Is TLS 1.2 still recommended
While TLS 1.2 can still be used, it is considered safe only when weak ciphers and algorithms are removed. On the other hand, TLS 1.3 is new; it supports modern encryption, comes with no known vulnerabilities, and also improves performance.
Why use TLS 1.2 when TLS 2.0 is the standard
Why use TLS 1.2 with Configuration Manager TLS 1.2 is more secure than the previous cryptographic protocols such as SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1. Essentially, TLS 1.2 keeps data being transferred across the network more secure.
Why TLS 1.3 is not used
TLS 1.3 mandates the use of specific ciphers, which can take a toll on the server side. SSL offload on application delivery controllers (ADCs) and decryption on servers would require costly hardware upgrades and administrative overhead. TLS 1.2 is still relevant and has not yet been compromised.
Why is TLS 1.0 bad
TLS 1.0 was released in 1999, making it a nearly two-decade-old protocol. It has been known to be vulnerable to attacks—such as BEAST and POODLE—for years, in addition to supporting weak cryptography, which doesn't keep modern-day connections sufficiently secure.
Why is TLS 1.2 not secure
In TLS 1.2 and earlier versions, the use of ciphers with cryptographic weaknesses had posed potential security vulnerabilities. TLS 1.3 includes support only for algorithms that currently have no known vulnerabilities, including any that do not support Perfect Forward Secrecy (PFS).
Why is TLS 1.3 better
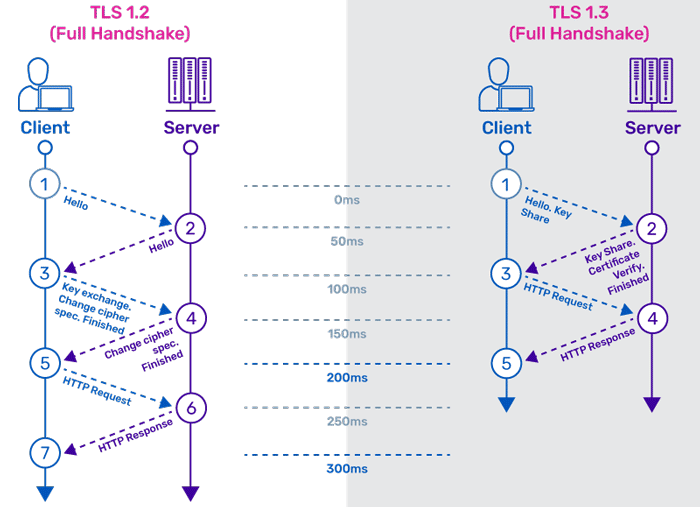
In a nutshell, TLS 1.3 is faster and more secure than TLS 1.2. One of the changes that makes TLS 1.3 faster is an update to the way a TLS handshake works: TLS handshakes in TLS 1.3 only require one round trip (or back-and-forth communication) instead of two, shortening the process by a few milliseconds.
Why are TLS v1 0 and v1 1 no longer recommended
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Is TLS 1.3 vulnerable
This vulnerability allows a remote unauthenticated attacker to cause a denial-of-service (DoS) on the BIG-IP system. There is no control plane exposure; this is a data plane issue only. Note: TLS 1.3 is disabled by default. This vulnerability affects only configurations where TLS 1.3 has been explicitly enabled.
Does TLS 2.0 exist
The history of TLS
SSL 1.0 was never released because it contained serious vulnerabilities. Version 2.0 came out with Netscape Navigator 1.1 in 1995, however it still contained a number of serious flaws. SSL 3.0 was a heavily redesigned version and came out in 1996, with many of the security issues resolved.
Why SSL is less secure than TLS
SSL Certificate
Compared to SSLs, TLS is a simpler protocol. SSL is a more complex protocol than TLS to implement. Whereas SSL has three versions, of which SSL 3.0 is the latest. TLS protocol offers higher security than SSL.
When did TLS 1.1 become deprecated
March 2021
TLS 1.0 and 1.1 were formally deprecated in RFC 8996 in March 2021.
When did TLS 1.0 become deprecated
As part of ongoing efforts to modernize platforms, and to improve security and reliability, TLS 1.0 and 1.1 have been deprecated by the Internet Engineering Task Force (IETF) as of March 25, 2021.
Why is TLS 1.1 insecure
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Is TLS 1.3 widely used
Transport Layer Security (TLS) is a widely used protocol for securing internet communications. It has undergone several revisions over the years, with TLS 1.2 and 1.3 being the most widely used versions today.
Is TLS 1.3 out yet
The most recent, TLS 1.3, was released in August 2018. The differences between TLS 1.2 and 1.3 are extensive and significant, offering improvements in both performance and security.
Is TLS 1.1 outdated
TLS 1.0 and 1.1 were deprecated in Mar 2021 with IETF RFC 8996. Today, the baseline TLS version used by most enterprises and businesses is 1.2. Many organizations, particularly those in highly regulated verticals and government agencies, also have to meet their respective compliance requirements.
Why is SSL no longer used
Is SSL still up to date SSL has not been updated since SSL 3.0 in 1996 and is now considered to be deprecated. There are several known vulnerabilities in the SSL protocol, and security experts recommend discontinuing its use. In fact, most modern web browsers no longer support SSL at all.
Is TLS 1.2 deprecated
TLS 1.0 and 1.1 were deprecated by IETF in RFC 8996 datatracker.ietf.org/doc/rfc8996 in March 2021. AFAIK there is no plan to deprecate TLS 1.2 yet but a bunch of the ciphersuites it supports are deprecated.
Is TLS 1.0 outdated
As of October 31, 2018, the Transport Layer Security (TLS) 1.0 and 1.1 protocols are deprecated for the Microsoft 365 service. The effect for end-users is minimal. This change has been publicized for over two years, with the first public announcement made in December 2017.
Has TLS 1.2 been deprecated
All TLS versions were further refined in RFC 6176 in March 2011, removing their backward compatibility with SSL such that TLS sessions never negotiate the use of Secure Sockets Layer (SSL) version 2.0. There is currently no formal date for TLS 1.2 to be deprecated.
Why SSL 3.0 is not provided
It was not limited to one or two types of machines, but all websites and Windows Virtual machines got vulnerable. To ensure the safety of the users, Microsoft completely disabled SSL 3.0 in Azure Websites by default to protect customers from the vulnerability.
Why isn’t SSL 3.0 provide
We have a plan to turn off SSLv3 in Firefox. This plan was developed with other browser vendors after a team at Google discovered a critical flaw in SSLv3, which can allow an attacker to extract secret information from inside of an encrypted transaction.
Can TLS 1.2 Be Hacked
What Is the Raccoon Attack The Raccoon attack is a newly discovered vulnerability in TLS 1.2 and earlier versions. It allows hackers (in certain situations) to determine a shared session key and use that to decrypt TLS communications between the server and client.
When did TLS 1.0 become vulnerable
The web server supports encryption through TLS 1.0, which was formally deprecated in March 2021 as a result of inherent security issues. In addition, TLS 1.0 is not considered to be "strong cryptography" as defined and required by the PCI Data Security Standard 3.2(.
Should TLS 1.2 be disabled
While TLS 1.0 & TLS 1.1 are known to be very vulnerable, the TLS 1.2 protocol is considered to be much more secure and is thus recommended for use.