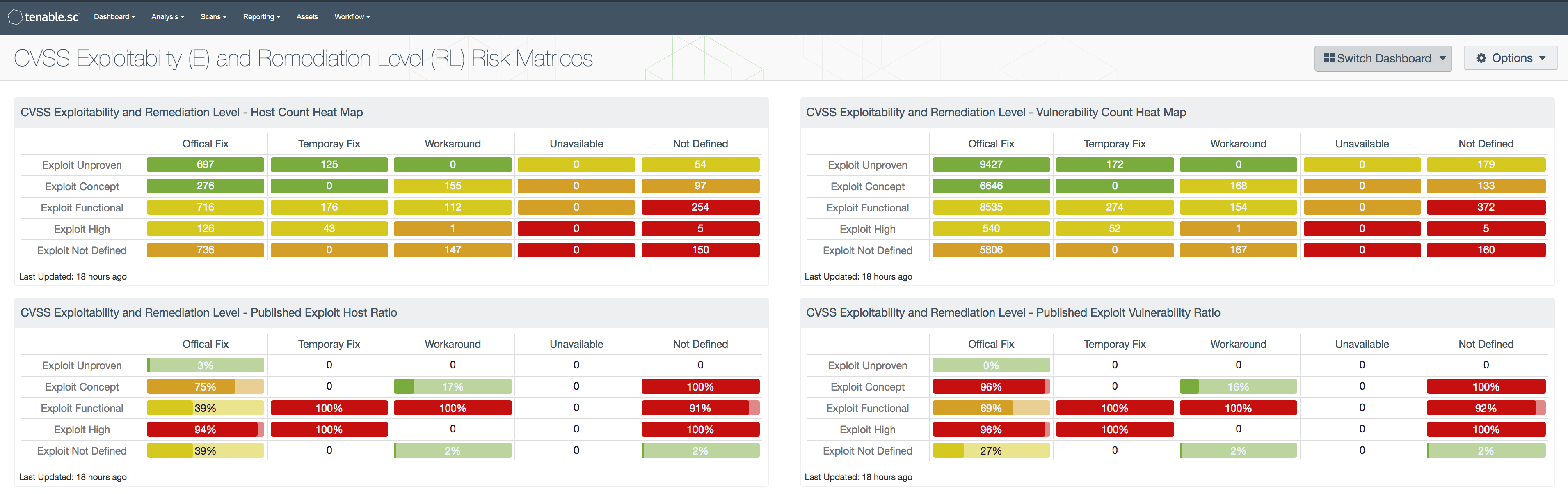
What is a vulnerability management process
Vulnerability management is the ongoing, regular process of identifying, assessing, reporting on, managing and remediating cyber vulnerabilities across endpoints, workloads, and systems.
In what order are the steps in the vulnerability management life cycle
The 7 stages of the vulnerability management lifecycleDiscover enterprise assets.Prioritize enterprise assets.Find and assess vulnerabilities.Prioritize and report vulnerabilities.Remediate.Verify remediation.Continuous improvement.
What is the first phase of the vulnerability assessment
Step 1: Define Parameters and Plan Assessment
An important part of the planning process will be an initial discovery phase, where you identify assets and determine baselines for their individual security capabilities, risk tolerance, user permissions, configuration, and other factors.
How do you manage a vulnerability management program
To start building an effective program, there are seven key steps to consider when implementing a Vulnerability Management framework:Make An Inventory.Categorize Vulnerabilities.Create The Package.Test The Package.Establish Change Management.Patch Vulnerabilities.Report On Results.
What is CVE in vulnerability management
CVE stands for Common Vulnerabilities and Exposures. The system provides a method for publicly sharing information on cybersecurity vulnerabilities and exposures. What is the Difference Between CVE and CVSS CVE is the database of known vulnerabilities and exposures.
What is a vulnerability management framework
A vulnerability management framework provides a set of guidelines and best practices to help you quickly identify and patch security flaws and improve your cybersecurity posture.
What is order lifecycle management
Order Lifecycle Management Definition
Order lifecycle management (OLM) plays a key role in helping companies streamline their order process flow from order placement to post-delivery services. It ends when the order touches a customer and is designed to provide a seamless experience for both consumers and businesses.
Who is generally involved in a vulnerability assessment
Vulnerability remediation involves fixing any security issues that were deemed unacceptable in the risk assessment process. This is typically a joint effort between development,operations, compliance, risk management, and security teams, who decide on a cost-effective path to remediate each vulnerability.
What are the 4 stages of vulnerability management
The four continuous stages of identification, prioritization, remediation, and reporting are essential for an effective vulnerability management process. A vulnerability is a flaw or weakness in a system that, if exploited, would allow a user to gain unauthorized access to conduct an attack.
What are the roles of a vulnerability management
Job DescriptionVulnerability Management.Responsibilities: Daily assessment of vulnerabilities identified by infrastructure scan.Evaluate, rate and perform risk assessments on assets.Prioritizing vulnerabilities discovered along with remediation timeline(s)
Who manages CVE
the MITRE corporation
Founded in 1999, the CVE program is maintained by the MITRE corporation and sponsored by the U.S. Department of Homeland Security (DHS) and the Cybersecurity and Infrastructure Security Agency (CISA).
Who assigns CVSS scores
The National Vulnerability Database (NVD)
The National Vulnerability Database (NVD) provides CVSS scores for almost all known vulnerabilities. The NVD supports both Common Vulnerability Scoring System (CVSS) v2. 0 and v3. X standards.
Is vulnerability management part of GRC
We've covered why vulnerability management is critical to your cybersecurity program and how it should be part of your overall GRC program.
What is lifecycle management role
The primary responsibility of a project lifecycle manager is overseeing the work of the project team and making sure they complete each phase of a project's lifecycle on time. Common responsibilities of a product lifecycle manager include: conducting feasibility research and gathering resources.
Is order management part of CRM
While a CRM is used to manage customer-facing duties, order management requires its own set of tools. Once a consumer places an order in the CRM, the information from that order must be shared with other departments such as inventory management and fulfilment centres.
Who is accountable for vulnerability management
the security officer
The owner of the whole vulnerability management process is the security officer. The security officer is responsible for designing the whole process and making sure that it's getting implemented correctly.
Who maintains the common vulnerabilities and exposures CVE list
The MITRE corporation
The MITRE corporation maintains the CVE List, but a security flaw that becomes a CVE entry is often submitted by organizations and members of the open source community.
What are the 4 vulnerability key drivers
4 key drivers of customer vulnerabilityHealth. Conditions or illnesses that affect one's ability to complete day-to-day tasks, both mentally and physically.Life Events. Such as bereavement, job loss or relationship breakdown.Resilience. Low ability to withstand and manage financial or emotional shocks.Capability.
What are the 5 steps of vulnerability management
There are five main stages in the vulnerability management cycle include:Assess.Prioritize.Act.Reassess.Improve.
What is the role of vulnerability management analyst
Job DescriptionVulnerability Management.Responsibilities: Daily assessment of vulnerabilities identified by infrastructure scan.Evaluate, rate and perform risk assessments on assets.Prioritizing vulnerabilities discovered along with remediation timeline(s)
What is the difference between CVSS and CVE
The CVE represents a summarized vulnerability, while the Common Vulnerability Scoring System (CVSS) assesses the vulnerability in detail and scores it, based on several factors.
Who assigns CVE scores
CVE Numbering Authority (CNA)
CVEs are assigned by a CVE Numbering Authority (CNA). While some vendors acted as a CNA before, the name and designation was not created until February 1, 2005. there are three primary types of CVE number assignments: The Mitre Corporation functions as Editor and Primary CNA.
Who assigns the CVE number for an vulnerability
CVE identifiers are assigned by a CVE Numbering Authority (CNA). There are about 100 CNAs, representing major IT vendors—such as Red Hat, IBM, Cisco, Oracle, and Microsoft—as well as security companies and research organizations. MITRE can also issue CVEs directly.
Who maintains CVE
the MITRE corporation
Founded in 1999, the CVE program is maintained by the MITRE corporation and sponsored by the U.S. Department of Homeland Security (DHS) and the Cybersecurity and Infrastructure Security Agency (CISA).
Who is responsible for life-cycle management
the PM
Consequently, the PM is responsible for the implementation, management, and/or oversight of activities associated with the system's development, production, fielding, sustainment, and disposal. Performance-Based Life-Cycle Product Support is the strategy PM will use in implementing life-cycle management.