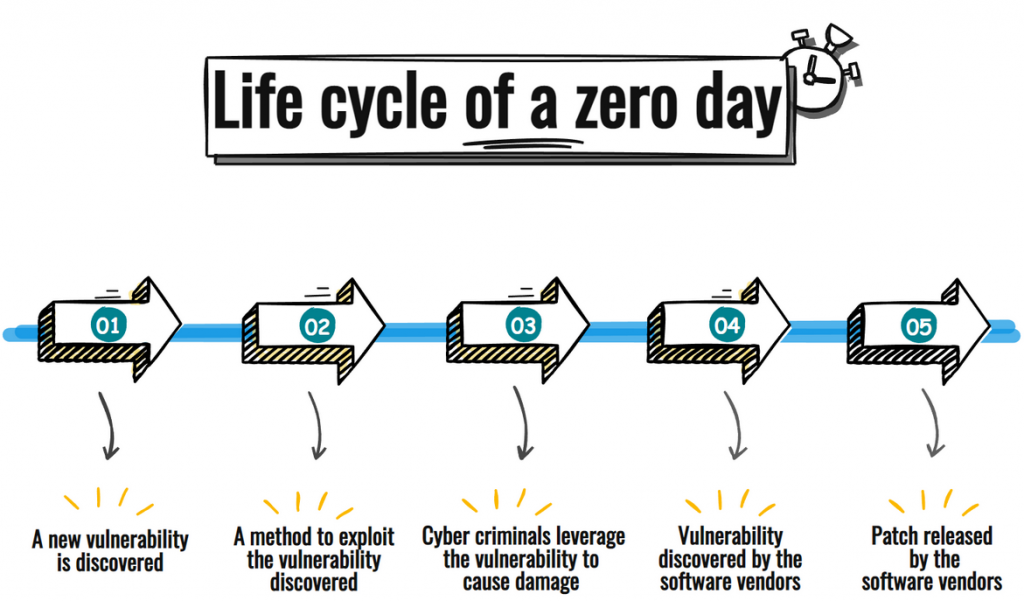
What causes zero-day vulnerability
A zero-day attack occurs when bad actors use a known exploit to target a vulnerable system to damage its operation or steal privileged information.
Why is zero-day malware a strong weapon for hackers
A zero-day (or 0-day) attack is a software vulnerability exploited by attackers before the vendor has become aware of it. At that point, no patch exists, so attackers can easily exploit the vulnerability knowing that no defenses are in place. This makes zero-day vulnerabilities a severe security threat.
Why are zero-day vulnerabilities so difficult to defend against
A zero-day (or 0-day) vulnerability is a software vulnerability that is discovered by attackers before the vendor has become aware of it. By definition, no patch exists for zero day vulnerabilities and user systems have no defenses in place, making attacks highly likely to succeed.
Is zero-day a vulnerability
A zero-day vulnerability is a vulnerability in a system or device that has been disclosed but is not yet patched. An exploit that attacks a zero-day vulnerability is called a zero-day exploit.
How do hackers find zero-day vulnerability
In most cases, hackers use code to exploit zero-day. Sometimes it is discovered by an individual when the program behaves suspiciously, or the developer himself may recognize the vulnerability. Attackers have found a new route by exploiting a zero-day vulnerability in Google's Android mobile operating system.
How we can defend zero-day vulnerability
Vulnerability scanning: Regular scanning is a primary technique for cybersecurity teams to identify security flaws in the software code of applications. Monitoring activities: We can prevent systems from zero-day attacks by monitoring the network and checking unexpected traffic.
Why is it called zero-day exploit
The term “Zero-Day” is used when security teams are unaware of their software vulnerability, and they've had “0” days to work on a security patch or an update to fix the issue. “Zero-Day” is commonly associated with the terms Vulnerability, Exploit, and Threat.
Do most attackers use zero-day attacks
Zero-day attacks consist of almost 80% of all malware attacks. Take a look at some recent attacks and learn how to prevent them.
Can zero-day exploit be prevented
One of the most effective ways to prevent zero-day attacks is deploying a web application firewall (WAF) on the network edge. A WAF reviews all incoming traffic and filters out malicious inputs that might target security vulnerabilities.
What is the difference between zero-day and vulnerability
“Zero-Day” Definition
It is important to understand the difference: A Zero-Day Vulnerability is an unknown security vulnerability or software flaw that a threat actor can target with malicious code. A Zero-Day Exploit is the technique or tactic a malicious actor uses to leverage the vulnerability to attack a system.
What is a real life example of zero-day vulnerability
Via zero-day exploits, an APT can gain access to a large number of computing systems at high profile organizations. A prominent example was the SolarWinds supply chain attack, in which an organized cybercrime group exploited a zero-day vulnerability to breach to US government agencies and a majority of the Fortune 500.
Can zero-day attacks be stopped
Preventing zero day attacks is a multistage process. Organizations need the threat intelligence required to identify a potential campaign, tools for acting on this intelligence, and a unified platform that supports rapid, coordinated threat response. Modern cyberattacks are widespread and automated.
How are zero-day exploits found
In most cases, hackers use code to exploit zero-day. Sometimes it is discovered by an individual when the program behaves suspiciously, or the developer himself may recognize the vulnerability.
What is zero-day based on
columbine high school massacre
zero day is based of columbine high school massacre. and its a video diary of two boys.
How common are zero-day attacks
According to the Ponemon Institute, 80% of successful breaches were Zero-Day attacks.
What is the solution to avoid zero-day exploit
The more software you have, the more potential vulnerabilities you have. You can reduce the risk to your network by using only the applications you need. Use a firewall. A firewall plays an essential role in protecting your system against zero-day threats.
How are zero-day vulnerabilities exploited
A zero-day (0day) exploit is a cyber attack targeting a software vulnerability which is unknown to the software vendor or to antivirus vendors. The attacker spots the software vulnerability before any parties interested in mitigating it, quickly creates an exploit, and uses it for an attack.
How do you protect against zero-day exploits
Best Practices for Zero-Day Attack PreventionMonitor Reported Vulnerabilities.Install Next-Gen Antivirus Solutions (NGAV)Perform Rigorous Patch Management.Install a Robust Web Application Firewall.Practice the Principle of Least Privilege.
What are the 7 ways to help prevent zero day attacks
For best results, zero-day attack prevention steps you should take include the following:Monitor Reported Vulnerabilities.Install Next-Gen Antivirus Solutions (NGAV)Perform Rigorous Patch Management.Install a Robust Web Application Firewall.Practice the Principle of Least Privilege.
Why is it called zero-day
The term “Zero-Day” is used when security teams are unaware of their software vulnerability, and they've had “0” days to work on a security patch or an update to fix the issue. “Zero-Day” is commonly associated with the terms Vulnerability, Exploit, and Threat.
What is the most famous zero-day exploit
Stuxnet, dubbed as “Operation Olympic Games” was the world's first digital weapon, which was created to target the Iranian nuclear program; it leveraged zero-day exploits to infect Windows machines. The malicious computer worm was a product of the concerted efforts of NSA, the CIA, and Israeli intelligence.
Why is it called a zero-day exploit
The term “Zero-Day” is used when security teams are unaware of their software vulnerability, and they've had “0” days to work on a security patch or an update to fix the issue. “Zero-Day” is commonly associated with the terms Vulnerability, Exploit, and Threat.
What is an example of a zero-day vulnerability
The locker has a 8 digit login that only you know so your information is very secure. Imagine that an offender figures out that hammering the locker in a certain way can break it open. You come to know about this flaw but as yet you do not have a fix for this. It is an example of zero day vulnerability.
What is the best example of a zero-day exploit
Via zero-day exploits, an APT can gain access to a large number of computing systems at high profile organizations. A prominent example was the SolarWinds supply chain attack, in which an organized cybercrime group exploited a zero-day vulnerability to breach to US government agencies and a majority of the Fortune 500.
What is the difference between zero-day and one day vulnerability
Zero-day exploit refers to the method or technique hackers use to take advantage of a vulnerability — often via malware — and execute the attack. Once a zero-day vulnerability has been made public, it is known as an n-day or one-day vulnerability.