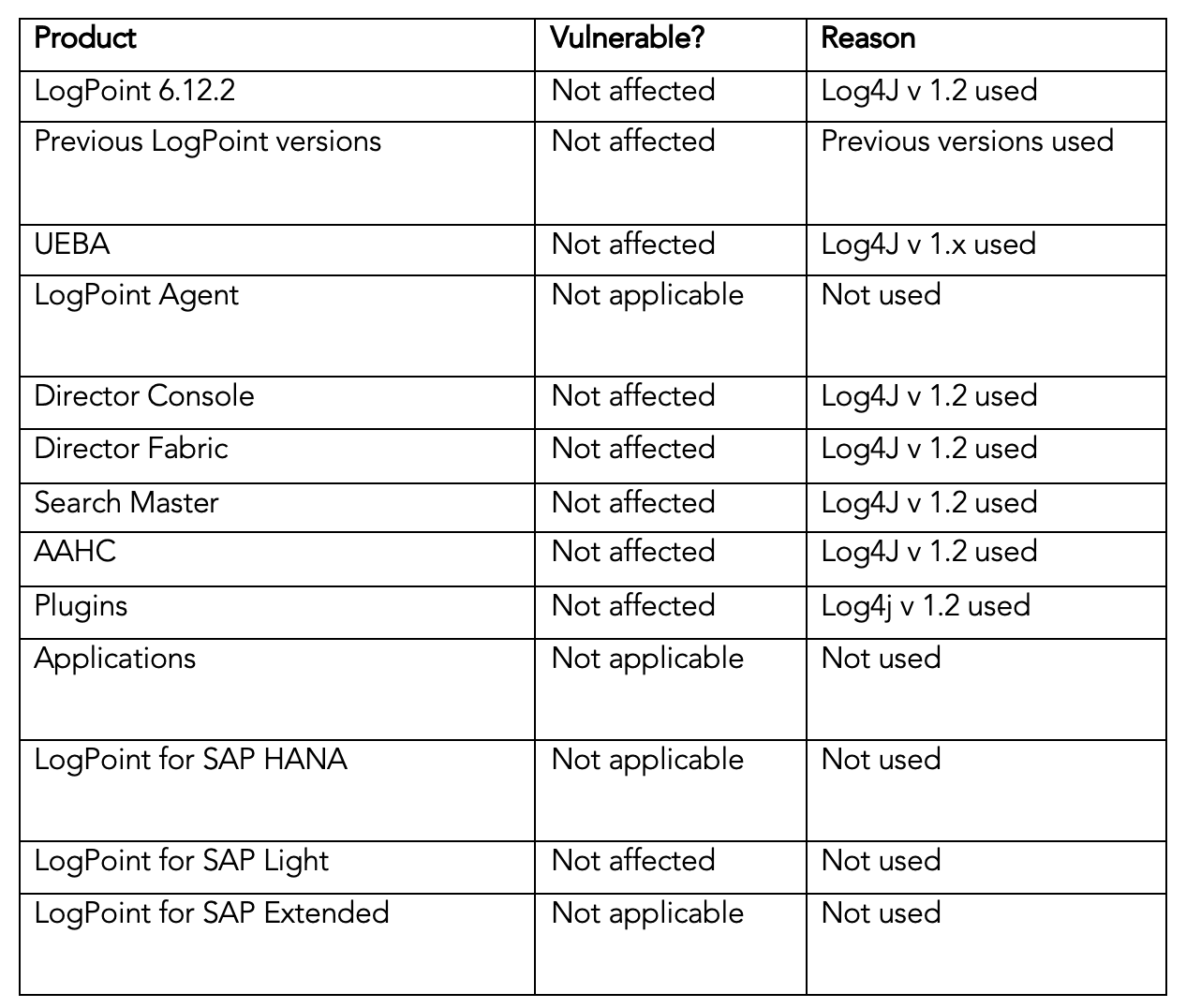
What is the vulnerability of Log4j 1.2 13
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data.
What is the vulnerability of Log4j 1.2 jar
JMSAppender, in log4j 1.2 version, is vulnerable to deserialization of untrusted data if the attacker has the 'write' permissions to the log4j configuration.
Which version of Log4j is vulnerable
Technical Details. The CVE-2021-44228 RCE vulnerability—affecting Apache's Log4j library, versions 2.0-beta9 to 2.14. 1—exists in the action the Java Naming and Directory Interface (JNDI) takes to resolve variables.
Is Log4j v1 vulnerable
Applications using Log4j 1.x are only vulnerable to this attack when they use JNDI in their configuration. A separate CVE (CVE-2021-4104) has been filed for this vulnerability. To mitigate: Audit your logging configuration to ensure it has no JMSAppender configured.
Is Log4j 1.2 end of life
Apache Log4j 1.2 reached end of life in August 2015. Users should upgrade to Log4j 2 as it addresses numerous other issues from the previous versions. CSM version 6.3.
Does Log4j 1.2 14 have vulnerability
Affected versions of this package are vulnerable to Deserialization of Untrusted Data. JMSSink in all versions of Log4j 1. x is vulnerable to deserialization of untrusted data when the attacker has write access to the Log4j configuration or if the configuration references an LDAP service the attacker has access to.
Is Log4j Version 1.2 14 vulnerable
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data.
Which Log4j version is stable
2.20.0
Log4j
| Developer(s) | Apache Software Foundation |
|---|---|
| Initial release | January 8, 2001 |
| Stable release | 2.20.0 / 21 February 2023 |
| Repository | github.com/apache/logging-log4j2 |
| Written in | Java |
How do I know if I am vulnerable to log4j
We also use a log inspection rule to detect the vulnerability. The log inspection rule 1011241 – Apache Log4j Remote Code Execution Vulnerability (CVE-2021-44228) looks for JNDI payloads in the access logs, with the default path being /var/log/*/access. log.
How do I know what version of log4j I have
Check the log4j library version in your project's dependencies: If you are using a build tool such as Maven or Gradle, you can check the version of the log4j library in your project's dependencies. The version should be specified in the build file (pom. xml for Maven and build. gradle for Gradle) for the project.
What is the replacement for Log4j 1.2 17
Initiated by Ceki Gülcü, the original author of Apache log4j 1. x, the reload4j project is a fork of Apache log4j version 1.2. 17 with the goal of fixing pressing security issues. Reload4j is a binary compatible, drop-in replacement for log4j version 1.2.
What is the version Log4j 1.2 17
Apache Log4j » 1.2. 17
| License | Apache 2.0 |
|---|---|
| Files | pom (21 KB) bundle (478 KB) View All |
| Repositories | CentralApache PublicApache ReleasesApache StagingBeDataDrivenHortonworksMulesoftOrekitRedhat GASonatypeSpring Plugins |
| Ranking | #16 in MvnRepository (See Top Artifacts) #3 in Logging Frameworks |
| Used By | 18,289 artifacts |
Is Log4j 1.2 17 jar affected
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data. This affects Log4j versions up to 1.2 up to 1.2. 17.
How do I know which version of Log4j is being used
Check the log4j library version in your project's dependencies: If you are using a build tool such as Maven or Gradle, you can check the version of the log4j library in your project's dependencies. The version should be specified in the build file (pom. xml for Maven and build. gradle for Gradle) for the project.
Is Log4j still vulnerable
With 40% of Log4j Downloads Still Vulnerable, Security Retrofitting Needs to Be a Full-Time Job. Vulnerabilities like Log4j remain responsible for security breaches a full year after the discovery of the flaw.
What is the vulnerability of Log4j 1.2 17
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data.
How do I know if I am vulnerable to Log4j
We also use a log inspection rule to detect the vulnerability. The log inspection rule 1011241 – Apache Log4j Remote Code Execution Vulnerability (CVE-2021-44228) looks for JNDI payloads in the access logs, with the default path being /var/log/*/access. log.
What replaces Log4j 1.2 17 jar
By drop-in, we mean that you can replace log4j. jar with reload4j. jar in your build with no source code changes, no recompilation, nor rebuild being necessary. The reload4j project offers a clear and easy migration path for the thousands of users who have an urgent need to fix vulnerabilities in log4j 1.2.
Is log4j 1.2 end of life
Apache Log4j 1.2 reached end of life in August 2015. Users should upgrade to Log4j 2 as it addresses numerous other issues from the previous versions. CSM version 6.3.
What replaces log4j 1.2 17 jar
By drop-in, we mean that you can replace log4j. jar with reload4j. jar in your build with no source code changes, no recompilation, nor rebuild being necessary. The reload4j project offers a clear and easy migration path for the thousands of users who have an urgent need to fix vulnerabilities in log4j 1.2.
Is Log4j 2.17 1 safe
1 can probably wait. A number of security professionals say that the latest vulnerability in Apache Log4j, disclosed on Tuesday, does not pose an increased security risk for the majority of organizations. As a result, for many organizations that have already patched to version 2.17.
Is log4j Version 1.2 14 vulnerable
Included in Log4j 1.2 is a SocketServer class that is vulnerable to deserialization of untrusted data which can be exploited to remotely execute arbitrary code when combined with a deserialization gadget when listening to untrusted network traffic for log data.
What is the release date of log4j 1.2 17
Release History
| Version | Date | Description |
|---|---|---|
| 1.2.17 | 2012-05-06 | Maintenance release |
| 1.2.16 | 2010-04-06 | Maintenance release |
| 1.2.15 | 2007-08-24 | SyslogAppender enhancements, NTEventLogAppender and Maven build. |
| 1.2.14 | 2006-09-18 | AsyncAppender rewrite, Syslog and SMTPAppender enhancements. |
Is 1.18 1 safe from Log4j
Is My Server Safe All servers running 1.18. 1 and above are completely safe.
What is the vulnerability of Log4j 1.2 14
Affected versions of this package are vulnerable to Man-in-the-Middle (MitM). Improper validation of certificate with host mismatch in Apache Log4j SMTP appender. This could allow an SMTPS connection to be intercepted by a man-in-the-middle attack which could leak any log messages sent through that appender.


