What is the purpose of the CVE
CVE stands for Common Vulnerabilities and Exposures. The system provides a method for publicly sharing information on cybersecurity vulnerabilities and exposures.
What is CVE and CVSS
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
What is the relationship between NVD and CVE
CVE – Common Vulnerabilities and Exposures (CVE) is a list of publicly disclosed vulnerabilities and exposures that is maintained by MITRE. NVD – The National Vulnerability Database (NVD) is a database, maintained by NIST, that is fully synchronized with the MITRE CVE list.
What is the difference between CWE and CVSS
Common Weakness Scoring System (CWSS) is a framework that documents software weaknesses so developers can minimize the number of bugs and vulnerabilities they introduce in a live system. The biggest difference between scoring systems is that the CWSS is proactive, whereas the CVSS is reactive.
What is the importance of vulnerability index
Conducting a vulnerability assessment has numerous benefits, including: Identifying vulnerabilities before hackers find them. VA scans all the network components, verifying whether they have weaknesses that cybercriminals can use to attack the organization.
Why are CWE and CVE important
Whereas the CVE logs real-world instances of vulnerabilities and exposures in specific products, the CWE lists and defines weaknesses commonly seen in digital products. The CWE does not refer to one particular example but provides definitions for widely seen defects.
Why is the CVSS important
CVSS scores quantify the severity of vulnerabilities. An IT team can use this information to determine which vulnerabilities pose the most serious threats and resolve them first before moving on to more minor weaknesses.
What benefit would a CVE CVSS provide to a defensive cybersecurity team
Common Vulnerabilities and Exposures (CVE) is a list or glossary of publicly known security flaws. It assesses vulnerabilities and scores them using the Common Vulnerability Scoring System (CVSS). Cybersecurity professionals use this information to determine how dangerous vulnerabilities are.
What is the purpose of Common Vulnerabilities and Exposures CVE standard in a network
CVE is designed to allow vulnerability databases and other tools to be linked together. It also facilitates comparisons between security tools and services. Check out the US National Vulnerability Database (NVD) that uses the CVE list identifiers and includes fix information, scoring and other information.
Do all vulnerabilities have a CVE
CVE stands for Common Vulnerabilities and Exposures. It is the database of publicly disclosed information on security issues. All organizations use CVEs to identify and track the number of vulnerabilities. But not all the vulnerabilities discovered have a CVE number.
What are the advantages of CVSS
Benefits of CVSS scoresDefines vulnerability vocabulary, nomenclature, and scoring.Dictates a standardized practice and base metric across communities.Provides indicators of existing risks that need mitigation.Allows a glimpse into the world of software and systems development.
Why is CVSS important
CVSS enables the organization to use the same scoring framework to rate the severity of IT vulnerabilities across a range of software products. CVSS scores help security teams to prioritize the vulnerabilities that need immediate attention.
What is the importance of vulnerability in cyber security
A vulnerability in security refers to a weakness or opportunity in an information system that cybercriminals can exploit and gain unauthorized access to a computer system. Vulnerabilities weaken systems and open the door to malicious attacks.
What is the importance of vulnerability identification
Vulnerability assessments can identify vulnerabilities in applications, systems, and network devices that attackers could exploit to gain unauthorized access to sensitive data. Organizations can reduce the risk of data breaches by identifying these vulnerabilities and protecting sensitive information.
What is the importance of vulnerability scanning tools
A vulnerability scanner enables organizations to monitor their networks, systems, and applications for security vulnerabilities. Most security teams utilize vulnerability scanners to bring to light security vulnerabilities in their computer systems, networks, applications and procedures.
What is the difference between CVE score and CVSS score
The CVE represents a summarized vulnerability, while the Common Vulnerability Scoring System (CVSS) assesses the vulnerability in detail and scores it, based on several factors.
What are the benefits of CVSS
Benefits of using CVSS: Standardization: CVSS provides a standardized and consistent way of measuring the severity of vulnerabilities across different systems, making it easier for organizations to compare and prioritize vulnerabilities.
Is CVE good or bad
CVE entries are not a good source to rank products by their "overall security". The main idea behind the CVE system is to create unique identifiers for software vulnerabilities. It's not designed to be a complete and verified database of all known vulnerabilities in any product.
What are the limitations of CVE
Limitations of CVE
The CVE is not intended to be used as a vulnerability database, so it does not initially contain sufficient information to run a comprehensive vulnerability management program.
Does CVSS measure risk or severity
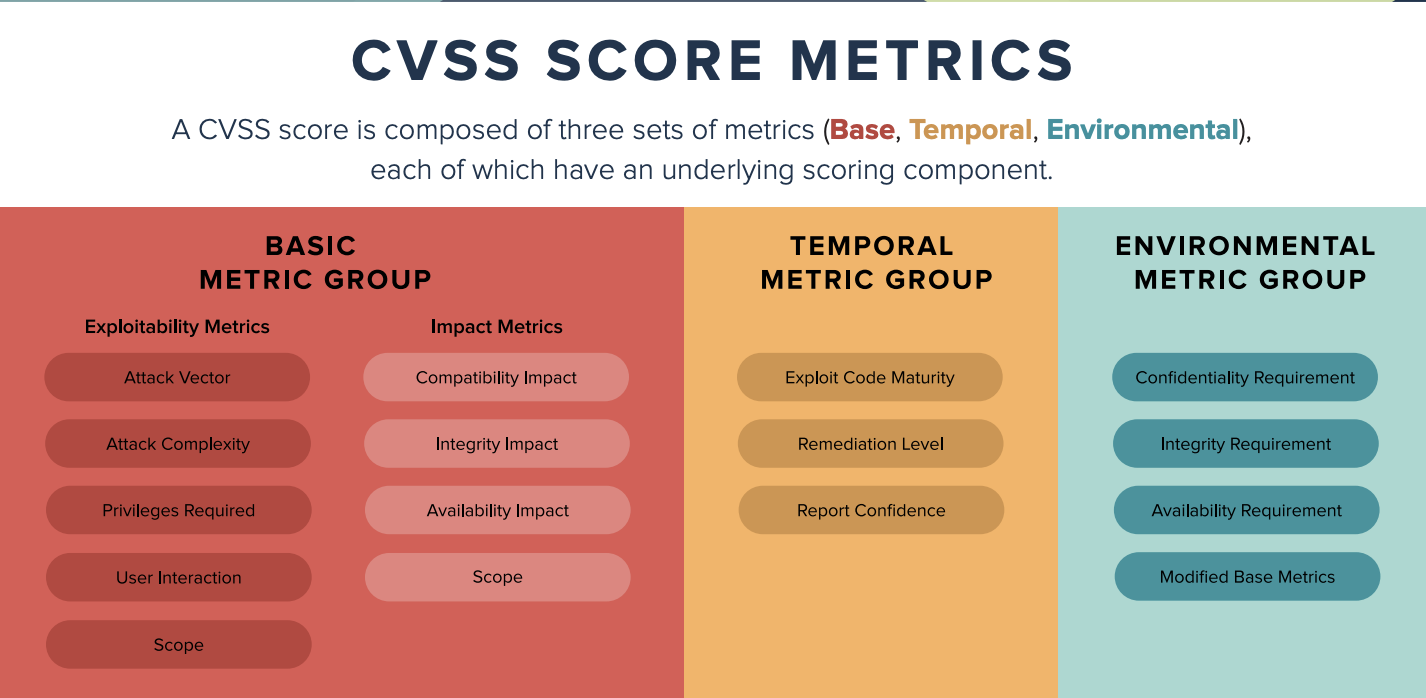
The Common Vulnerability Scoring System (CVSS) is a method used to supply a qualitative measure of severity. CVSS is not a measure of risk. CVSS consists of three metric groups: Base, Temporal, and Environmental.
Is CVSS a scoring system for security vulnerability scoring
What is CVSS The Common Vulnerability Scoring System (aka CVSS Scores) provides a numerical (0-10) representation of the severity of an information security vulnerability.
Why is network vulnerability scanning important
Vulnerability scans can be used to find vulnerable software and infrastructure that has been incorrectly configured. For instance, the scan could reveal that the version of Apache Web Server running requires updating or that communication ports have been left exposed that don't need to be.
Why is the concept of vulnerability important
“Vulnerability allows up to open up about how we feel and in turn helps us feel less alone or isolated. Sometimes we just need to be heard and other times we need advice or support/accountability.”
What is vulnerability and why is IT important
Vulnerability is an opportunity to grow as a person and a way to find deep satisfaction in your relationships. Opening up and relinquishing your fears of rejection helps builds trust and honesty with others, fosters empathy, and builds stronger bonds.
How important are vulnerability and risk assessment
Vulnerability assessment plays a critical role in defining disaster impacts in India by identifying the communities that are most at risk. It allows for the prioritization of resources and efforts to prepare for and respond to disasters, ensuring that the most vulnerable communities receive the necessary support.