Is CVSS the same as CVE
Differences between CVSS and CVE
CVSS is the overall score assigned to a vulnerability. CVE is simply a list of all publicly disclosed vulnerabilities that includes the CVE ID, a description, dates, and comments. The CVSS score is not reported in the CVE listing – you must use the NVD to find assigned CVSS scores.
What is CVE and CVSS
CVE stands for Common Vulnerabilities and Exposures. CVE is a glossary that classifies vulnerabilities. The glossary analyzes vulnerabilities and then uses the Common Vulnerability Scoring System (CVSS) to evaluate the threat level of a vulnerability.
What is the difference between CWE and CVSS
Common Weakness Scoring System (CWSS) is a framework that documents software weaknesses so developers can minimize the number of bugs and vulnerabilities they introduce in a live system. The biggest difference between scoring systems is that the CWSS is proactive, whereas the CVSS is reactive.
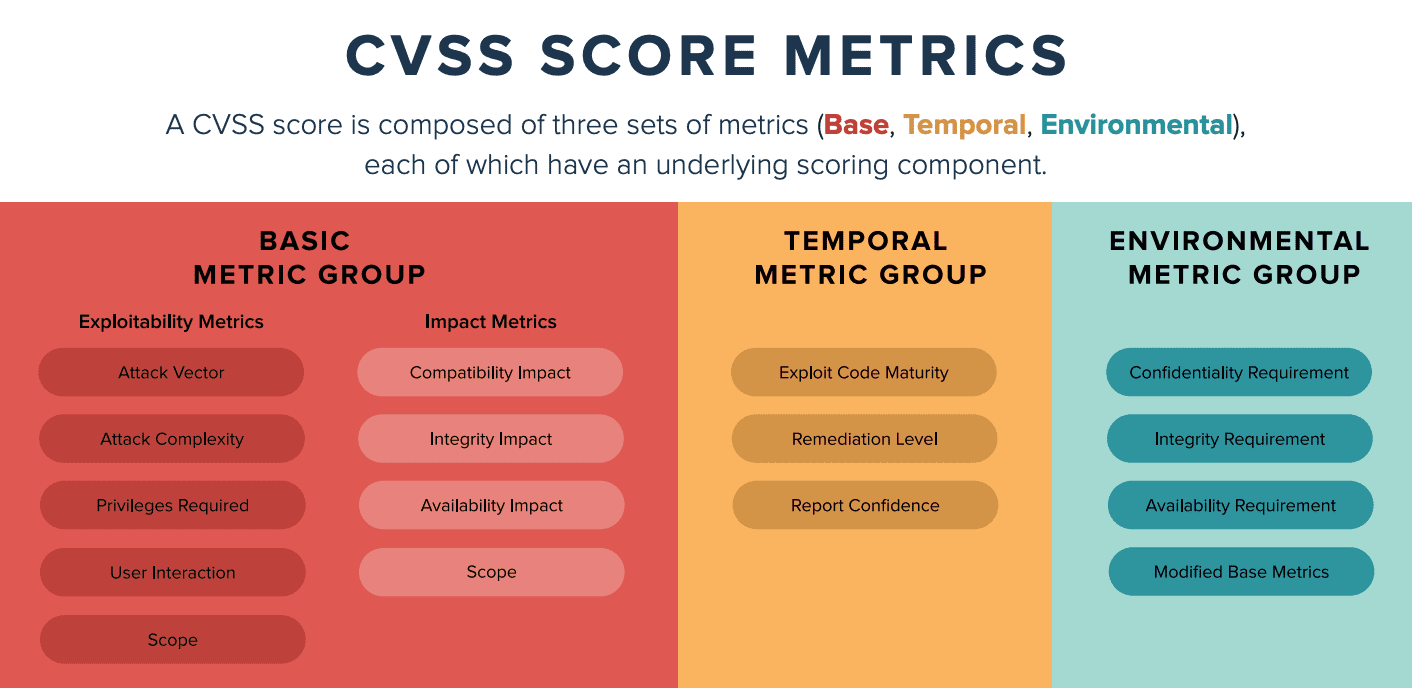
What is the difference between CVE base score and temporal score
Base Metrics do not change over time – they remain the same throughout the lifetime of a vulnerability. Temporal Metrics, on the other hand, change over time as a result of activities conducted by both software vendors and hackers. Temporal metrics are sometimes, but not always, reported in the NVD.
What is CWE vs CVE
Whereas the CVE logs real-world instances of vulnerabilities and exposures in specific products, the CWE lists and defines weaknesses commonly seen in digital products. The CWE does not refer to one particular example but provides definitions for widely seen defects.
Does every vulnerability have a CVE
In simple terms, we can state that 'All CVEs are vulnerabilities, but not all vulnerabilities have CVEs.
Does CVE mean vulnerability
Common Vulnerabilities and Exposures
CVE stands for Common Vulnerabilities and Exposures. The system provides a method for publicly sharing information on cybersecurity vulnerabilities and exposures. What is the Difference Between CVE and CVSS CVE is the database of known vulnerabilities and exposures.
What does CVE mean
common vulnerabilities and exposures
common vulnerabilities and exposures (CVE)
Is CWE based on CVE
CWE also includes mappings to other vulnerability databases, such as CVE. CVEs refer to the actual vulnerabilities, while CWEs refer to the underlying weaknesses that can lead to those vulnerabilities.
What is CWE or CVE score
While both standards play a critical role in secure software development, they have different purposes. In summary, CVE is a standard for identifying and naming specific vulnerabilities, while CWE is a standard for classifying and describing the types of weaknesses that can lead to vulnerabilities.
What is CVE temporal score
The temporal score represents vulnerability urgency at specific points in time. Environmental Scoring is optionally computed by end-user organizations and adjusts combined Base-Temporal score. This should be considered the FINAL score and represents a snapshot in time, tailored to a specific environment.
What is CCE vs CVE
CVE provides this capability for information security vulnerabilities, CCE assigns a unique, common identifier to a particular security-related configuration issue. The name of the imported file. The type of the list, that is, if it is a CVE or CCE list.
Who creates a CVE for vulnerability
The Mitre Corporation
CVEs are assigned by a CVE Numbering Authority (CNA). While some vendors acted as a CNA before, the name and designation was not created until February 1, 2005. there are three primary types of CVE number assignments: The Mitre Corporation functions as Editor and Primary CNA.
What type of vulnerability is CVE
CVE, short for Common Vulnerabilities and Exposures, is a list of publicly disclosed computer security flaws. When someone refers to a CVE, they mean a security flaw that's been assigned a CVE ID number. Security advisories issued by vendors and researchers almost always mention at least one CVE ID.
Do all vulnerabilities have a CVE
CVE stands for Common Vulnerabilities and Exposures. It is the database of publicly disclosed information on security issues. All organizations use CVEs to identify and track the number of vulnerabilities. But not all the vulnerabilities discovered have a CVE number.
Do hackers use CVE
Can Hackers Use CVE to Attack My Organization The short answer is yes but many cybersecurity professionals believe the benefits of CVE outweigh the risks: CVE is restricted to publicly known vulnerabilities and exposures.
What is CVSS in cybersecurity
The Common Vulnerability Scoring System (CVSS) is a public framework for rating the severity of security vulnerabilities in software.
What is CVE and CWE in security
In other words, CVE is a list of known instances of vulnerability for specific products or systems, while CWE acts as a dictionary (so to speak) of software vulnerability types. The National Vulnerability Database (NVD) actually uses CWEs to score CVEs.
How is CVE score calculated
CVSS scores are calculated using a formula consisting of vulnerability-based metrics. A CVSS score is derived from scores in these three groups: Base, Temporal and Environmental. Scores range from zero to 10, with zero representing the least severe and 10 representing the most severe.
What are the 4 types of vulnerability
Students will consider four principal vulnerability factors, namely: physical; social; economic; and environmental. Students will also learn the difference between hazard vulnerability and hazard exposure.
What is CVSS score for vulnerability
NVD Vulnerability Severity Ratings
| CVSS v2.0 Ratings | CVSS v3.0 Ratings | |
|---|---|---|
| Severity | Base Score Range | Base Score Range |
| Low | 0.0-3.9 | 0.1-3.9 |
| Medium | 4.0-6.9 | 4.0-6.9 |
| High | 7.0-10.0 | 7.0-8.9 |
Is CVSS a threat model
There are eight main methodologies you can use while threat modeling: STRIDE, PASTA, VAST, Trike, CVSS, Attack Trees, Security Cards, and hTMM. Each of these methodologies provides a different way to assess the threats facing your IT assets.
What does a CVE score of 10 mean
CVSS attempts to assign severity scores to vulnerabilities, allowing responders to prioritize responses and resources according to threat. Scores are calculated based on a formula that depends on several metrics that approximate ease and impact of an exploit. Scores range from 0 to 10, with 10 being the most severe.
What are the 5 categories of vulnerability
One classification scheme for identifying vulnerability in subjects identifies five different types-cognitive or communicative, institutional or deferential, medical, economic, and social. Each of these types of vulnerability requires somewhat different protective measures.
Which are the 4 key drivers of vulnerability
4 key drivers of customer vulnerabilityHealth. Conditions or illnesses that affect one's ability to complete day-to-day tasks, both mentally and physically.Life Events. Such as bereavement, job loss or relationship breakdown.Resilience. Low ability to withstand and manage financial or emotional shocks.Capability.