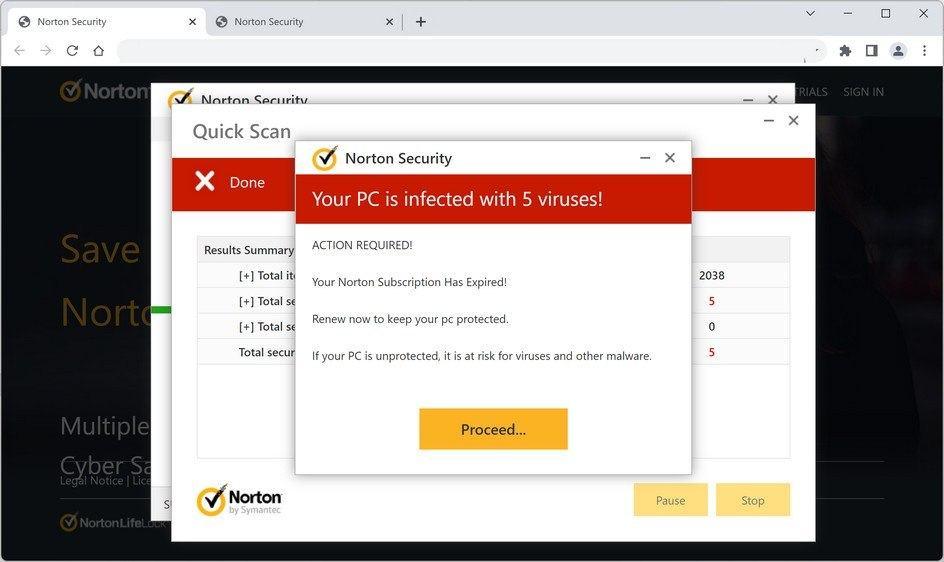
Can Trojans be fake
Fake antivirus Trojans
A dangerous type of scareware, fake AV Trojans pretend to detect viruses and other malware on your device, then urge you to pay for security software — which is either useless or actively malicious.
Can a Trojan virus be disguised as a genuine piece of software
A Trojan Horse Virus is a type of malware that downloads onto a computer disguised as a legitimate program. The delivery method typically sees an attacker use social engineering to hide malicious code within legitimate software to try and gain users' system access with their software.
Is Trojan virus real
One form of Trojan malware has targeted Android devices specifically. Called Switcher Trojan, it infects users' devices to attack the routers on their wireless networks. The result Cybercriminals could redirect traffic on the Wi-Fi-connected devices and use it to commit various crimes.
Does Trojan virus still exist
Trojans now not only target Windows computers, but also Mac computers and mobile devices. Accordingly, you should never feel too safe or be on the internet without up-to-date anti-malware protection such as Kaspersky Internet Security.
Is Trojan virus easy to detect
Running a malware scanner is the best way to detect and remove the trojan horse from the computer. Just look for a trusted and effective malware scanner software online. There are different malware scanners available for download, but choose the one that can protect your computer from advanced types of malware.
Can Trojans be harmless
They disguise themselves as harmless until installed and implemented into your system. Just like the myth, the nature of Trojans is to lie in wait to attack. You can get rid of Trojans by using an antivirus suite, specialist tools, or resetting and restoring your system.
Can Trojan virus be harmless
It makes up approximately 51.45 percent of all malware,1 which comes as no surprise, given the unique traits of a Trojan. To infiltrate a device, a Trojan presents itself as legitimate software, but hidden beneath its seemingly harmless exterior are malicious codes that can damage your devices.
Can a Trojan virus record you
Cybercriminals can use so-called Trojan horse malware. You click on an attachment or download a piece of music or video infected with malware, and hey presto! – A cybercriminal can remotely control your PC's functions – including your camera and microphone and may even be able to record images and audio remotely.
Is the Trojan horse fake
But was it just a myth Probably, says Oxford University classicist Dr Armand D'Angour: 'Archaeological evidence shows that Troy was indeed burned down; but the wooden horse is an imaginative fable, perhaps inspired by the way ancient siege-engines were clothed with damp horse-hides to stop them being set alight.
Can a Trojan virus track you
It then loads itself onto your device to spy on and track your activity, location, usernames, and passwords. Trojan horse: A trojan horse on your cell phone may appear as a text message. From there, trojans will send messages at a premium, often increasing your phone bill.
Is Trojan virus hard to remove
Can Trojan viruses be removed Trojan viruses can be removed in various ways. If you know which software contains the malware, you can simply uninstall it. However, the most effective way to remove all traces of a Trojan virus is to install antivirus software capable of detecting and removing Trojans.
Can Trojan infect your WIFI
A trojan attack tricks you into downloading malware hiding a virus that then tramples all over your phone, tablet, or computer. A router virus can ride inside a trojan, waiting to sniff out vulnerable public or home Wi-Fi networks to infect.
Do Trojan viruses steal passwords
There are a variety of types of Trojans, many of which can launch sophisticated and clever attacks. Here are some types to be aware of: Password-stealing Trojans—These look for saved passwords on your computer and email them to the hackers. Some can even steal passwords cached in your browser history.
Can a Trojan virus be removed
You can remove some Trojans by disabling startup items on your computer which don't come from trusted sources. For the best results, first reboot your device into safe mode so that the virus can't stop you from removing it.
Should you delete Trojan virus
If you find a Trojan, whether it's masquerading as a legitimate program, hiding as a startup program, or operating as a background process, the next step is to remove it.
Can a Trojan steal my passwords
There are a variety of types of Trojans, many of which can launch sophisticated and clever attacks. Here are some types to be aware of: Password-stealing Trojans—These look for saved passwords on your computer and email them to the hackers. Some can even steal passwords cached in your browser history.
Is Trojan a myth
Whether there is any historical reality behind the Trojan War remains an open question. Many scholars believe that there is a historical core to the tale, though this may simply mean that the Homeric stories are a fusion of various tales of sieges and expeditions by Mycenaean Greeks during the Bronze Age.
Was the Trojan horse a trick
The Trojan Horse is one of history's most famous tricks. The Greeks were laying siege to the city of Troy, and the war had dragged on for ten years. They built a wooden horse, which they left outside the city. The Trojans believed the horse was a peace offering and dragged it inside their city.
Should I worry about a Trojan virus
Depending on what type of Trojan horse or virus you have, intruders may have access to your personal information and may even be using your computer to attack other computers. You can stop this activity by turning off your Internet connection.
Is Trojan bad for your PC
Trojans can infect your computer and cause enormous problems before you even know what happened. Once a trojan gets onto your system, it can monitor your keyboard, install additional malware and cause a variety of other problems you simply don't want to face.
Are all Trojan files bad
That said, most Trojans are designed to take control of a user's computer, steal data, spy on users, or insert more malware on to a victim's computer. Here are some common threats that come from Trojan attacks: Backdoors, which create remote access to your system.
Is Zeus a virus or a Trojan
Since it was introduced to the internet in 2007, the Zeus malware attack (also called Zbot) has become a hugely successful trojan horse virus. Even today, the Zeus trojan and its variants are a major cybersecurity threat, and many computers that run Microsoft Windows are still at risk.
Who tricked the Trojans
According to Quintus Smyrnaeus, Odysseus thought of building a great wooden horse (the horse being the emblem of Troy), hiding an elite force inside, and fooling the Trojans into wheeling the horse into the city as a trophy. Under the leadership of Epeius, the Greeks built the wooden horse in three days.
How do we know Troy is real
Most historians now agree that ancient Troy was to be found at Hisarlik. Troy was real. Evidence of fire, and the discovery of a small number of arrowheads in the archaeological layer of Hisarlik that corresponds in date to the period of Homer's Trojan War, may even hint at warfare.
Should I delete Trojan
If you find a Trojan, whether it's masquerading as a legitimate program, hiding as a startup program, or operating as a background process, the next step is to remove it.


