Why TLS 1.3 is not used
TLS 1.3 mandates the use of specific ciphers, which can take a toll on the server side. SSL offload on application delivery controllers (ADCs) and decryption on servers would require costly hardware upgrades and administrative overhead. TLS 1.2 is still relevant and has not yet been compromised.
Is TLS 1.3 widely used
Transport Layer Security (TLS) is a widely used protocol for securing internet communications. It has undergone several revisions over the years, with TLS 1.2 and 1.3 being the most widely used versions today.
Is TLS 1.3 vulnerable
Many of the major vulnerabilities in TLS 1.2 had to do with older cryptographic algorithms that were still supported. TLS 1.3 drops support for these vulnerable cryptographic algorithms, and as a result it is less vulnerable to cyber attacks.
Is TLS 1.2 or 1.3 better
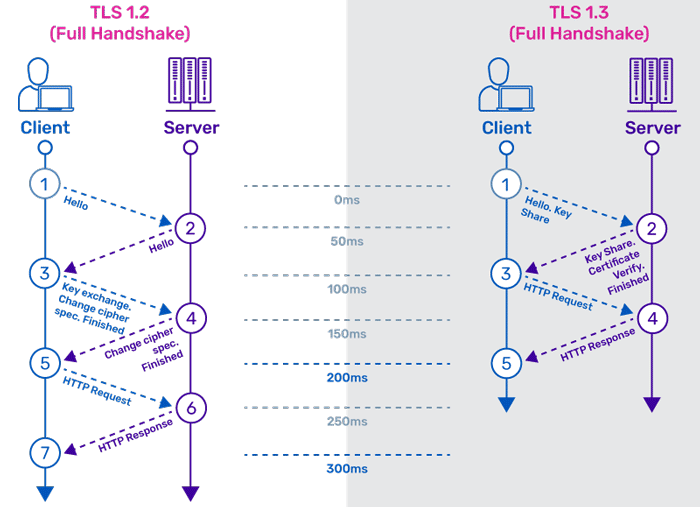
While TLS 1.2 can still be used, it is considered safe only when weak ciphers and algorithms are removed. On the other hand, TLS 1.3 is new; it supports modern encryption, comes with no known vulnerabilities, and also improves performance.
Should TLS 1.3 be disabled
However, if some apps you are using in Windows 10 do not support TLS 1.3, the apps possibly do not work properly by TLS 1.3 is enabled, and you should disable TLS 1.3 in Windows 10.
Why is TLS 1.0 weak
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Why are TLS v1 0 and v1 1 no longer recommended
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Why is TLS 1.2 needed
TLS 1.2 is more secure than the previous cryptographic protocols such as SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1. Essentially, TLS 1.2 keeps data being transferred across the network more secure.
Which version of TLS is unsafe
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Is TLS 1.2 outdated
TLS 1.2 version has been in use by most website owners because of its excellent security features and unparalleled speed. However, more and more companies are now switching to TLS 1.3 for improved performance and better security.
Does TLS 1.3 use AES 256
Every implementation of TLS 1.3 is required to implement AES-128-GCM-SHA256, with AES-256-GCM-SHA384 and CHACHA20-Poly1305-SHA256 encouraged.
Is it recommended to disable TLS 1.1 and replace it with TLS 1.2 or higher
TLS 1.0 and TLS 1.1 are no longer considered secure, due to the fact that they are vulnerable to various attacks, such as the POODLE attack. Disabling TLS 1.0 and TLS 1.1 on your server will force clients to use a more secure protocol (TLS 1.2), which is less vulnerable to attack.
Why is TLS 1.2 not secure
In TLS 1.2 and earlier versions, the use of ciphers with cryptographic weaknesses had posed potential security vulnerabilities. TLS 1.3 includes support only for algorithms that currently have no known vulnerabilities, including any that do not support Perfect Forward Secrecy (PFS).
Why is TLS 1.1 bad
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Why was TLS 1.0 deprecated
There are also real security risks of using TLS 1.0 or 1.1 in any IT infrastructure or solutions. Well-known attacks like BEAST (Browser Exploit Against SSL/TLS), POODLE (Padding Oracle On Downgraded Legacy Encryption), etc.
Why is TLS 1.0 bad
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Which TLS versions are weak
Your organization should avoid TLS versions 1.1 and below and RC4 encryption, as there have been multiple vulnerabilities discovered that render it insecure. The best way to ensure strong transport layer security is to support TLS 1.3, which is the most secure and up-to-date version of TLS.
Which TLS version is outdated
Using outdated TLS versions would force organizations to use outdated, vulnerable cipher suites and not support newer recommended cipher suits. TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages.
Which version of TLS is weak
Your organization should avoid TLS versions 1.1 and below and RC4 encryption, as there have been multiple vulnerabilities discovered that render it insecure. The best way to ensure strong transport layer security is to support TLS 1.3, which is the most secure and up-to-date version of TLS.
Why is 256-bit AES so secure
The three types of AES also vary by the number of rounds of encryption. AES-128 uses 10 rounds, AES-192 uses 12 rounds, and AES-256 uses 14 rounds. The more rounds there are, the safer the encryption. This is why AES-256 is considered the safest encryption there is.
Does TLS 1.3 use AES
TLS 1.3 eliminates many of the features that are vulnerable to attacks, such as CBC mode, compression, and MAC verification. It also uses only secure cipher suites, such as AES-GCM, which combines encryption and authentication in one operation.
Why is TLS 1.0 and 1.1 bad
TLS 1.0 and 1.1 are vulnerable to downgrade attacks since they rely on SHA-1 hash for the integrity of exchanged messages. Even authentication of handshakes is done based on SHA-1, which makes it easier for an attacker to impersonate a server for MITM attacks.
Why use TLS 1.2 when TLS 2.0 is the standard
Why use TLS 1.2 with Configuration Manager TLS 1.2 is more secure than the previous cryptographic protocols such as SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1. Essentially, TLS 1.2 keeps data being transferred across the network more secure.
Which version of TLS is vulnerable
While TLS 1.0 & TLS 1.1 are known to be very vulnerable, the TLS 1.2 protocol is considered to be much more secure and is thus recommended for use.
Which TLS versions are insecure
SSL version 1 and 2, SSLv2 and SSLv3 are now insecure. It is also recommended to phase out TLS 1.0 and TLS 1.1. We recommend that you disable SSLv2, SSLv3, TLS 1.0 and TLS 1.1 in your server configuration so that only the newer TLS protocols can be used. It is recommended to only enable TLS 1.3 for maximum security.