What benefit would a CVE CVSS provide to a defensive cybersecurity team
Common Vulnerabilities and Exposures (CVE) is a list or glossary of publicly known security flaws. It assesses vulnerabilities and scores them using the Common Vulnerability Scoring System (CVSS). Cybersecurity professionals use this information to determine how dangerous vulnerabilities are.
What is the CVSS score in CVE
CVSS is the overall score assigned to a vulnerability. CVE is simply a list of all publicly disclosed vulnerabilities that includes the CVE ID, a description, dates, and comments. The CVSS score is not reported in the CVE listing – you must use the NVD to find assigned CVSS scores.
What is CVE in vulnerability management
CVE stands for Common Vulnerabilities and Exposures. The system provides a method for publicly sharing information on cybersecurity vulnerabilities and exposures. What is the Difference Between CVE and CVSS CVE is the database of known vulnerabilities and exposures.
What is the difference between critical and high vulnerability
Critical: These vulnerabilities should be prioritized for immediate remediation. High: These vulnerabilities should be reviewed and remedied wherever possible. Medium: These vulnerabilities pose minimal risk to data security. Low: This category represents vulnerabilities that are cautionary or informational in nature.
Who uses CVE
Information technology and cybersecurity professionals use CVE Records to ensure they are discussing the same issue, and to coordinate their efforts to prioritize and address the vulnerabilities.
Why would we use CVSS
CVSS enables the organization to use the same scoring framework to rate the severity of IT vulnerabilities across a range of software products. CVSS scores help security teams to prioritize the vulnerabilities that need immediate attention.
Does CVE use CVSS
CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
What is CVSS used for
The Common Vulnerability Scoring System (CVSS) is a public framework for rating the severity of security vulnerabilities in software.
What are the two most common types of vulnerability scans
Credentialed and non-Credentialed scans (also respectively referred to as authenticated and non-authenticated scans) are the two main categories of vulnerability scanning. Non-credentialed scans, as the name suggests, do not require credentials and do not get trusted access to the systems they are scanning.
What are the 4 main types of vulnerability
Types of vulnerability include social, cognitive, environmental, emotional or military. In relation to hazards and disasters, vulnerability is a concept that links the relationship that people have with their environment to social forces and institutions and the cultural values that sustain and contest them.
Do hackers use CVE
Can Hackers Use CVE to Attack My Organization The short answer is yes but many cybersecurity professionals believe the benefits of CVE outweigh the risks: CVE is restricted to publicly known vulnerabilities and exposures.
Does every vulnerability have a CVSS score
The National Vulnerability Database (NVD) provides CVSS scores for almost all known vulnerabilities. The NVD supports both Common Vulnerability Scoring System (CVSS) v2.0 and v3.X standards. The NVD provides CVSS 'base scores' which represent the innate characteristics of each vulnerability.
Does Nessus use CVSS
Tenable Nessus analysis pages provide summary information about vulnerabilities using the following CVSS categories. The plugin's highest vulnerability CVSSv2 score is 10.0. The plugin's highest vulnerability CVSSv3 score is between 9.0 and 10.0.
Who uses vulnerability scanners
security teams
A vulnerability scanner enables organizations to monitor their networks, systems, and applications for security vulnerabilities. Most security teams utilize vulnerability scanners to bring to light security vulnerabilities in their computer systems, networks, applications and procedures.
Which scan is most commonly used by attacker
Port scanning
Port scanning is one of the most popular techniques attackers use to discover services they can exploit to break into your computer system, according to the SANS Institute. It's important to note that port scanning is not solely used for nefarious purposes. It also has legitimate uses in managing networks.
What are the 5 categories of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
What are 5 example of vulnerability
To illustrate the principles above, here are 11 specific examples of vulnerability: Telling someone when they've upset you, respectfully but honestly. Sharing something personal about yourself that you normally wouldn't. Admitting to mistakes you have made in the past.
Does Qualys use CVSS
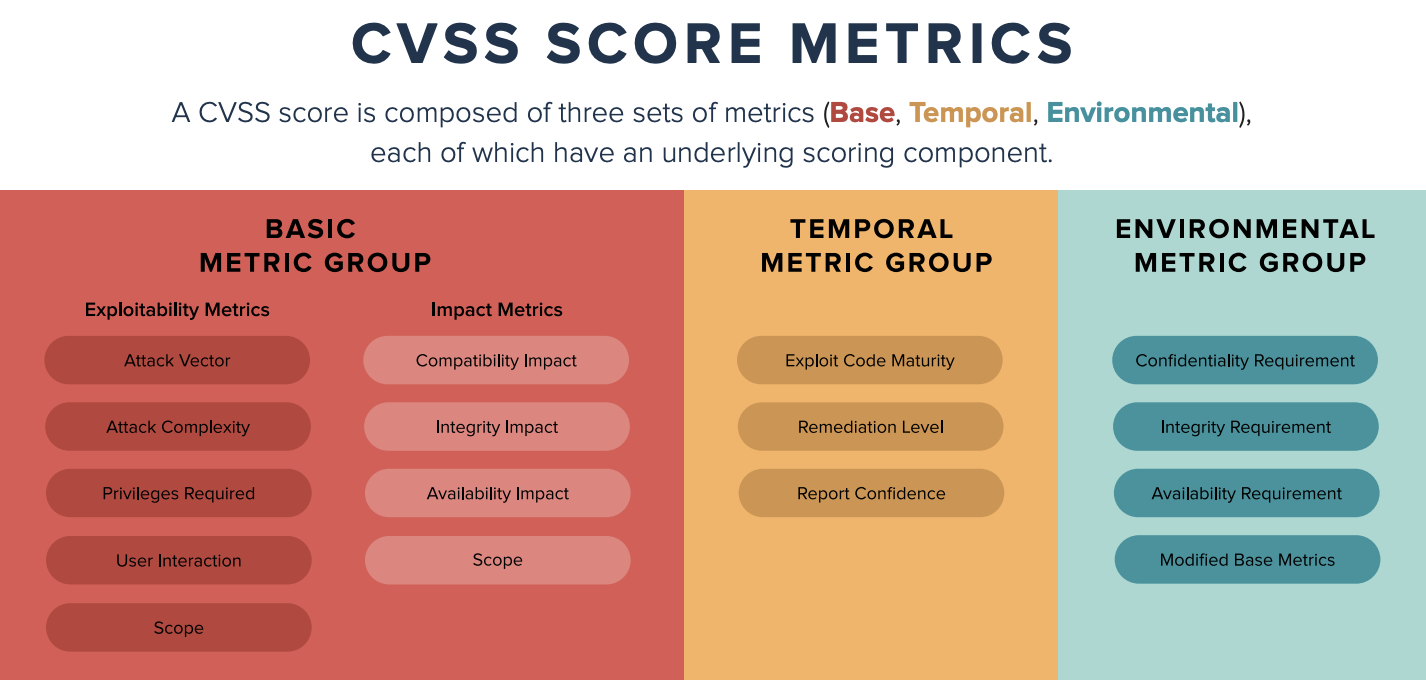
Qualys exposes CVSS Base and Temporal Scores for each vulnerability. The Common Vulnerability Scoring System (CVSS) provides an open framework for communicating the characteristics and impacts of vulnerabilities. CVSS consists of 3 groups: Base.
Do hackers use vulnerability scanners
How Scanning Tools Help Hackers. The most commonly used tools are vulnerability scanners that can search for several known vulnerabilities on a target network and potentially detect thousands of vulnerabilities.
Is the world’s most popular vulnerability scanner used in companies for checking
Explanation: Nessus is a popular and proprietary network vulnerability scanning tool developed by Tenable Network Security. It helps in easily identifying vulnerabilities and fix them, which includes missing patches and software flaws.
What are the 4 main types of vulnerability in cyber security
The four main types of vulnerabilities in information security are network vulnerabilities, operating system vulnerabilities, process (or procedural) vulnerabilities, and human vulnerabilities.
What are 3 types of common cybersecurity attacks
What are the 10 Most Common Types of Cyber AttacksMalware.Denial-of-Service (DoS) Attacks.Phishing.Spoofing.Identity-Based Attacks.Code Injection Attacks.Supply Chain Attacks.Insider Threats.
What are the three 3 types of network service vulnerabilities
At the broadest level, network vulnerabilities fall into three categories: hardware-based, software-based, and human-based.
What are the 5 types of cyber-attacks
What are the 10 Most Common Types of Cyber AttacksMalware.Denial-of-Service (DoS) Attacks.Phishing.Spoofing.Identity-Based Attacks.Code Injection Attacks.Supply Chain Attacks.Insider Threats.
What are the 4 types of attacks in network security
Types of Cyber AttacksMalware Attack. This is one of the most common types of cyberattacks.Phishing Attack. Phishing attacks are one of the most prominent widespread types of cyberattacks.Password Attack.Man-in-the-Middle Attack.SQL Injection Attack.Denial-of-Service Attack.Insider Threat.Cryptojacking.